Security Now 934, Transcript
Please be advised this transcript is AI-generated and may not be word for word. Time codes refer to the approximate times in the ad-supported version of the show.
Leo Laporte (00:00:00):
It's time for Security Now, Steve Gibson is here. Wither Voyager too. We've got an update on that story. You know, Steve paid a lot of attention to Amit Joran, screed against Microsoft Microsoft on Microsoft's own social network. Linkedin. What did Amit say and why? Does Steve agree coming up? Also, Bruce Schneider on the recent attack on Azure by Chinese hackers. And then we'll talk about global privacy control, how to turn it on, why you want to turn it on, and how Yahoo, Yahoo is responding. It's pretty amazing all of that coming up in a whole lot more this week on security. Now stay tuned it podcasts you love
Leo Laporte (00:00:41):
From people you trust. This is twit.
Leo Laporte (00:00:49):
This is security now with Steve Gibson, episode 934 recorded Tuesday, August 8th, 2023, revisiting Global Privacy Control. This episode of Security Now is brought to you by ACI Learning. Acis newest product Insights assists in closing, lucrative skill gaps. Visit go dot ACI learning.com/twit. Listeners will receive at least 20% off or as much as 65% off an IT Pro enterprise solution plan discount based on size of your team. And when you fill out the form, you'll get a proper quote tailored to your needs. And by thinks canary, thousands of irritating false alerts help no one get the single alert that matters. When someone's inside your network for 10% off and a 60 day money back guarantee, go to Canary tools slash twit and enter the code twit in the how did you hear about this Box? And by Duo Protect Against Breaches the leading access management suite, providing strong multi-layered defenses to only allow legitimate users in.
(00:01:57):
For any organization concerned about being breached and in need of a solution, fast Duo quickly enables strong security and improves user productivity. Visit cs.co/twin today for a free trial.
Leo Laporte (00:02:11):
It's time for security. Now. The show we cover the week security news reassure you that there is no reason to set your hair on fire with this guy right here whose hair apparently was set on fire some time ago. <Laugh>, Mr. Steve Gibson <laugh>. Hello,
Steve Gibson (00:02:25):
Steve. Now the question is, is it w e e k security or W E A K security? No, nothing weekly about the security here. Nothing weak weaklings. No weaklings. No weaklings. Okay. So today's topic, we are going to revisit something that we talked about a little over a year ago in May of 2022. And I didn't plan this, but when I went to TechCrunch, the it, something happened.
(00:02:57):
And so I thought, whoa, what? Wait. so today's topic for episode number 934 for 8 8 20 23 is revisiting global privacy control. But before we get to that, we're going to update on what happened last week with Voyager two. Something new happened. Oh, in that, I mean, it's, it's, it's, it's providing more news than J P L and NASA wishes it was producing than anything 12 billion miles away should really and all. Yeah, that's right. Yeah, they, they, the good news is they haven't lost it, although it'd be easy to go to lose track of it. Also we're going to answer the question, what did Tenable's C e o Amit Joran have to say about Microsoft's security practices? And what did Bruce Schneider have to say about the recent attack on Azure by Chinese hackers? Also there's more to AI than chat. G P T.
(00:04:03):
What did some academic researchers in the UK accomplish by adding new deep learning modeling to a classic and previously weak attack? And after discussing some interesting listener feedback from the prior week, we're gonna revisit, as I said, a topic that we covered when it was young, because it's beginning to show signs that it might have a life of its own and may not be destined to fall by the wayside as all brokers of our personal information would hope. And of course, we've got another great picture of the week. So I think a fun podcast for our listeners. <Laugh>
Leo Laporte (00:04:40):
Always, always fun with Steve and informative. We can't forget that. Our show today brought to you by a name. You know, our studio sponsors the great folks at a c i learning big fans. And you may say, well, how do you know about a c i learning?
(00:04:56):
Because I know about a IT pro. And IT PRO has been a sponsor for, since they started for a DEC decade. The best place to go to get your IT training so you can get your first job in IT or to get your team up to spec so they can handle modern security, modern threats, audits, all the things you need to do the compliance. 94%, I'll give you a stat. 94% of CIOs and CISOs agreed that the, one of the most important parts of their job is attracting and retaining talent. There is an IT talent shortage. So it's, it's more important than ever if you've got a team to keep their skills up to date and to make it a great place to work. 87% of companies say they have native skill gaps in their employees. The challenge of assessing your IT staff skills though is, is, is not easy.
(00:05:51):
However, there's a new tool from a C i I think this is so great. That does make it easy. A c i learning is partnered with the best in the industry and it's added a new feature called Insights. It is a skills gap analysis tool to assure you the training you're providing is working and to help you pick the training to give to your team the stuff where you need to work on it. Right? In a quick one hour assessment from Insights a c I learning will provide your whole team with key diagnostics. This is the solution IT managers have long awaited with insights. You can identify specific skills gaps in your employees. You can see where your team's weaknesses lie. You can empower your team too with now with a c i learnings in personalized training. I mean, why train people for stuff they're already excellent at Right?
(00:06:42):
Blanket training. Just waste money and time insights gives you those detailed information you need the solutions, the support and strategy you need by issuing recommendations, and it'll even generate a training plan for individuals or your whole team. Now that's sweet, that's really great. You can compare your results against other organizations so you know, if you're, you know, doing well, if you're up to snuff, you could test skills. You can close the gaps with Practical Labs that allow trainees to focus on the skills they need most. This is really a great thing. A c i learning. They, they do such a good job. They help you not only improve your team, but retain your team and entrust them to thrive while investing in the security of your business. It's a win all round. More than 7,200 hours of content are available now that's up from what was what, 5,800 about a year ago.
(00:07:35):
I mean, they are firing on all cylinders. But that's important because you wanna make sure they always have the newest, the latest stuff in the content. New episodes are added every day from their studios. A c i learning stomps, its competitor with a 50% higher completion rate on their stuff. Now that's a very good sign. That means people enjoy and are learning from the a c I stuff. These are training solutions. Your business has been waiting for future proof. Your team and company with insights, the newest tool from ACI learning, they're always getting better. Visit go dot aci learning.com/twit, make sure you add that slash twit so they know you saw it here. That'll give you as much as 20% off at least 20% off or as much as 65% off depending on the size of your team on an IT pro enterprise solution plan.
(00:08:25):
Just fill out the form, you're gonna get a quote and you'll know exactly what you're gonna pay ACI learning visit go.acilearning.com/twit. These guys are great. They do such a good job and you need it. You need it for your business. Tell you another thing we need, we need a picture of the week, Mr. Gibson <laugh>.
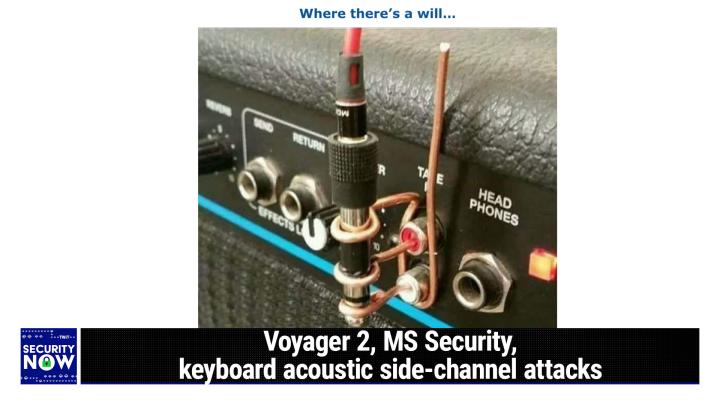
Steve Gibson (00:08:44):
So, okay, now normally I'm able to explain on an audio podcast what the photo is that we're looking at. You're not gonna attempt that with this, huh? <Laugh> this. Well, this is a bit challenging. Okay, so, so here's the problem that an industrious person set out to solve. They had a, one of the newer style stereo plug connectors. Like, like remember the old days headphone jacks were large plugs. We, they technically they're called quarter inch phone plugs or, or, or phono plugs. But then newer headphones had the little smaller stereo connector, you know, like the kind that would plug into, into our smartphones when smartphones still had headphone connectors.
(00:09:37):
So the problem is, so the, a person has a signal source with that kind of a connector on the end, yet he wants to connect it to the old school r c a style mono plug that, that we used to have on the back of stereos, for example. And, and, and in this case it's the tape in connectors. And so there's two of them, right? So because each one is, is man, all you have do is one is you state the problem. How do I get a mini out mini jack output into dual R c a left and right r c a connectors? How do I solve that? That's much simpler said <laugh>. That I would said much more simply, Leo. Yes, there you go. And this is the wildest solution ever. So he is got, he's got, he's got an adapter at first thing.
(00:10:31):
Exactly. He's got exactly, he's got an adapter on the thing, right? Exactly. So the, the, and, and, and remember that during that transition phase in headphones, and you still see it around, you'll, there is a, it, it is a, a, an adapter from the mini headphone connector to the old school large one. If you wanna plug it into something with, with a regular quarter inch headphone pla plug socket. So, so he, he plugs this little guy in into the adapter. Now it's a quarter inch size <laugh>. The problem is, you know, you've got a pair of R c a manal connectors. Now, could this guy, you could go to the store and buy, that would've been a connector. You know, I'm sure I have some, you know, I do in my random adapter box, you know, but new, this is an emergency.
(00:11:25):
Well, it was an e story, an emergency, or he had some extra thick, very heavy gauge copper wire around. Yeah. And praise to him for using heavy gauge copper here. Oh, yeah, yeah, you gotta do that. It's sort of like a coat hanger. I mean, I, you know, it took some effort to bend this copper, this solid copper wire. Again, now here's where I've already like painted myself in a corner. I don't know how to describe this except to, to say, imagine that you created like an eyelet with the copper, so that it was an eyelet that then had a straight piece, and then you slid the eyelet down onto the quarter inch plug. And now remember that the quarter inch headphone plug has rings, right? It's got some insulator rings, and so it's got, it's actually three different conductive zones that, that you want to connect to.
