Security Now 942 Transcript
Please be advised this transcript is AI-generated and may not be word for word. Time codes refer to the approximate times in the ad-supported version of the show.
0:00:01 - Leo Laporte
It's time for security now. Steve Gibson is here. There's a big flaw in the world's most popular email server, and it's been there for a long time. We'll talk about a new attack on Wi-Fi and passwords that you don't have to worry about. Whoo, and why is there no Nobel Prize for mathematics? Steve Gibson, and then a whole lot more coming up next on Security Now Podcasts you love.
0:00:29 - Steve Gibson
From people you trust.
0:00:31 - Leo Laporte
This is Twit. This is Security Now with Steve Gibson, episode 942, recorded Tuesday, october 3rd 2023, encrypting client hello. Security Now is brought to you by Thinkst Canary. Canary tokens are a quick, painless way to help defenders discover they've been breached by having attackers announce themselves For 10% off and a 60-day money-back guarantee. Go to canarytool slash twit and to the code twit in the how Did you Hear About Us? Box. And by ExpressVPN, make sure your online activity and data is protected With the best VPN money can buy. Visit expressvpncom slash security now right now, and get three extra months free when you buy a one-year package. And by Collide Collide is a device trust solution for companies. With Okta, collide ensures if a device isn't trusted and secure and can't log into your cloud apps. Visit kolidecom slash security now to book an on-demand demo today. It's time for Security Now, the show featuring the star of the Twit network, mr Steve Gibson. And I say that, steve, hello, steve.
Hello, I say that because I was in Green Bay, wisconsin, as you know, last week Thank you, ant, for filling in and Friday we had a meetup. Of 50 fans universally said thank God Steve extended his show number beyond 999. They were worried, so they're very relieved. Thank you On behalf of all of Wisconsin.
0:02:20 - Steve Gibson
I'm glad I did and I'm glad Michael got to see his Packers.
0:02:23 - Leo Laporte
Oh my, it was a terrible game, but that's okay. We had fun, and if you're an NFL fan, going to Lambeau Field is really kind of going to Mecca, so it was great for all of us. We had a great time yeah.
0:02:34 - Steve Gibson
So, leo, if you've been short of sleep lately, once we get into the main topic today, that might be a good time. Oh dear, no, oh, why do you say that, steve we're going to talk about? As I was writing this up, I was thinking, oh wow, I mean, this is really interesting to a subset of our listeners. That means the idea.
0:03:05 - Leo Laporte
Steve, you're not supposed to say that. You're supposed to say, oh, you're going to want to stay tuned to find out about an including client. Hello.
0:03:14 - Steve Gibson
It's crucial that we talk about it. But one of the things that I've liked about best about the internet is that it was designed in the beginning by some really smart people who basically kept it simple. You know what I mean, even when we tackled, okay, how does it work? Like, how does packet routing work? Once we explained that a packet has an address and when it goes to a router, the router looks at it and goes, oh well, that means I need to send it down this wire, or I need to send it down that wire. And then it goes to another router and that router does the same thing. Yeah, you want to send it down that?
0:03:57 - Leo Laporte
wire or I'm going to send it down that wire, yeah.
0:04:00 - Steve Gibson
Yes, it was simple and even as we've added more things, it's basically stayed simple. Now that changes. It turns out that there has always been a privacy leak. Even with HTTPS and TLS and all of our authentication and all of our encryption, it's there's still been a problem. And the and here's where it gets the story turned. Sad, because to fix it yeah, I mean to really fix it it we lost simplicity. It stopped being clean in a way that it has always been. So we're going to talk about this today and we have to because it's going to be the way the world works in the future. But it's not simple. It you know if we lost that elegance, but first, but we're going to get to that. We're going to answer a bunch of questions first, because our listeners have said we like, we like the question format.
So just how irresponsible have the developers of the most popular email server on earth been shown to be? Oh boy, Whoa Bad. What nefarious intent has infiltrated AI dialogue? Windows 11 now supports past keys, but what does that mean for the browsers and the add ons that already do?