(00:12:25):
So this guy, you've got your tip and you've got your ring, right? Your ring, your ring and your tip. Exactly. Ring your tip. Yeah. And, and so, so he's got copper wrapped around the ring and the tip, which then goes into the r c a, the, the manal, R c a red and white for left and right plugs, right Then, then to anchor the whole thing. <Laugh> back on, near, near the, the, the base of this, he's, he, he wraps the copper around and then does a big loop, a big U-shape loop, because he needs to connect to the, to, to the ground side of these R C a plugs. Anyway, really, you need to download, you need to download the show notes. It's, it's worth it. If you download the show notes to look at the page, the first page, you'll never figure it out if you're just listening.
(00:13:17):
It's crazy. It's, but beautiful. I mean, it's just elegant. Absolutely. Yeah. It's an elegant solution. <Laugh>, and maybe this was just until the Amazon delivery came. Yeah, probably. And couldn't wait to get the listen, listen, had to have an adapter right now for whatever purpose. Anyway, hats off to the anonymous inventor of this approach. I don't think there's a market for this, because, you know, Amazon will sell it to you for $3 and deliver it in the afternoon. So, okay. So when we last left the Voyager two space probe, it had received a series of mistaken commands from ground control, which caused it to turn two degrees away from Earth. Now, at its <laugh>, at its present distance of 12.3 billion miles, two degrees might as well be 90 degrees. I mean, you know, it's missing the earth by a long shot. So this meant that no more data could be received, nor could any corrective commands be sent to the probe.
(00:14:25):
It wouldn't hear them. Now, the good news is that as long as all is going well, Voyager has a failsafe system that was expected to perform an automatic reorientation this coming October. Actually, it's on the 15th of October, but you know, that's still three months away, right? So NASA wrote, Voyager two is programmed to reset its orientation multiple times each year to keep its antenna pointed at Earth. The next reset will occur on October 15th, which should enable communication to resume the mission. Team expects Voyager two to remain on its plan trajectory, <laugh>, let's hope that happens during the quiet period. But then last week we received an update from NASA on August 1st, 2023, using multiple antennas. NASA's Deep Space Network was able to detect a carrier signal from Voyager two. A carrier signal is what the spacecraft uses to send data back to earth. The signal is too faint for data to be extracted, but the detection confirms that the spacecraft is at least still operating.
(00:15:47):
The spacecraft also continues on its expected trajectory. Although the mission expects the spacecraft to point its antenna at Earth in mid-October, the team will attempt to command Voyager sooner while its antenna is still pointed away from Earth to do this. A D S N, that's the, the abbreviation for Deep Space Network. A Deep Space Network antenna will be used to shout the command to Voyager to turn its antenna. This intermediary attempt may not work, in which case the team will wait for the spacecraft to automatically reset its orientation in October. Either way, once the spacecraft antenna is realigned with earth communication should resume. That was on August 1st. That was when we did the podcast last week on Tuesday. Then August 4th, three days later, NASA has reestablished full communications with Voyager two, the agency's Deep Space Network facility in Canberra, Australia sent the equivalent of an interstellar shout, meaning I guess they cranked the, the power up to max or maybe 11 and said, you know, point here anyway, more than 12.3 billion miles to Voyager two, instructing the spacecraft to reorient itself and turn a antenna back to Earth with a one-way speed of light delay of 18.5 hours, speed of light, 18 and a half hours just to get out there.
(00:17:40):
For the commander reach Voyager, it took 37 hours for the mission controllers to learn whether the command worked. At 12:29 AM Eastern daylight time on August 4th, the spacecraft began returning science and telemetry, telemetry data indicating it's operating normally, and that it remains on its expected trajectory. So, yay. You can just imagine the breath holding that was going on during those 37 hours. But really the entire project is an incredible engineering accomplishment. You know, these guys should be so proud of what they have done. It's, and you can't, you know, you can't just fire up a telescope and look for it. It's beyond Pluto. I mean, it's, it's not visible. It's Leo, it's gone. It's gone. <Laugh>. I mean, we fully expected it to simply dissolve. It's so cool when, when it left the, the Earth's simulation, you know, it's so cool. But it's just, it's really incredible. It's just the need thing thing. And, and when it didn't die after it's first, you know first planetary encounter, they said, well, huh, let's keep going. <Laugh>. I mean, what the hell? You know, this stuff is so over-engineered. I mean, look at perseverance. Look at, I mean, it's amazing the rovers that just like, you know, like they got covered in dust and they wound down, and then the dust blew off and it came back. Hello? Hello. What on Come, what did I miss? What's up, <laugh>? What's up <laugh>?
(00:19:16):
Wow. Rather just very feel good story. Just great. Okay. So everyone who listens to this podcast knows that I often become upset with Microsoft's behavior and with their performance. Oh, you had a friend this time, didn't you? <Laugh>, I know where you're going with this one. I, I sometimes feel odd since I could imagine someone reasonably saying, if you have so much trouble with Microsoft, why don't you just switch to Mac or Linux? And it's true that I do love Windows and I have a very, and I have very little trouble with it myself. But due to their size and their dominance, Microsoft's behavior matters and affects the world regardless of what desktop platform I've personally chosen. And since this podcast covers security, it also needs to explore Microsoft's many behaviors related to security. Well, last Wednesday, August 2nd, someone else weighed in on Microsoft's security practices from their own perspective and significant experience.
(00:20:28):
Since I sometimes feel a bit self-conscious tearing into Microsoft over and over, I wanted to share this additional viewpoint. But for what? This what this individual, for what excuse, excuse me, but for what This individual, I'm getting a little excited <laugh>, as you can see, for what this individual wrote, to have any weight and bearing, you need to know something about the postings author. As I mentioned at the top of the show, Amme Joran Wikipedia informs us. Amme Joran is chairman and chief Executive Officer of Tenable, a position held since January 3rd, 2017. Previously, Joran was president of Computer and Network Security Company, R s A, we've heard of them. Joran joined r s A during his tenure as c e o of Net Witness Corp, which was acquired by SSA's parent Company E M C in April of 2011. Prior to his time and net witness, Joran was the National Cybersecurity Division Director within the United States Department of Homeland Security.
(00:21:38):
He took up the post in, in September, 2003 and served as the initial director of the US cert. That's of course the US Department of Defense computer Emergency Response Team. He resigned from his position at US CERT in October of oh four. Earlier in his career, Jorn was a co-founder and c e o of Rip Tech, which was acquired by Symantec in August, 2002. He also served on the board of directors of s OTA, acquired by R s a Guardian, acquired by I B M Guidance software and other internet security technology companies. Joran is a graduate of the United States Military Academy and served as one of the founding members of the US Department of Defense's Compu Computer Emergency Response Team. He has a master's degree in computer science, other words, very impressive guy. Very, this guy has earned, yes, he has earned some street cred by being like in the middle of computer security for many years.
(00:22:38):
His LinkedIn posting last Wednesday is titled Microsoft. The Truth is Even Worse than You Think. Oh boy. So here's what Amit wrote and posted publicly on LinkedIn, a platform Microsoft purchased. He wrote last week, Senator Ron Wyden sent a letter to the cybersecurity and Infrastructure Security Agency, cssa, the Department of Justice and the Federal Trade Commission, asking that they hold Microsoft accountable for a repeated pattern of negligent cybersecurity practices, which has enabled Chinese espionage against the United States government. According to data from Google Project Zero, Microsoft products have accounted for an aggregate 42.5% of all zero days discovered since 2014. He writes, Microsoft's lack of transparency applies to breaches, irresponsible security practices and vulnerabilities, all of which expose their customers to risks. They are deliberate that they are deliberately kept in the dark about in March, 2023. So right, just this past March, a member of Tenable's research team was investigating Microsoft's Azure platform and related services.
(00:24:13):
The researcher discovered an issue which would enable an unauthenticated attacker to access cross tenant applications and sensitive data such as authentication secrets. To give you an idea of how bad this is, our team very quickly discovered authentication secrets to a bank. They were so concerned about the seriousness and the ethics of the issue that we immediately notified Microsoft. Did Microsoft quickly fix the issue that could effectively lead to the breach of multiple customers, networks and services? Of course not. They took more than 90 days to implement a partial fix and only for new applications loaded in the service. That means that as of today, and he wrote this last week, the bank I referenced above is still vulnerable more than 120 days since we reported the issue. As are all of the other organizations that had launched this service prior to the fix and to the best of our knowledge, they still have no idea that they are at risk and therefore can't make an informed decision about comp, about compensating controls and other risk mitigating actions.
(00:25:44):
Microsoft claims that they will fix the issue by the end of September, meaning end of next month, four months after we notified them. That's grossly irresponsible, if not blatantly negligent. We know about the issue. Microsoft knows about the issue and hopefully threat actors don't cloud providers, he says, have long espoused the shared responsibility model. That model is irretrievably broken. If your cloud vendor doesn't notify you of issues as they arise and apply fixes openly, what you hear from Microsoft is just trust us. But what you get back is very little transparency and a culture of toxic obfuscation. How can a ciso, a C I S O board of directors or executive team believe that Microsoft will do the right thing given the fact patterns and current behaviors? Microsoft's track record puts us all at risk, and its even worse than we thought. Ugh. Wow. A culture of toxic, toxic obfuscation.
(00:27:07):
Obfuscation. I love that. Okay, now by looking at the facts, through the years, we've documented a great many instances where Microsoft's behavior, whether apparently deliberate or inadvertent, yet either way, quite difficult to see as anything other than we are so big we don't need to care and you can't make us has clearly damaged their own customers even significantly. But their enterprise and government customers are as captive as I am. I'm held captive by my decades long investment in Windows, and by the fact that there is no viable alternative to Windows for some of the things I want to do, I depend upon many tools that are only hosted on Windows. And Microsoft's big enterprise customers have invested massively in their own solutions, which are also not portable to any other platform. The incredible power this position gives Microsoft should not be underestimated. It leaves the entire world asking, please, sir, may I have some more soup?