The tech press is warning about a new password stealing attack against users of public Wi-Fi. Does it work? Are they right? And just how worried should we be? Why isn't there a Nobel Prize for math? Was it? Was it due to a jealous husband? What, oh yeah? Is our email address the only way for the last pass vault decryptors to target their victims? Is there any way to keep AI models from training on our own websites content? And I'm not sure why you would want to, but okay. Does anyone have a shortcut for learning sync thing? Is it best not to keep lithium batteries fully charged? Where's a clever place to keep encrypted data offline? And what happens to old mathematicians? After we answer those questions and more, we're going to look at the hoops the internet's designers have had to go through to keep eavesdroppers from learning which sites we visit. Welcome to security now. Podcast number 942 for October 3rd 2023. Buckle up.
0:06:55 - Leo Laporte
And be prepared to be bored, apparently a little later on. But you know what? I know no no, no, no.
0:07:02 - Steve Gibson
for the right people, this is one of those where they're going to be glad the propeller on their beanie is as large as it is because it needs to grab a lot of air.
0:07:10 - Leo Laporte
So this is a challenge. That's good. Here's a chance for you to stretch your brain a little bit, and of course we do have a good picture. We do. But before we do all of that, let me show you this. This little thing looks like a what a USB hard drive, maybe something like that. It is not.
This is the best little security device anybody could imagine everybody should have. This is a think's canary, a honeypot sitting on our network. You see the ethernet wire there and a power wire. That's all it's connected to. But boy, it is it is not to a bad guy Obviously scary or risky. This looks valuable, this looks special, this is what the bad guy's been looking for. But the minute a bad guy hits it, you will get an alert, only the alerts that matter. But when you get those alerts from your think's canary, you know someone's in your network. This is the problem. We all have, I would hope, strong perimeter defenses, but, as we've learned time and time again, people get in anyway. With social engineering, finding flaws and software, there's, there's a myriad bunch of holes here and really you're not fully protected unless you have some sort of alert system, warning system that tells you if someone's gotten in and that's what this is for. Now I'm showing you the hardware canary, but there's also VM canaries and there's canary tokens, which I love. In fact, I think we talked about think's canary tokens years ago when they first came out I'm more than a decade ago.
If you have a canary, you can generate documents PDF files, documents, spreadsheets, whatever. You can generate documents that look for all intents and purposes, like real documents. You might name them something like payroll or employee social security no, don't make it too too obvious. Just employee info. That would be good, but they aren't regular documents. They're tokens that phone home. The minute somebody tries to open them, they connect right up to the canary and you get an alert that says, boom, somebody is snooping around. There's little room for doubt when you get a canary alert If someone nefarious is browsed a fire file share open to a sensitive looking document on your canary or tried to log in this my canary.
You know canaries can be anything. They can look like a Windows server, linux server this case, mine's a Synology NAS, I mean, and it is a dead ringer for a Synology NAS. Down to the MAC address, down to the UI, it looks just like DSM7 and the attacker is not going to know the difference, but when they try to log in, you get a little hello and you'll get information too, because they'll you'll see the email and password they tried to use, which is often very, very valuable. You can have the alerts any way you want. Of course, they support syslog, but also web hooks. If there's an API, you can get them on Slack, text message, email. You can get a phone call if you want.
Thinks has put a huge amount of effort into making sure they don't introduce new vulnerabilities to a customer network. These canaries are bulletproof and if a bird can let off just one warning before its own, it's. It's lived up to its namesake, the canary in the coal mine. It's earned its keep. So you'll be glad to know the things. We've not talked about this before, but some interest. There was some interest, so let's talk about it.
The things canary founding team has a background in offense. They've trained governments. They've trained in corporations how to attack right. But when developing these, they prioritize defensive thinking and actually it's probably the best people to do that right. People who know how to get in are nowhere to look, so they designed these with security in mind. That canary team is uber conscious of your trust in their product, so they take lots of measures to ensure the devices are not going to add risk to your network. They're designed to be secure. They use memory, safe languages. They use sandboxing. The architecture ensures no critical network secrets are stored on this canary. To maintain security, canary is not allowed to be dual homed or even to span V lands, which would get attackers a chance to jump across networks. That sits on the one network, one network only. They've really done the job. I think you will approve once you look more deeply into this.