(00:28:27):
Amit Yin's posting on LinkedIn prompted an interview by Cyber Scoop. They, in turn, cyber Scoop wrote Veteran Cybersecurity executive Amit Yen accused Microsoft on Wednesday of dragging its feet on fixing critical cyber secure critical vulnerability, a sorry, fixing a critical vulnerability affecting its Azure platform and said the Check Giant, the tech giants slow response illustrates a negligent approach to security. His harsh public critique of Microsoft, a relatively rare event for a high profile corporate figure in cybersecurity follows criticism from lawmakers and researchers alike. After a recent cyber attack affecting US government officials resulted from a Microsoft security lapse as the c e O of Tenable, a firm that helps customers understand and mitigate their cybersecurity vulnerabilities. Your end said he works with hundreds of companies every year to disclose and patch vulnerabilities. Microsoft, he said, consistently fails to proactively and professionally address vulnerabilities in their products.
(00:29:47):
Joran told Cyber Scoop in an interview quote in Microsoft's case, you have a culture which denies the criticality of vulnerabilities unquote, according to a timeline. In a limited blog published to Tenable's website, Microsoft acknowledged the issue the same day. It was disclosed on March 30th and confirmed it four days later. Tenable asked for an update on June 27th, 90 days later, and was told on July 6th that it was fixed. But Tenable says it was merely a partial fix. Okay, now where have we heard that before? How many times on this podcast have we noted that, you know, someone at Microsoft who was shown a serious vulnerability by a security researcher and even given a fix for it, apparently didn't even take the time or care to actually understand the underlying problem. And so only half patched it to resolve one of the problem symptoms. A anyway, cyber scoop continues on July 21st.
(00:31:06):
Microsoft told Tenable that it would take until September 28th for a complete fix. Tenable agreed to withhold technical details and proofs of concept until September 28th. In his blog post, Joran described Microsoft's approach to addressing the issue as grossly irresponsible, if not blatantly negligent. Joran wrote that quote, more than 120 days since the vulnerability was reported, the bank in question remains vulnerable unquote, adding that many vulnerable organizations still have no idea they're at risk and therefore can't make an informed decision about compensating controls and other risk mitigating actions. <Laugh>. And then we heard from Microsoft get this Mike, he's <laugh>, they wrote a spokesperson for Microsoft, said that the company quote appreciates the collaboration with the security community to responsibly disclose product issues. <Laugh>. And that security updates are ultimately a delicate balance between timeliness and quality while ensuring maximized customer protection <laugh> with minimized customer disruption unquote.
(00:32:29):
Wow. Said Friday in a blog post that the issue has, quote, been fully addressed for all customers, unquote. So I guess Joran got their attention was hit with his blog post in LinkedIn and, oh, what do you know, just two days later, it's been completely fixed. It was gonna take until September 28th, but shine a bright light on the problem. Oh look, it's all fixed. They said no customer remediation action is required and that all affected customers were notified via email starting Friday. Microsoft said its investigation, quote, identified anomalous access only by the security researcher that reported the incident. And no other actors on phone. No one's using this. We don't have to worry that. Yeah, don't know. You don't worry about it. Your end. So they <laugh>, they say your end's broadside against Microsoft. Comes amid growing scrutiny of Microsoft in Washington after one of the company's products was abused by hackers based in China to steal the email messages of senior US officials in that incident.
(00:33:44):
Hackers based in China were able to steal an encryption key that they could then use to forge authentication tokens and security researchers have sharply criticized the company for not only allowing an encryption key to be stolen, but for building a computing architecture in which tokens could be forged in this way at all. The incident spurred Oregon Senator Ron Widen to call Microsoft negligent in its security practices and request that the Department of Justice investigate whether Microsoft's actions in the incident broke the law. Okay, now I'll just say good luck with that Washington. A long time ago when Microsoft was much smaller and far less powerful, it was nearly impossible to hold its behavior to account. There's just no possibility of doing it any longer.
(00:34:44):
They said, while Microsoft has insisted that the Chinese operation was highly targeted research by the cloud security company, whizz <laugh> suggests the incident may have been more broad than first understood a claim. Microsoft has dismissed as speculative. You know, right? Because, you know, Microsoft is as dismisses a speculative because after all, a delicate balance is required between timeliness and quality while ensuring maximized customer protection. They said the 10, the the vulnerability discovered by Tenable allowed an an auth, an unauthenticated attacker to access cross tenant applications and sensitive data such as authentication secrets. According to Jo's blog post, it appears, and everybody agrees, that does not exploit the same types of authentication of flaws seen in the recent incident involving Chinese hackers, but may add pressure on Microsoft to improve its security practices. Okay, <laugh>, we can hope. Unlikely industry professionals and government officials pointed out that the Chinese operation was only detected because a government agency was paying additional money for more sensitive logging capabilities.
(00:36:08):
Microsoft later reversed that policy. Basically it was charging people for better logging of their, of their, of the activity on their cloud platforms. And they got a lot, they got in a lot of hot water for, for, or making money for like, just offering more locking that like cost them nothing. Joran who has grown increasingly critical of Microsoft in recent years told cyber Scoop that the company's dominant position in the technology ecosystem makes many computer security researchers hesitant to speak up about its security practices. But the doing so is especially important given the ubiquity of its products, to which I say exactly and finally quote, Microsoft is a pretty strategic problem in the security space, given the pervasiveness of their software, of their infrastructure. Joran said, I also think they have to be part of the solution. Well, yeah. 'cause No one can make them do anything.
(00:37:13):
So, you know, I'm not a fan of complaining about problems that no one has any power to resolve. As an engineer and technologist, I most enjoy discovering and sharing solutions to problems, but ignoring truly important issues in a podcast that's focused upon security seems negligent too. So we'll just keep perspective, discuss problems and celebrate those companies who do act quickly and responsibly in the best interests of the users of their products. But there is the issue of that recent serious attack by Chinese hackers several weeks ago while working on a previous episode of this podcast, I saw this news that's referred to in the cyber, the cyber scoop piece. I suppose I let it slide past because well, that's what you know, what that expression about beating a dead horse at some point, I'm sure that we all get tired of complaints about Microsoft. Sort of like how many ransomware attacks are we going to, you know, detail here at some point?
(00:38:21):
What's the point? But saturation shouldn't keep us from covering important security events. And this Chinese attack was very important and quite significant. The best way to deal with it today is to refer to a well-known industry expert who very nicely framed what happened. He is Bruce Schneider and Bruce posted under the title Microsoft Signing Key Stolen by Chinese. Bruce wrote a bunch of networks, including US government networks have been hacked by the Chinese. The hackers, he said, used forge authentication tokens to access user email using a stolen Microsoft Azure account. Customer signing key Congress wants answers the phrase negligent security practices is being tossed about and with good reason, says Bruce master signing keys are not supposed to be left around waiting to be stolen. He said, actually two things went badly wrong here. The first is that Azure accepted an expired signing key, implying a vulnerability in whatever is supposed to check key validity.
(00:39:55):
The second is that this key was supposed to remain in the system's hardware security module, it's H S M, and not be in software. This implies a really serious breach of good security practice. The fact that Microsoft has not been forthcoming about the details of what happened tells me, says, Bruce, that the details are really bad. And he says, I believe this all traces back to SolarWinds. In addition to Russia inserting malware into a SolarWinds update, China used a different SolarWinds vulnerability to break into networks. We know that Russia accessed Microsoft source code in that attack. I've heard from informed government officials that China used their SolarWinds vulnerability to break into Microsoft and access source code, including Azures. He says, I think we are grossly underestimating the long-term results of the SolarWinds attacks. That Backdoored update was downloaded by over 14,000 networks worldwide. Organizations patched their networks, but not before Russia and others use the vulnerability to enter those networks. And once someone is in a network, it's really hard to be sure that you've kicked them out. Bruce finishes sophisticated threat actors are realizing that stealing source code of infrastructure providers and then combing that code for vulnerabilities is an excellent way to break into organizations who use those infrastructure providers. Attackers like Russia and China, and presumably the US as well, are prioritizing going after those providers.
(00:42:07):
So Bruce, nicely and succinctly explained what happened with the Microsoft Azure mess. In short, they first deeply screwed up when they failed to take responsibility for their screw up. And only now Microsoft is starting to wonder how Microsoft became this powerful. Well, I got a news flash for you. I also thought of Bruce Schneider recently in another context because I, I love to quote one of his pithy observations, which is, attacks always get better, they never get worse. While that's kind of obvious, reminding ourselves of its truth serves as a nice reality check. And in this case, it explains what recently happened with the classic attack of listening to someone typing on a keyboard. And with that tease, Leo, we're gonna listen to you telling us about an advertising. I'll type out an ad <laugh>. All right, Steve? Yeah. Boy, I I, when I read that screed, I thought of you immediately.
(00:43:18):
Yeah. you know, I think part of the problem with Microsoft is just that they have so many ins that's such a big installed base. I think anybody with a big installed base like that would have similar problems. But anyway, well, I, yes when I saw him, him note the, the percentage of zero days that were theirs, it was like, well, yeah, well, of course it should be a hundred percent. It could be a hundred percent right. Well, and, and, and or, or if, if you were to break Microsoft up into individual organizations, right, each responsible for one of their different products, then, you know, the zero days would be spread out the way they are among everyone else. So, you know, it is the fact that they're such a behemoth. On the other hand, that's a problem. I mean, the, I used to know people at Microsoft who were really nice people. Brad Silverberg was a great guy. And the, you know, the, the really good guys, they're gone. You know, they, they took their money and left. And now we're just left with kind of an un unaccountable monstrosity, <laugh>.
(00:44:27):
There's always Linux and Mac. If you ever wanna change, Hey, I love my unaccountable <laugh>, my unaccountable monstrosity. I know you do. I know you do. This episode of Security Now is brought to you by Thanks Canary. If you are running an enterprise and you are worried about the advance, we talked about advanced persistent threats last week, if you were worried about hackers wandering your network, I wanna show you something that everybody who has something to protect inside their perimeter ought to have. It's the Thinkt Canary. Most companies discover they've been breached too late. <Laugh> was it, was it the, the British government just said, oh yeah, we were breached. But you know, the election of we are breached, but, and we were gonna tell you, but we just, we didn't get around to it right away. And oh my gosh, you would think the British Election Authority would have a few of these and would know the minute bad guys breached their defenses.
(00:45:25):
Last month, an attacker compromised one of your users. This is, this is a hypothetical scenario that could already be happening right now to you. That person has been in your network for a month reading company chat, searching for keywords and embarrassing data perhaps looking at where you do your backups so they can make sure they'll clobber those when they trigger the ransomware attack. Exfiltrating data about your customers and your employees or your voters. How would you know? How would you know? You got a great perimeter defense, but how would you know that they got through it? What about your lead developer just down at the Starbucks happened to be targeted and compromised at the coffee shop. Now comes back to the office, plugs in the computer. The bad guys inside your perimeter. How would you know you could if you had a canary and canary tokens?
(00:46:21):
Canary tokens are awesome. Everything's canary can generate canary tokens. Drop. things like, well, well, how about this? This is a cool one. A fake A W S A P I key. Put it on every enterprise laptop before they go out the door to Starbucks. <Laugh>. Just put it in there, right? Attackers compromising your users. See those? We got 'em. We got the S three bucket baby. But the minute they use them, it's not the SS three keys or secrets. It's a canary token that pings you and says you're being attacked. Canary tokens are tiny trip wires you could put anywhere in your network and hundreds of them, thousands of 'em if you want. They follow the basic things to canary philosophy. Trivial to deploy with a ridiculously high signal quality. Three minutes of setup, no ongoing overhead, virtually zero false positives. We've had a canary on our network since they started advertising.
(00:47:20):
It's been fewer few years and, and no false positives. One real positive that we reacted on and was glad we had it, but no false positives. But the thing is, you're gonna get an alert, whether it's email, text slog through your canary console. You get to choose. There's even an a p i. You could have your own write your own script like Steve does so that the it could go Yeah, but daba do in the background. When you're, when you've been triggered, every customer gets their own hosted management console. You could figure the settings in there. Create canary tokens. Take your Canary hardware and make it be anything you want. This one's a sonology na, you could make it. No, it's not. It looks like it though. Even the Mac, even down to the Mac address. It could be a Windows server, a Linux server.
(00:48:09):
It could be I i s there's little room for doubt. If someone browsed a file share and opened a sensitive looking document, looking is the key word on your canary, you're gonna get that immediate alert. Often they give away more than they intend to. If they try to log into this sonology, the the email address they use will be very telling. Won't it? It'll maybe even let me know which employee has been compromised, right? If it's rare to find a security pro product that, that people can tolerate, that doesn't slow you down, get in the way, bug you, irritate you. This canary sits on a shelf <laugh>, no one even knows it's there. Especially not the bad guys until we need to know. This is the security product everybody loves. Just go to Canary Do Tool slash Love. You'll see all the love hardware, VM and cloud-based canaries.
(00:49:00):
They have all kinds Now they're deployed and loved on all seven continents. Yes, all seven Canary tool slash Love. You'll see a bunch of unsolicited tweets and emails where people say what they really think of the things Canary. And I'll give you a hint. They love it. We love ours. You'll love yours. Visit canary.tools/tweet. This is how you know whether you're being attacked. You know, you know you've got your perimeter, but what happens when they get inside? This is how you know this is the canary in the coal mine. How much they cost. Well go to Canary Tools slash twit. I'll give you an example. Say you want five of them. You know, a big bank might have hundreds or even thousands. A little operation like ours might have a half dozen, but let's say 5 7500 bucks a year for those five, you get the five Canaries your own hosted console.
(00:49:45):
You get upgrades, you get support, you get maintenance. And now that they've got VMs and other ways of doing it, you really need to go check it out. Canary Tool slash Twit. 'cause It's gonna really depend on how you configure it. If you use the code twit, T W I t and the how did you hear about Us Box, this is one thing I can tell you, 10% off for life, for Life, thanks to Canary incomparable value and a must have for every security setup. But if for any reason you're unhappy, you can always return your Canaries with their two month, 60 day money back guarantee for a full refund. I can say that with confidence. 'cause In all the years we've advertised things <laugh>, no one has ever asked for a money back. Not one <laugh>. It's worth it. Trust me, you once you have a things canary or two or three or four, you will not wanna live without them.
(00:50:39):
This is real peace of mind. Canary Tools slash twit. Don't forget if you put twit in the, how did you hear Bus Box 10% off Forever for life. This is just the best thing ever. I am a huge fan and I'm glad we have them. Canary Tools slash twit, you will be glad you have one too. Alright, back to Steve and okay. The issues of the day. Yes. So <laugh> okay. As I was saying, Bruce Schnier reminds us always that attacks always get better. They never get worse. Which is in, in the sense that they always get better for the bad guy. They always get worse for the good guy. <Laugh>, let's be clear. Yes, exactly that. Right? Right. Okay. So and in this case, this explains exactly what happened recently with the classic attack of listening to someone typing on a keyboard.
(00:51:50):
Although significant controversy, understandably, I think surrounds questions regarding the current and future impact of chat, G p T style, conversational AI models, a huge amount of far less glamorous. Yet nonetheless, important work is being done by applying some of these newly emerging AI ish techniques to previously explored domains. We've talked before about the concept of having a smartphone resting on a desk surface with its microphone passively listening to the keystrokes being typed nearby. If this were practical, it would represent acoustic side channel leakage from the keyboard. And since confidential information might be entered through that keyboard, and since in general no one wants or expects to have their keystrokes surreptitiously monitored and recorded, it would represent an attack. And speaking of attacks, as we said, they always get better. Last Thursday on August 3rd, a trio of researchers from three different universities in the UK published a paper for the 2023 I e e e European Symposium on Security and Privacy Workshops.
(00:53:08):
Their paper is titled A Practical Deep Learning Based Acoustic Side Channel Attack on Keyboards. Here's what they described from their research and of its success. They said, with recent developments in deep learning, the ubiquity of microphones and the rise in online services via personal devices, acoustic side channel attacks present a greater threat to keyboards than ever. This paper presents a practical implementation of a state-of-the-art deep learning model in order to classify laptop keystrokes using a smartphone integrated microphone. When trained on keystrokes recorded by a nearby phone, the classifier achieved an accuracy of 95%. The highest accuracy seen without the use of a language, of a language model. When trained on keystrokes recorded using the video conferencing software zoom, an accuracy of 93% was achieved a new best for the medium. Our results prove the practicality of the side channel attacks via off the shelf equipment and algorithms.
(00:54:37):
We discuss a series of mitigation methods to protect users against these series of attacks. Okay, so this is a phenomenal level of recognition. 95% for an outbound external microphone that's, I'm sorry, an outboard external microphone that's simply listening to keystrokes from a keyboard nearby and to only lose 2% accuracy when significantly compressing the audio through Zoom is equally astonishing. Imagine being able to process the recorded sounds of someone typing after the fact, you know, through a, a, a, a compressed connection to be able to obtain a near perfect rendition of what they originally keyed. This is achieved essentially by utilizing far more of the total available information than any previous efforts have managed. For anyone who wants the details, I've included a link to the entire 21 page research report, but I think we already have the gist of the idea. And there's an important lesson here for us.
(00:55:59):
Regardless of the outcome of the debate over the true longer term value of chat G p t style interaction, I think it's very clear that something has happened recently and that the world has been changed. We're still not sure of the what and how of all of these changes. And I'm also certain that they're still underway. Research like this demonstrates that applications of the new deep learning models have only just begun to be explored. I expect we're gonna be seeing some very significant discoveries in the future relative to security once these relatively new capabilities become more widely available. And Lord only knows what those side channel attack masters at the Ben Gurion University of the Negev in Israel are gonna come up with. They've made their thing, haven't they? <Laugh>? Oh my God. Once they add deep learning modeling to their many bags of tricks, you're right.
(00:57:03):
Yeah. I mean, oh boy, <laugh>. Wow. Yeah, we, I don't think we're gonna have to wait long either, 'cause they, the, these guys tend to be on top of things. Okay, so some feedback from our listeners, rusty tweeting as at Rusty oh 1 0 1, he's, he has another take on the, in the cloud or on the ground discussion. He said, listening to this week's ssn with the discussion of running things in the cloud, I'd noted that more and more people are running their own power stations, either with solar, wind, or water wheel systems, including Amazon for at least one of their a w s sites. I think that's becoming less and less of a useful counter argument. He said additionally, he said there have been recent cloud providers who've decommissioned equipment that was providing cloud services right up until it was shut down. And apparently end users didn't get the word for some reason.
(00:58:05):
Some of whom have lost significant functionality as a result. Perhaps that's not going to be an issue for some of the larger providers, but if you are trying to work within a budget, there may be storm clouds on the way. Okay? So I think there's no question that there's a real and vital role for cloud-based services. I'm not intending to suggest otherwise, but there can also be a bit of a gold rush mentality of imagining that the only reason there's still anything that's not in the cloud is inertia and that eventually everything will be, I think the reality is there's probably a place for both. And that's the point that I had intended to make. I also sort of liked that whole notion that, that we're losing the, the inherent distributed nature of the internet, which is one of the ways that it got so much of its strength and robustness.
(00:59:07):
You know, you know, we all feel that everybody aggregating around the a chromium based web browser is not a good idea because we end up with, you know, a monoculture. So it certainly is the case that if anything, like a really bad problem ever hit a W ss, it would impact a huge portion of, of the users of the internet, the, the, the providers of services. And so, you know, that's not the way it used to be, but we'll see what happens. Alan c Alan c Bonacci, he said, hi Steve. I heard you speak about OIE and decided to give it a try. Actually I was talking about, yeah, you're not in favor of oie. Yeah. I've mentioned aie back in the day. It was, it was from Twilio, but you and I both have come up with better solutions I think since Right?