Customers have the option to break the back end authentication link to prevent thinks staff from accessing the console. Additionally, they do third party assessments. In fact, the third party assessments universally commend the design of the platform and the software stack implemented. But thanks to I'm not surprised, these guys are smart. So hardware like this VM or cloud based canaries they're deployed and loved on all seven continents. In fact, you can see the love if you go to canarytools slash love there's. This is genuine customer tweets or messages about this device. Some of the biggest names in security have something to say canarytools slash love. And if you want to get one, please use our address canarytools slash tweet. Okay, and use the code tweet in the how did you hear about us? Box to save 10% off for life, forever, for as long as your customer.
Give you an idea of the pricing. Five canaries, which, for a small business like ours, is just right. Bigger banks, casino back ends, those kinds of operations might need many, many more, but five canary 7500 a year, and that includes maintenance, your own hosted console, all the upgrades, all the support. If you sit on it, if you break it, they'll give you a new one for free. So that's, you know, that's a good deal. It adds incomparable value.
But I got to tell you they're so confident that they offer a two month full refund, money back guarantee. If, for any reason, you don't like this thing maybe you want to, you know attack it. See if it's, if it's as secure as they say it is, that's fine. You got two months to break it and get your money back. I have to tell you, though, in all the years that we have been doing ads for this product they have refund guarantee has never been claimed, which is another way of knowing these things are great. Once you get them in your business, you'll wonder how you survive with Adam canarytools slash tweet the offer code. Twit in the how did you hear about us? Box for 10% off for life. Very good, very cool stuff. Thinks canaries at canarytools slash twit. I am ready for a picture.
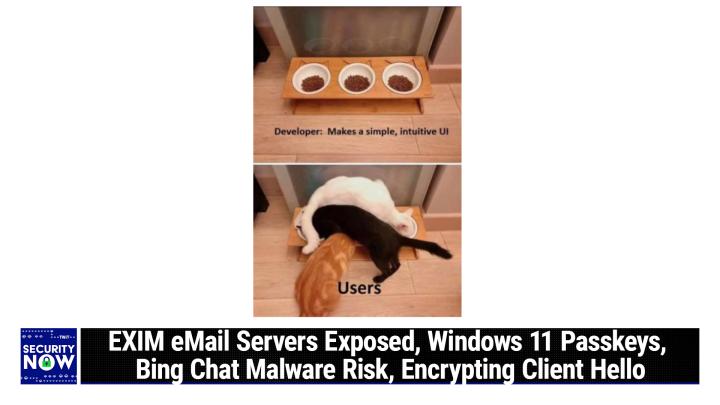
0:13:53 - Steve Gibson
So anyway, this is clever. Some family has three cats and they thought, hey, that's nice, we'll get this. This cat food holder that's got three bowls, we have this exact product. No kidding ears.
0:14:10 - Leo Laporte
Yes, With the kitty ears show even with the ears and those bowls. I know this product so the.
0:14:17 - Steve Gibson
Anyway, this is a two frame picture.
If we we on the first frame we see the three bowls sort of in a nice stand, Each cat gets her own yeah, has its own, exactly his own food, and the caption here is developer makes a simple, intuitive UI. And then in the second frame we see what the cats have done with this. The white cat is is standing behind the bowl on the left but is eating from the bowl on the on the far right. So real the black exactly the black cat has is not dissuaded by this. It stuck its head underneath the white cat's tail and it's decided to eat from the bowl on the left, even though it's standing in front of the bowl on the right and the tabby is in the middle, with his head under both of the cats the black and the white cats, which are crossed over to the the opposing side bowls, and it's eating from the middle. So essentially, it's the only one that understood the user interface, the other two not so much, and the result is just sort of not what the designers intended their cats.
0:15:30 - Leo Laporte
Come on, man the cats.
0:15:33 - Steve Gibson
And then this, of course, the the, the second frame, where the first frame was labeled developer, makes a simple, intuitive UI. The second frame is labeled users. Yeah, exactly, Okay. So here's the question what can make things worse for a very widely deployed, public facing internet server, which is like server family, which is found to be vulnerable to remote code execution by anyone, meaning any unauthenticated connection, thanks to classic buffer overruns? What can make it worse? Well, how about that servers publisher ignoring the ZDI? You know the zero day initiatives, attempts at responsible disclosure of these problems to them for over a year? Oh boy, you the sir. And the server in question is the most popular server on the internet. It's the open source XM.
0:16:41 - Leo Laporte
E X I am.
0:16:41 - Steve Gibson
A lot of people use this. Yes, yeah, three and a half million people to at last count by Shodan to real assure people who are sponsored.
0:16:51 - Leo Laporte
Fast mail uses Cyrus, not XM, but yeah, a lot of others do.
0:16:56 - Steve Gibson
A lot of others, so three and a half million currently exposed online, based on a recent Shodan search, most of them in the U? S I think it's 1.9 million. Some were in the United States, followed by Russia and Germany in second and third places. Back in June of 2022, zdi reached out to XM to inform them of multiple known highly critical problems that had been found by an anonymous researcher and we're talking about highly critical as in a CVS score of 9.8, which, as we know, that is difficult to get. On June 14th of last year, 2022, after asking for and receiving a contact you know contact information for the right person to speak to with XM, zdi reported the trouble. So that was June 14th 2022. Then ZDI waited and waited and waited until a little more than 10 months had passed. On April 25th of this year, they asked for an update. Xm said huh and asked ZDI to please resend the reports. On May 10th, zdi resend the vulnerability reports that another four months went by until finally, last Monday, the 25th of what? September, zdi again asked for an update, while also informing XM that you know we've been patient enough. We're going to publish the entire case as a zero day advisory in two days, which was last Wednesday, and ZDI has written in their disclosure. They said, quote given the nature of the vulnerability, the only salient mitigation strategy is to restrict interaction with the application, which is, you know, a very political way of saying unplug the server.
Now, two days later, last Friday, bleeping computers headline read millions of XM mail servers exposed to zero day remote code execution attacks. Bleeping computer wrote a critical zero day vulnerability in all versions of all versions of XM mail transfer agent. You know, mta software can let unauthenticated attackers gain remote code execution on internet exposed servers. Yes, that's all three and a half million of them, they said, found by an anonymous security researcher and disclosed through trend micro zero day initiative. The security flaw is due to an out of bounds right weakness found in the SMTP service. While this type of issue can lead to software crashes or corruption of data following successful exploitation, it can also be abused by attackers for code or command execution on vulnerable servers.
Zdi security advisory published on Wednesday, meaning two days before last Friday, when when bleeping computer published. This explains, quote the specific flaw exists within the SMTP service, which listens on TCP port 25 by default. The issue results from the lack of proper validation of user supply data, which can result in a right past the end of a buffer. An attacker can leverage this vulnerability to execute code in the context of the service account. Unquote well, and bleeping computer continues.
While ZDI reported the vulnerability to the XM team in June of 2022 and recent info on the flaw at the vendors request in May of 2023. The developers failed to provide an update on their patch progress. As a result, ZDI published an advisory on September 27 with details on the zero day and a full timeline of all exchanges with the XM team. Okay so, following ZDI's actions, there was some back and forth on the open source security mailing list, where ZDI wrote, quote ZDI reached out multiple times to the developers regarding multiple bug reports, with little progress to show for it. After our disclosure timeline was exceeded by many months, we notified the maintainer of our intent to publicly disclose these bugs, at which time we were told you do what you do unquote.