(01:00:02):
Anyway, so, so ba basically he's talking about some two factor authenticator, you know, A A A T O T P based approach, he said, so I reset the two factor authentication code on a a Gmail account to generate a new code. What is strange is that the T O T P and my password manager is different from Authe. I managed to log in with both. Could it be clock differences between my desktop and my phone? If yes, why would both work fan of the show? Okay, so Alan did follow up a bit later to confirm that it was indeed a clock difference as to why both of the different codes would work. Many authentication receivers, you know, authenticators will continue to accept a recent, if not 100% current code. When they receive a code and the present one doesn't work, they may try the next one that's about to come up, or they may try the previous one that was just technically obsoleted and maybe even the one before that.
(01:01:13):
The point is that for the system to work, both endpoints need to share not only the same secret key, and there there's no fudge factor. Of course, because that, that key is the pseudo random sequence. But they must also agree upon the current time of day in today's internet connected world, it's easy for devices to be within, you know, very close clock agreement. 'cause We're all able to get the time from the internet, but it's also reasonable to make some allowances for them not being, and of course there is the whole, you know, man in the middle literally a a person in the middle, you know, reading the code from their phone and then turning around and transferring it by, by keying it in on their keyboard. And so that's going to introduce a little bit of a delay and thus some, some need for fudging.
(01:02:07):
So that's all that was going on was that the, the, the authenticator would much rather be a little bit tolerant and accept a, you know, as, as long as only one use of the code is possible, that is as long as the code when used cannot be used immediately. Again, I don't see any reason for, for giving the, the user a bit of, a bit of leeway and also cutting down on user frustration of, of the system saying, sorry, that code's invalid when you're quite sure that it just was Joe lag Greca. He said Firefox oh. He said, I, he's he said, I'm finally ready to leave the Google Chrome browser. Which browser do you use or recommend? And he said, Firefox. And of course Firefox is, were both Leo, you and I are and I'm completely happy with a choice. Me too.
(01:02:59):
I'm never changing. Yeah, yeah. Well, I shouldn't say that, but I know it's hard to say never. Right? so some time ago I did try using binging 'cause I was curious about tabs down the left hand column of the browser. But frankly I was stunned when I encountered some sites that it would not render. I thought, what, you know, who knows? Anyway, I had been using Chrome for a while again, just to sort of see how it compared to my longtime previous use of Firefox today, having satisfied a little bit of my wanderlust, I'm back to Firefox. And, you know, many things about it are just exactly right for me. I, I need to use an add-on to get my tabs to run down the left side of the browser. But there's a slick session manager that allows me to save and tire browser sessions and I use that when I'm working on the podcast in order to change lo locations and have all the tabs sent to a different location.
(01:03:57):
So anyway, yes, I am 100% Firefox. And when, when we get to talking about today's topic which we'll get to shortly, you'll learn another reason why it continues to be my choice. Someone whose name is seven in Twitter, he said, apologies in advance if this is a topic you've covered ad nauseum. I listened to SSN religiously from episode one through several hundred, but I had to take a few years off from extracurricular listening. I've since subscribed to Club Twit. Thank you very much. Yay. And return, yeah, and returned to attending weekly services. <Laugh>. Good. He's back. He's got the religion again. <Laugh>, he says, I don't know if my question will be simple enough to address in a dmm, but perhaps with at least perhaps with at least with a suggestion where to start after receiving a notification that one of my accounts was compromised, including he has in all caps the password I have come to fully realize that no passwords are safe.
(01:05:09):
Mm-Hmm. <affirmative>, period. Mm-Hmm <affirmative>, I use two FA wherever possible, but of course two-factor authentication support isn't consistent across all services. Is there a best way to simplify the process of not relying on passwords alone? He says, is there a simple answer to the question? WW SS g d <laugh>, what would Steve Gibson do? <Laugh>, exactly. I love it. Took me a moment. I need a button. Took me a moment to par. Took me a moment to parse ww s g did. But it's clear that that's what he meant. Yeah. Okay, so I'll expand a bit on seven's question by answering what does Steve think about the current and probable future state of identity authentication over the internet? One way to view our current security environment and I'll discuss a second way after this, is to see that what's developing is a spreading spectrum of options.
(01:06:15):
This, you know this is always what we get when new and better solutions at last start being adopted. The reason we wind up with a spectrum that spreads is that the appearance of new and better solutions doesn't automatically kill off the older and less secure solutions, despite the fact that two-factor authentication has been widely available now for what, a decade or or two, most sites still don't offer it as an option. Partly that's due to inertia and partly due to a lack of perceived need. And partly because making logon more difficult increases support overhead to some degree. And now we have pass keys, which represents yet another step forward. But will pass keys kill off two-factor authentication and passwords? No. Over time more sites will be offering Paki support, maybe again, as the perceived need at the higher end of the security spectrum manifests.
(01:07:28):
Eventually support for two factor authentication and passkey will be baked into servers and servers will be taking more responsibility for authentication. After all, you know, servers were doing H T T P without any security not that long ago. And it's only recently that sort of by universal agreement, the whole industry just said, okay, we're just gonna all decide we need to have it. And, you know, e f F and Let's Encrypt made made that more practical by not having people paying for certificates constantly. But we also know that even as two factor support and pass keys becomes more available, many sites still won't care. They'll feel that identifying their visitors with an email address and the password is sufficient. And for many sites, they're probably correct. More and more often internet users are being asked after all to create an account as a requirement just to get in the front door.
(01:08:28):
Why? Probably because it forces its visitors to turn over an email address for the receipt of follow-up spam. It allows a site you may never choose to visit again, to continue to plague you into the future. And it may also be that sites will then be able to further monetize your existence by selling whatever information they manage to accumulate about you. This is one place where to top where today's topic, global privacy control may turn out to be relevant. We'll see. But the other fact is that email and one's control over an email address remains the ultimate fallback when anyone is unable to remember how to log on. I've joked here in the past that I forgot my password link appearing underneath every password prompt makes a strong case for not even bothering with remembering any passwords. Just bang on the keyboard for a while when you're creating an account, then click the, I forgot my password link whenever you want to come back.
(01:09:39):
And I actually think that people would probably do that if it weren't actually quicker and easier to have a password manager remember, and then fill in the answer for you. But what does that mean about the actual security being delivered? And from an actual security standpoint, I have to say that what's really infuriating and even somewhat confounding is to see a two factor authentication prompt, followed by a link saying, I'm unable to use my authenticator right now. What, what's the point of requiring one if you can just say, my dog ate it and then be allowed to log on without it. Usually you have to jump through some hoops though, to, to, well, I mean, it's not just the password at that point, is it? Yeah. I guess it depends on the site. It's your email. Yeah. Wikipedia now has an entry on the topic security theater, defining it as security theater is the practice of taking security measures that are considered to provide the feeling of improved security while doing little or nothing to achieve it.
(01:10:58):
And rightfully, Wikipedia references Bruce Schneider as the originator of that perfect term. And we know that pass keys are gonna be just the same, right? Since no one ever wants increased authentication security to actually prevent anyone from authenticating, there will always be the g get out of jail free card of just click the link we sent to the email address you have on file with us, so we know it's really you. So to seven's original question, I would reply, if you want the most security possible, the only thing you can do is to take advantage of the most secure authentication option available on a site by site basis. Use a password manager to remember your random and long secrets. Use an authenticator app to generate your one-time passwords as pass keys become available. Use them wherever possible. But always keep in mind something that has not received enough attention anywhere by anyone. And I sincerely hope that it does not receive any more attention by the bad guys, which is that because security is about the lowest common denominator. And due to the ubiquitous role, that email continues to play as the ultimate, my dog ate my authentication, authentication recovery, which might be better named total au authentication bypass. Any entity who is able to obtain access, even transiently to your email flow obtains unfettered access to your entire online life.
(01:13:03):
That's why you gotta secure your email <laugh>, let's face it. Exactly. that's really that means that e email, email security is really ultimately important. There are a number of sites now that don't use passwords that just use email. So you'll, they say, what's your email? You say it, you, they say, okay, we're gonna send you a link. Click that, and you're logging log in. That's become more and more prevalent. I guess that's not more secure, but that's just in response to people not doing passwords. Right? Right. Yeah. I mean, I I'm sure that that their, that their poor support people said they got just tired Yeah. Of receiving email. I forgot my password. Right. And they, so they said, okay, screw it. I mean, after all, they were just, they were gonna send a password recovery link anyway, so Right. Short circuit the whole process.
(01:13:54):
Right. And just assume everybody's forgotten their password. <Laugh>. And I, and I have to say, Leo, when I, when I was putting this together yesterday, I sort of had to pause and think, okay what's wrong with just using email? Why, why don't we automate, somehow automate the, like the email pass, you know, link receipt and forwarding process somehow. Yeah. Like, you know, 'cause as I said, that's what this all devolves into anyway. Well, we've always said the weakest link in your password recovery process is your security. Right? If, if there's a way to get a, a password, that's the weakest link. You know? If it's, so, if it's email, it's email. So you might as well just say, okay, we're just gonna use email, not bother with anything else else. Especially else if you're ignore two factor, everything else gives you a, oops, I can't, I, I can't, it doesn't work or email me.
(01:14:56):
It's, I'm standing on my head. So, you know, you know, send me an email link and then let me in. And it always, you can always get in there. That is a good way, that is a good reason, I guess, to use these unique email generators, right? So that every site has a unique email because, well, mostly it's just really, it, it just for it forwards in, it always forwards Yeah. Into your email, into your master email. Yeah. Yeah. But mostly what it says is keep your gosh darn email secure as you possibly can have two factor on that. Yeah. Yep. And I don't think Google, if you lose your two factor just says, oh fine, we'll email you something. I think you have to jump through more hoops than just that. I, I believe so, but I might be wrong. I haven't, I haven't tried it.