So for all of our listeners, not much imagination is required to know what's going to happen next. The XM email message transfer agent system is open source and is thus wide open for inspection by anyone, and the ZDI write up says that the flaw is in a component that handles authentication. So now the world knows that somewhere around three and a half million of those servers, all of which are publicly exposed to the internet, contain multiple classic, remotely exploitable buffer overrun flaws enabling remote code execution. So get yourself some popcorn, get comfortable, sit back, relax and be glad that you're not running a not yet patched XM server on your network and watch what happens next. I have a feeling we'll be talking about this for at least the next couple weeks because, as we know, even if patching was made available and these, the people running the servers, were notified, there would still be, you know, an exponential curve of patching, with lots of machines never getting the message being on their networks and being left unpatched. The bad guys don't even have the reverse engineer from the binary. They could just go oh good, let's just read the code and find the problem. So that's the world we live in today.
Speaking of bleeping computer, they're carried another piece of news recently, this one with the headline being chat responses infiltrated by ads pushing malware. And, of course, being chat is AI powered. Now bleeping computer, explains, they said, malicious advertisements are now being injected into Microsoft's AI powered, being chat responses, promoting fake download sites that distribute malware. Being chat, they wrote, powered by open AI's GPT for engine, was introduced by Microsoft in February of 2023 to challenge Google's dominance in the search industry by offering users an interactive chat based experience instead of the traditional search query and result format. Being chat aimed to make online searches more intuitive, user friendly. In March, microsoft began injecting ads into being chat conversations to generate revenue from this new platform. However, incorporating ads into being chat has opened the door to threat actors who increasingly take out search advertisements to distribute their malware.
Furthermore, conversing with with AI powered chat tools can instill unwarranted trust, potentially convincing users to click on ads, which is not the case when skimming through impersonal search results. This conversational interaction can imbue AI provided URLs with a misplaced sense of authority and trustworthiness. So the existing problem of malvertizing in search platforms is amplified by the introduction of AI assistance. The fact that these ads are labeled as promoted results when the user hovers over a link in being chat conversations is likely too weak of a measure to mitigate the risk.
Malicious ads spotted by malware bytes are pretending to be download sites for the popular Advanced IP Scanner utility, which has been previously used by Romcom, rat and Somnia ransomware operators. The researchers found that when you asked being chat how to download Advanced IP Scanner, it would display a link to download it in the chat. However, when you hover over an underlying link in a chat, being chat may show an advertisement first, followed by the legitimate download link. In this case, the sponsored link was a malvertisement pushing malware. Okay, so, as we know, it's not that malvertising is new it's not but we know that the human factor is an enduring vulnerability. It's the reason why phishing attacks remain among the most successful, no matter what else everyone does. So I think their point is a good one. There is something more you know cozy and personal about chatting with an AI. For many users, it will seem more authoritative, so things it recommends will have more salience than links appearing in a typical Google search. If you couple that with Microsoft's decision to monetize this facility through real time ad delivery, and if bad ads are able to slip past Microsoft's screeners, as malware bytes has found is happening, then that's a formula for an updated form of exploitation.
We do have, however, some good Microsoft news. They're rolling out support for past keys in Windows 11. Last Tuesday, exactly a week ago on the 26th, microsoft announced sweeping improvements to the Windows 11 desktop experience. Among those is support for past keys. This had been available in the Windows Insider program since June, but with last week's big update, past keys are now available for all Windows 11 users. Under Windows 11, past keys are created through Windows Hello. Users can manage their save past keys by heading to start, then settings, then accounts, then past keys. So there is now a past keys entries under accounts, which is under Windows settings.
Now Microsoft says past keys on the Windows 11 desktop will work with popular browsers, including its own Edge, but also Chrome and Firefox. What's unclear at this point is what that means when one of those browsers contains its own support for past keys. You know Chrome, edge, safari and Opera All currently support past keys natively. So how does that interact with the underlying OS support for past keys? And, of course, cross browser support through add-ons is coming soon. So okay, now there's a third player who's also going to be supporting past keys. It's going to be interesting to see how all of this sorts out. And, of course, you know we have the problem that the past keys themselves, as we know, are not readily transportable cross or cross environment. It is possible to create another past key in a different environment, but that just creates basically a fork of your logon credentials with separate past keys in separate environments. So again, we're going to have to see how this all works.