(01:15:42):
Yeah, have a have an email provider that really lets you lock the sucker down. Well, and it actually, this is why one of the features that I built into squirrel was after you got comfortable with squirrel, there was a checkbox in the config where you could say, please disable. Yeah. All other authentication, no recovery. Yeah. I don't want, yeah. There are no other ways to recover, otherwise, you don't actually get any additional security. Yeah. I'm now looking what happens if I lose my two FA token on fast mail? I'm just curious. 'cause That's where everything is. Uses your phone, you get a code sent to your phone. Okay. That, that, that's better than nothing. Right? Better than nothing. Although, you know, SS M Ss is not great. Right? That's another <laugh>. So there one more thing. <Laugh>, another li in the list of things to do is make sure that you have either pin protected or somehow protected your cell phone account so that somebody can't sim jack you.
(01:16:48):
And actually the F T C is, is moving forward on regulation on that, because that's really important. I'm trusting Google Fi not to let people, you know, steal my number. I think. Good. Well, yeah, but trust is good if it's merited <laugh>. I know that, that's kind of what I meant. <Laugh>. It's gotta be earned first. Do you wanna take a break here? Steve's take, yeah. Yep. And then we're gonna talk about the global privacy control and and what happened to me yesterday, oh, I'm very interested in this, but, but we'll get to it in a moment. You will be too. Trust me. But first, a word from our sponsor duo. Oh, duo is so great. Duo protects against breaches with a leading access management suite. Strong. We just, were talking about it multi-layered, not one layer. Multi-Layered defenses, innovated capabilities that only allow legitimate users in and keep bad actors out.
(01:17:44):
For any organization concerned about being breached, that needs protection fast duo can quickly enable strong security without hampering user productivity. This is kind of interesting. Usually we say there's a balance between security and convenience, right? Duo, smart duo prevents unauthorized access with multi-layered defenses and then we'll up the defense, increase authentication requirements in real time when the risk increases. And, and so there may be a step up. Oh, yeah. Well, now we want you to do one more thing. Duo enables high productivity by only requiring authentication when it's needed. Right? And it's smart about that. Enabling swift, easy and secure access. You know, when, when it's sufficient, DUO provides an all-in-one solution for strong M F A passwordless single sign-on Trusted endpoint Verification Duo helps you implement zero trust principles by verifying users and their devices. It's a great solution, and you can turn it on like that.
(01:18:49):
Start your free trial, sign up today. Here's what you do. Go to css.co/twit. Got it. Cs.Co/Twit. Sign up for DUO today. You'll be safe tomorrow. Cs.Co. I just made that slogan up, by the way. CS co slash t w I t I hope they don't mind me making up slogans for 'em. <Laugh>, I do that a lot. <Laugh>. Alright, now, I have no slogan whatsoever, whatsoever for this ridiculously named, but I think very potent technology, global privacy control. So today's podcast adventure was triggered when I followed a news link yesterday over to TechCrunch. The screen darkened with an overlay as screens do these days when a site wants to bring something to its visitor's attention. And I was left staring at an interesting notice from TechCrunch. It had their TechCrunch logo, which I always thought is kind of cool in the upper left hand corner.
(01:19:57):
And the headline read, review your Global Privacy Control Preferences. And the notice said, you are using Global Privacy control G P C. This leads to a lower quality experience on Yahoo by blocking certain editorial content, including embedded tweets, YouTube videos, and third party ads that are relevant to your interests. Huh. Okay. That was interesting. It gets better to enhance your Yahoo experience. Allow us to share and sell your personal information. It will be so much of a better experience that way. Right, right. Yeah. Because, you know, it's, it's clearly in my best interest to have my Yahoo experience enhanced. Sure. By allowing them to share and sell my personal information and no doubt about it. So much better. And there's more this, they continue. This includes technical identifiers like your IP address and cookie IDs, but does not include things like personal emails or contact information.
(01:21:16):
Mm-Hmm. <affirmative>. And then this notice in concludes with this won't affect your G P C settings for other websites. And you can always change this preference in privacy controls. And then at the bottom of this little popup, I was presented with two options, allow or don't allow. And you can probably guess which one I chose. Okay. Now, there are several bits of good news here. One is that someone made them do this <laugh>, the other <laugh> you made me. That's right. They didn't, they didn't wanna do this. They didn't wanna ask me this question. The other is that the only reason I received this notice was that I took my own advice back on May 3rd of last year, 2022, as a result of our podcast 8 69, which was titled Global Privacy Control. I flipped a switch that's built into Firefox and then promptly forgot about it.
(01:22:24):
But that switch remained flipped. And I should note that perhaps it's no surprise that the switch is missing from Chrome. However, in addition to Firefox, which incorporates it natively, it is present in both the brave and the DuckDuckGo privacy browsers. And it can be added to Chrome with a use of a third party extension. We'll get to all that later. Okay. So we have many things to talk about here. First of all, to clear up one question, I was visiting TechCrunch, and I was informed by that popup that Yahoo wanted me to drop my pants. <Laugh> Wikipedia. I like that. <Laugh>. I might as well. <Laugh> Wikipedia explains this by writing in 2010, A o l acquired TechCrunch mm-hmm. <Affirmative> for approximately $25 million. Yeah. They gotta make that back somehow. Uhhuh <affirmative> 12, following the 2015 acquisition of A O L and Yahoo by Verizon.
(01:23:26):
The site was owned by Verizon Media from 2015 through 2021. In 2021, Verizon sold its media assets, including A O l, Yahoo and TechCrunch to the private equity firm, Apollo Global Management. And Apollo integrated them into a new entity called Yahoo Inc. So that's why I went to TechCrunch. And I was talking to Yahoo. The next thing that caught my eye in that popup was their term technical identifiers, which the notice was hoping I would be willing to allow them to share and sell. Seems we should know what those are. The term in that pop-up was also a link, which took me to a Yahoo page titled, collection and Use and Linking of Technical Identifiers where they write. Yahoo uses meaning TechCrunch, because that's the parent Global, uses different technical identifiers to make its consumer services available on most platforms, browsers and devices. And again, right.
(01:24:43):
To make its services available. Well, they, they work just fine without those, but no we need those technical identifiers. Sorry, I didn't mean to editorialize. Yeah, they, they, they continue. Yahoo also uses these technical identifiers to provide our digital advertising services on our properties and for our business partners as detailed in our cookie policy. These technical identifiers include browser, cookie identifiers, sometimes referred to as cookie IDs and browser local storage identifiers, mobile device identifiers such as the Android advertising ID or the Apple identifier for advertising I D F A platform or operating system based identifiers, such as those offered on smart or connected TVs or media streaming devices. Partner supplied, technical identifiers, encrypted, or one way cryptographic hashes of personal information such as email addresses, phone numbers, account identifiers, derivatives, or escalated versions of these identifiers. Now, of course, when you cryptographically hash something like your phone number, it becomes a, an identifier for you.
(01:26:01):
Not, not of you, but a and enabling cross everything association of you. And of course, email addresses, phone numbers, account identifiers and so forth. Household based identifiers, IP addresses, probabilistic, non-unique identifiers, right? Like, like fingerprints. They can't be sure that's you, but, eh, close identifiers generated from the com from the combination of various device, browser or operating system attributes such as the operating system or browser version, cohort audience, or group identifiers such as sports enthusiasts. Okay, that won't work for me, but you get the idea. The storage generation and collection methods of these identifiers may also vary depending on the context. For instance, some browsers and devices offer limited technical identifier support and or limited cookie support. So non cookie based identifiers may be used in these cases. Example of these devices include smart or connected TVs over the top O T T streaming devices such as Roku device and similar interactive media players, digital out of home, D o O H billboards and similar media devices.
(01:27:20):
Browsers enable with intelligent tracking prevention, I T P Privacy Sandbox or similar cookie blocking technology. Oh, no. Certain apps, mobile devices or installed software where permitted and applicable certain internet of DI device, internet of things, devices. In other words, every effing thing we could <laugh>. Everything you got. Yeah. We paid, we have rooms of techies trying to find some way to track you, hook onto you see where you went, what you're thinking, what you like, what you're doing. We want it all collection. This is a great document. 'cause They're basically, I mean, they figure nobody's gonna read this, but they're revealing everything, right? They just, yes. I mean, it's really telling. Yeah. Yes. It, it is. Every freaking thing we, we, every, anybody we ever had was able to think of. So they say the collection methods for technical identifiers and, and remember that's what they wanted me to click.
(01:28:22):
Okay. Yeah. Let's you know, let's go. And the collection methods for technical identifiers and associated data depend on the context as described here. When using the internet in a browser, for example, Chrome, our consumer services and digital advertising services may use standard cookies, JavaScript code libraries. Well, that's rather generic, but, okay. And or dynamic H T M L tags, web beacons, and similar technologies in mobile apps. Our consumer services and digital advertising services may use mobile software development kits. Again, generic, local or remote application programming. Same and similar client or server side code. In other cases, we may exchange data and files such as log files with our partners in offline context using secure server to server transfer methods, APIs, cloud services, mutual agents or technology services providers may be alien technology, who knows. And other industry standard methods, technical identifiers may be used to identify a user across multiple devices, often referred to as cross device linking or cross device identifier resolution.
(01:29:38):
And as a result, technical identifiers that are presumed to belong to a particular user, device or household can be linked to one another. And the associated technical identifier may be used to reference data, personalized advertisements or tailor experiences. This process may be implemented and used by us, or in coordination with our advertising partners as part of our digital advertising services. Just click yes here to proceed. Oh my Lord. So in short, technical identifiers, fires, amounts to pretty much anything and everything they can possibly get their hands on to track me and associate me with any members of my family and presumably coworkers through instances of shared IP addresses, tracking us across any and all of our devices using every trick and technique that's available to them. Thank God I said no. But also, thank goodness I was asked and had the opportunity to say no.
(01:30:47):
Good point. Not everyone is given the option. You have to ask for it. And we have California's state legislature and Attorney General as well as those in Colorado and Connecticut to thank for this. I'll explain all that in a moment. But this is certainly not my first visit to TechCrunch. Recently, I've been popping over to TechCrunch from time to time with Firefox, following links to news to share with this audience. And this is the first time I've ever seen that popup. So this is new behavior. I received that notice because ever since we first talked about this in May of 2022, my Firefox browser has been broadcasting the standardized G P C global privacy control signal to indicate that I do not wish to have my online experiences enhanced. Thank you very much, at the cost of my, my family's and my company's privacy. Okay.
(01:31:57):
Before I move on, I need to that while digging deeper into what was up with TechCrunch, I followed TechCrunch's, your privacy choices link, which you can find at the bottom of their pages. The first interesting thing is that the right hand side of the page has specific subpage for California, Colorado, Connecticut, <laugh> as I uhhuh, interesting as I as uhhuh as I mentioned before. And there's also one for Virginia. Hmm. The California page I was taken to has two switch settings. Oh, and I should also note that somewhere I did see something about IP geolocation, which is obviously how they decided that I'm in California, right? Because I hadn't logged into them. So that's going on also. But I, and I tried to go back and find it, but I couldn't. So anyway, the California page I was taken to has two switch settings due to my previous reply to the popup.
(01:33:02):
The first one was turned off and was set to don't allow that, corresponded to quote, allow the sale and sharing of my personal information. That's now off. But there was a second switch and it was still turned on and set to don't limit. And that one corresponds to quote, limit the use of my sensitive personal information. And, and the page explains. And, and Leo, if you go to TechCrunch and scroll to the bottom and click on your privacy choices, you'll see this. So under this limit, the use of my sensitive personal information, the page explains, in connection with providing our services, we may use sensitive personal informa, get, listen to this sensitive personal information such as precise location data and email content data among other purposes. We use such data to help understand, oh, both the ears are on to help understand your interests.
(01:34:15):
So we can show you more relevant ads and content. Look how long it's taking and turn it off. This is definitely wait for 30 seconds before refreshing page. Holy cow. Actually, I think you'll find Yahoo. The, the Firefox has died. Now. I don't think you can close that tab even worse. I don't There's anything you can, oh my gosh. There's anything you can do. <Laugh>, I broke. You broke Firefox. Wow. Yeah, they really don't want you to turn that off. Oh my goodness. Uhhuh, don't flip that. How did you turn on your global privacy control? How is, is that now a switch in Firefox or is it automatic? Yes. Okay. Yes. It's a switch Firefox. And I presume that if you find it and turn it on and then go back to TechCrunch, you'll get the popup experience that I got. So that would be interesting to see.
(01:35:07):
Do I have to do about config? That's how we did it last time when we talked about this last time. I'm sure it's there. Yes. About config and then maybe just in, in, in the search box, you know, maybe G P C or, or type global privacy. Yeah. And see if it, if it, if it finds it. Yeah. Okay. So they, so they, they, they said to opt out of the use and limit our use of such information. That is my sensitive personal information to only those purposes per get. This only those purposes permitted by California law select limit. This may make the content and ads that you see less relevant to you. Oh, boohoo, <laugh>. Okay. So after doing some additional research, I figured out what's going on for anyone in California and, and to, and, and, and to some other degree, the other states.
(01:36:03):
Why Yahoo is showing two switches under the California con. And you found it in, in Firefox found. Yeah. Yeah. And now I wanna enable it, and now it's enabled. Now let's go to TechCrunch. Haha. See what they say. Wow. You know, I go to TechCrunch every day. Nothing so far didn't get to pop up for me. It, it, it, it grayed out. So it'll see, it'll be interesting to see if it's some point since you do go every day and presumably your presumably it sees you in California. Yeah, it does. 'cause I'm getting California privacy rates. Ah, ah, good point. Yeah, exactly. Yeah. Right, right, right. But if every time I turn this off, it crashes. How about if I limit the use of my sensitive personal information? Oh, oh, this is so bad. Badly. THEC needs, needs to jump right in on this.
(01:36:57):
This is terrible. It is so bad. Oh my goodness. Okay. So I figured out what's going on for anyone in California and why Yahoo is showing two switches for us under the California Consumer Privacy Act. C C P A, California consumers have the right to opt out of the sale and sharing and the use of their personal information. Okay. Those three things, sale sharing and use. But the global privacy control as it is presently defined, and it's quite unlikely to ever have its strength. Broadened only applies to those first two of the three personal information sales and sharing. The G P C does not also cover the use of personal information, but California law does. So if Californians want to prohibit the use of their personal information beyond its sale and sharing, which can be done globally with the G P C setting, that will still need to be done on a site by site basis.
(01:38:08):
So, and Leo, one thing you might try is restarting Firefox. Oh. Having just close it all out. Yeah, you're right. Yeah. H having, having start over, having put that on. Yeah. Yeah, you're right. Yeah. Be because now that your G P C is on that upper switch in NT should really not be on Yeah. That mean, because your browser is now shouting. No, no, no. Do not. And California law requires that this be obeyed. We can only hope that there are massive penalties for not, because I restarted it and I'm still getting a normal page. Let me try one more time to switch that switch, geez, Louise. Or see if the switch is, is already flipped for you. Oh, yeah. Good. Okay. Yeah. Lemme check. Yeah, it ought to be, it ought to be turned off. Oh, okay. I didn't get any popup though of saying anything.
(01:39:00):
No. All right. Let's see. Is it already turned off? Nope. Oh boy. <Laugh>. Nope. They're just ignoring it. And of course, if I click the button, <laugh>, we'll be back later. Bye-Bye. Okay. So here's how the G P c, the, the, the topic of today places itself it's need and the role it's filling. It's the GPCs formal specification explains, building websites today often requires relying on services provided by businesses other than the one which a person chooses to interact with. The result is a natural consequence of the increasing complexity of web technology and the division of labor between different service providers. While this architecture can be used in the service of better web experiences, it can also be abused to violate privacy. While data can be shared with service providers for limited operational purposes, it can also be shared with third parties are used for behavioral targeting in ways that many users find objectionable.
(01:40:11):
Several legal frameworks exists and more are on the way within which people have the right to request that their privacy be protected, including requests that their data not be sold or shared beyond the business with which they intend to interact. Requiring that people manually express their rights for each and every site they visit is however impractical. And then the spec quotes the attor, the California Attorney General saying, given the ease and frequency by which personal information is collected and sold, when a customer, a website, consumers should have a similarly easy ability to request to opt out globally. This regulation in California offers consumers a global choice to opt out of the sale of personal information, as opposed to going website by website to make individual requests with each business each time they use a new browser or a new device. So the spec says the specification addresses the issue by providing a way to signal through an H T T P header or the dom the document object model, a person's assertion of their applicable rights to prevent the sale of their data, the sharing of their data with third parties, and the use of their data for cross site targeted advertising.
(01:41:54):
This signal is equivalent, for example, to the global privacy control in the C C P A regulations. And so what's, and also subsequent to the passing of the regulation, the Attorney General formally acknowledged or asserted that this G P C signal is within the scope of what California considers a global assertion. That an an individual wants this, you know, this to hold. Okay. So what's also annoying though, now that I've woken up to this, is that I should have never received that popup in the first place. My browser's G P C setting is not the default, and it's not even available from Chrome without an add-on. So if a browser is broadcasting it, and for example, yours hadn't been Leo, if a broadcaster, if a browser is broadcasting it, it's because this is what its owner meant and wants, which means that the pop-up I received was tech crunches.
(01:43:07):
Are you really sure this is what you want here? Would you consider changing your mind? Pretty pleased with a cherry on top. I'll also note that all four of the states that have enacted G P C specific legislation have differing definitions and language in their laws. So each of those four pages where TechCrunch's Parent Company Yahoo, is juggling legislation differs from the others. This means that we now have state by state privacy laws, and that Yahoo is desperately clinging to the leverage of every bit of personal information available. Its sales sharing and internal use that they can on a state by state basis. Okay, so now let's step back a bit to get some perspective on the whole global privacy control issue. I found a great write-up at a site called Firewalls. Don't stop dragons <laugh> dot com. And the guy gets ev most of this right?
(01:44:17):
And I, I'll, I'll note where he made a couple mistakes, but he writes, you are tracked mercilessly today. When you surf the web, either on your computer or your smartphone websites, use several different techniques to identify you and record as much data about you as they can. While marketers will claim that you have the power to opt out of most tracking, this is frankly impossible to do. Practically speaking, there are simply too many trackers, many of which you'll never know about. There's a newish initiative that aims to address this problem called Global Privacy Control, or G P C G P C is a browser setting that lets you automatically tell every website you visit to stop collecting your data. Sounds good, right? But it also may sound familiar. Back in 2009, a group of researchers had a brilliant idea. Why don't we give users a way to tell every website they visit that they don't wanna be tracked?
(01:45:25):
They came up with a simple, global, do not track d n t flag that users could set on their web browser once and forget it. Their browser would in turn tell every website they visited that they did not wish to be tracked. The obvious problem here is that websites at that time were under precisely zero obligation to comply. But there were also a couple of interesting twists to the story. At one point, Microsoft took it upon themselves to automatically enable the D N T flag for Internet Explorer. Users, advertisers were outraged because the flag was supposed to be an affirmative action taken by the user. They used this move as another reason to ignore the flag. And in an ironic twist, the very fact that your browser set this flag now made you more trackable. It turns out that D N T was a little ahead of its time without any legal reason to comply.
(01:46:34):
It never caught on and was eventually abandoned if it had only held out a bit longer. It might've been relevant. The European Union's General Data Protection Regulation, G D P R was just coming online around the same time D N T was abandoned. However, the G D P R user consent verbiage didn't seem to explicitly recognize D N T enter global privacy control. From everything I can see he wrote, it's really just D n T 2.0. However, this time there are legal requirements, at least in some regions to actually require compliance. In particular, the California Consumer Privacy Act, C C P A and subsequent California Privacy Rights Act, C P R A have explicit language requiring sites to honor these automated requests not to be tracked. Similar laws have been passed in Nevada, Utah, Colorado, Virginia, and Connecticut, with others coming G P C may yet succeed where D N T failed.
(01:47:55):
Okay, now I'll pause here just to note that just as the terms do not track and global privacy control sound like different things, indeed they are. So, as much as I like what this author is written, everyone who follows this podcast knows that I'm a stickler for detail. So when he says the G P C is really just D N T 2.0, that's only true in as much as it's a global beacon that browsers can be configured to send that part of G P C is the same as D N T. But just to be clear, G P C is explicitly not about tracking, as I've been careful to say. It's about prohibiting the sales and sharing of personal information. This author continues to make some good points, however, about how to enable global privacy control. He writes, this is not a slam dunk for one thing, there is no US Federal Law requiring companies to respect G P C.
(01:49:01):
Also, the G D P R interpretation of G P C sadly seems a little weak. Well give 'em a little time. I bet they'll fix that. There are still too many regions that have no privacy regulations and the various regulations that do exist need to be harmonized with one another on what G P C really means. For example, does the request apply only to further data collection or should it apply to data already collected? Does it apply to the user or just the device that set the G P C flag? If you're lucky enough, he writes to live in a region that has privacy laws, it's a no-brainer, just enable it. But even if you don't, there's no reason shouldn't go ahead and register your desire not to be tracked, and which I'll correct to remind everybody not to have your personal information sold or shared.
(01:49:58):
But otherwise, he's right. He says, then whenever and wherever this request is required to be honored, you'll get the benefit. And he said he finishes. Thankfully, it's pretty easy to do. And if you're already using privacy tools, you may find that G P C has already been enabled. The test is simple. Go to the Global Privacy Control website. If you see a green dot and G P C signal detected at the top, you are good. And so that it, the site is global privacy control.org. Just go https slash slash global privacy control.org. And there, there's a little banner that you get at the very top. You should see a green dot if to confirm that your browser is currently sending that out. Oh, and Leo, that's, that's not, which is why Interesting. Perhaps was getting Yes. Yeah. Good. Okay. So now Google how to enable G P C for Firefox.
(01:50:55):
Yeah. while I keep going here, I turned on the, in the, about config, but I guess that wasn't enough. We'll have to, there must be something else. Yeah. Yeah. So Colorado's Privacy Act, the C P A and Connecticut's Data Privacy Act, the C D P A both recently went into effect, oh, there's two options. That's why I have to do both. Good. Okay. They both went into effect on July 1st, right? So, ju only like a little over a month ago. And like California's C P R A, those states legislation require companies to honor the G P C, but Virginia's apparently doesn't. So that's unfortunate. Virginia has some laws, but it's not, it didn't like in it, it didn't anticipate G P C. So you got two things there. Now, there, now they're both enabled. Ah, okay. And so first go to global privacy control.org.
(01:51:47):
Make sure, yeah. And see you get Green Dot mm-hmm. <Affirmative>. Okay. And then back to Tech Crunch. Yeah. Global. So today, Firefox Brave and the DuckDuckGo Privacy Browser all support the G P C as for browser extensions for Chrome and other chromium browsers that do not yet natively offer. Yep. Yep. You're, you're Green Network. Green Light. Cool. All right. There's Abbe, which is from the Delete Me people. I, I think a sponsor of the TWIT Network. Yes. disconnect Opt Meow. Where Meow Remember is the Cat's Meow <laugh>. So O P T M E O W T opt me Out and Privacy Badger, which, and that's the name I just hate. But that's from the E F F <laugh> Badger. Really? Badger couldn't like, you know, it's like a honey badger. It just just doesn't give up. How about PRI privacy fairy or something?
(01:52:41):
I don't know. But not, not badger. Anyway, I have a link here at the end of the show notes to the G P C page, which maintains a list of available extensions. So at the moment, those in California, Colorado, and Connecticut, the three Cs have the advantage of state laws which compel compliance with their residents. G P C request. Bravo. It doesn't appear that websites serving Virginians, which does have similar privacy laws, are similarly bound to follow the G P C signal. But what we need now that the G P C exists and is gaining some traction will first be for additional states, which is easier to do, to step up and add their voices with their own statewide legislation. Then we need the US federal government to take this initiative national. At that point, everyone will be on equal footing with the ability to opt in to this and thus opt out of having your, your, your personal data sold and shared.
(01:53:48):
And then we can imagine a day when a federal law won't require the presence of A G P C beacon. Well, we could dream, can't we? Leo, you and a may you, and I may not see that day <laugh>, but maybe our grandchildren, well, I don't have any, but you know, nor do I, we certainly will <laugh>. You will. Yeah. Yeah. Very good stuff. And gosh, I hope you're right. That's all I can say. If, if nothing else, it's, it doesn't look like it's gonna die. California Colorado and Connecticut are requiring it as a consequence of my having turned it on. I got the, I got the popup with, with Yahoo saying, are you sure? And boy am I glad I was asked. So it, it'll be interesting to hear back from our listeners as they experience the effects of having this turned on.
(01:54:44):
I can't imagine why everybody would not turn this thing on. Yeah, yeah. I'm gonna go through all my browsers. Obviously you can't and Chrome are, but are there Chrome plugins that will let you enable it? Yes. Yeah. A bean has one and disconnect. Good is one. And that horrible privacy badger thing, I mean, horribly named. I'm sure it's a good thing. They'll let you turn it on in Chrome. 'cause Google doesn't want this, but no, they'll, we're gonna make them <laugh>. It's gonna, and Yahoo. It's still spinning <laugh>. Oh my Lord. Oh yeah. Who knows. You know, I turned off all of the tracking protection. 'cause You know, I to say Firefox is very good tracking protection, disabled, all of that. Yeah. Turned off. You block origin for it. John was just wanted to ask. Yeah, no, turn it off.
(01:55:38):
What about starting it up? There's like a startup with no extensions option. I might, I might have to do that. It starts up, it starts up clean, and we also have quite a bit of stuff in our, you know, network. Our company network. Well, Leo, it happened to me. I couldn't do it either. I, I got that thing. I couldn't even close the page. I had to go into task manager and abort the process to get out. Wow. I can at least close the page, you know, able page, we have, you know, so many and rightly so, perimeter protections on here and stuff. I just don't know if it's something we're doing or something they're doing. It doesn't look like they're compliant right now. 'cause When I go to techcrunch.com and click the Privacy choices, those switches are still on, and I cannot turn them off.
(01:56:20):
And your and your browser is broadcasting a, it's insane. You know, an F off signal. It's really frustrating. So frustrating. Okay. But Steve, see if we listen to the show, right, we know we are informed. And that is the first step into changing the world. That's because of this guy right here. Steve Gibson. Grc.Com is his website. He has the podcast there. He actually has the normal 64 Kilobit audio. He also has 16 Kilobit audio for the bandwidth impaired. And he's got those great transcripts that Elaine Ferris writes. And that is a nice thing to have. If you wanna follow along as you listen or search all of that@grc.com while you're there, pick up a copy of Spin, right? Steve did not mention it this week, but it is there. 6.0 I I I, I thought Sunday night that I was going to have the first fully functional soup to nuts, windows and Doss all integrated, ready to go to te for the gang to test.
(01:57:23):
And I, but two things didn't work when I gave it my own first test. And I ran out of time. So it's really close, so close. But you know what, that would be incentive to go right now to grc.com. Get spin, right? The world's best mass storage, maintenance and recovery utility. You got six. Oh, and when six one comes out any minute now, well, you, first of all, you could be in on the beta, which would be great. And then you can get the final version, all of that for free if you buy today. Grc.Com. We have of course, audio on our site, but video as well of the show at twit tv slash ssn for security. Now, get it. There's also YouTube channel, clever. Hey, we're really thinking here. There's a Security Now channel on YouTube. You can also subscribe in your favorite podcast player that's recommended.
(01:58:12):
That way you'll get it automatically the minute it's available. I want to encourage everybody to join Club twit. Club Twit proceeds help keep this show alive, all the shows we do, and a lot of security. Now, people don't want trackers. They're very privacy focused. What a shock. The best way to ensure that is to do the ad free versions available to Club Twit members, ad free, tracker free just from us, direct to you. Nobody involved. And I think that that's, you know, seven bucks a month is a good deal. Just for that reason alone. If you just want security now without ads and trackers, 2 99 a month you get lots of other benefits, I think the club is really worth it. But mostly you do it because you, you wanna support what we're doing. I, I don't take any of that money.
(01:58:57):
It all goes to our hosts, our staff, keeping the lights on, the camera's rolling. TWIT TV slash club twit TWIT TV slash club twit that is the address for the club. Club twit members do have their own Discord chat. They can chat in about this and everything else on their minds. If, if you're not a member, you can also go to our IRC at IRC TWIT TV Club Twit forums, I'm sorry, the TWIT forums, 'cause you don't have to be a club member to join are at TWIT community. Those are our great discourse forums. And we also have a Mastodon instance at TWIT Social. Both the Mastodon and the discourse are open to the public. So just go I do have to approve you just to keep spammers out and you'll have access. And that's a good way to leave comments too, is at the TWIT Community Forums or on our social page.
(01:59:48):
I think that's all the business. Steve, have a wonderful week and we'll be back right here next Tuesday, one 30 Pacific, four 30 Eastern, 2030 U T C for security. Now see you on the 15th. Bye. It's midweek and you really wanna know even more about the world of technology. So you should check out Tech News Weekly. The show where we talk to and about the people making and breaking the tech news. That's the biggest news. We talk with the people writing the stories that you're probably reading. We also talk between ourselves about the stories that are getting us even more excited about Tech News this week. So if you are excited, well then join us. Head to twit tv slash tnw to subscribe.
Speaker 3 (02:00:31):
Security now.