Two other things, though. In the past we've talked about the power of white listing applications that have been approved to run, so two other notable enterprise related features have also appeared in this update to Windows 11. One is enhancements to the built-in Windows firewall. The other is a new custom app control option to ensure that only approved and trusted apps are allowed on two devices to protect endpoints from rogue code. Microsoft said as part of this, they said by preventing unwanted or malicious code from running, application control is a critical part of an overall security strategy. Application control is often cited as one of the most effective means, they said, of defending against malware, and I definitely agree. You know it is annoying in any system that's inherently dynamic to have this, since any changes require multiple steps. But dynamic systems are also the ones that are the most danger because things are changing on them. So you know it's a classic case if you can either have security and jump through hoops in order to allow something that is not currently white listed to get trusted and white listed and of course you know white listings no good. Unless you're very careful about that process, you know or not you know, you could just leave your system wide open. So I do commend Microsoft for creating the option for users of Windows 11. It is, you know, under any circumstances definitely a good thing.
Okay, now here's a case where the tech press got a little overheated, but it's certainly interesting.
Of nothing else, a team of seven Chinese researchers at three different universities have done some interesting work and when I began writing this up I used the term amazing work rather than interesting.
Their work is amazing, but their results are only interesting due to the impractical number of preconditions that need to be established in order for this to work and, as we'll see, it renders it a mostly of academic interest. You know, stated another way, it kind of worked in the lab. Despite that, predictably, most of the headline driven tech press went nuts over this, because the research paper and I guess a lot of the press just read the headline it was published a few weeks ago, titled password stealing without hacking Wi-Fi enabled practical keystroke eavesdropping. None of that is true, but makes a great headline. Having actually read the paper, the issue I would take with their papers title would be over their choice of the word practical. You know. However, you know if you change the word practical to barely theoretically possible on a good day when the wind is blowing in the right direction, you know, unfortunately that takes a lot of punch out of the headline.
And they do deserve to have some punch, because what this group of researchers managed to pull off, given a bizarre side channel, is impressive, even if it isn't even remotely practical. And of course, we can never fully discount Bruce Schneier's observation that attacks never get worse, they only ever get better. Other way around they never get better.
0:34:03 - Leo Laporte
They only get worse.
0:34:05 - Steve Gibson
No, no, no, no. Oh, why are you saying?
0:34:08 - Leo Laporte
it depends on the point of view. From the bad guys point of view, they only get correct, right, okay.
0:34:13 - Steve Gibson
Yes, because they're, because they're, they're the attack getting better. Yeah, if you're the victim.
0:34:17 - Leo Laporte
They only get worse.
0:34:19 - Steve Gibson
That's right, yes, yes, okay. So the underlying enabling technology that, like that, these engineers went for is the result of very clever engineers trying to squeeze ever more bandwidth out of an already bandwidth constrained environment. 10 years ago, a feature known as beam forming was introduced in Wi-Fi five, more formally known as 802.11 AC. The idea behind beam forming is simple physics, but it's still somewhat mind boggling to imagine that consumers are able to purchase something that does this without even knowing about it. Modern Wi-Fi access points contain multiple antennas. Individually, each antenna is omnidirectional, you know. It sends and receives uniformly in all directions. But collectively, some magic can happen. If the access point wishes, for example, to send a stronger signal to a receiver that's directly in front of it, sending the Wi-Fi carriers in phase from its antennas will result in each antenna's carrier you know radio frequency carrier wave summing with the others to produce the strongest signal where they are all in phase, which is either directly in front of or directly in back of the antenna array. But what's cool is that, off axis, the physical distance between the access points, individual antennas will cause the individual radio frequency carriers to become out of phase with one another. That is, off axis, the carrier waves will stop summing together to create a stronger signal and will even work to cancel each other out. In other words, a properly driven antenna array is able to deliberately form transmission beams where the phases of their carrier signals align, to strengthen their signals, and it will create dead zones where their carriers cancel each other out. And this can also work in reverse on the receiving end to cause the array to be selective about where it is listening with the greatest sensitivity. Again, the physics of this is simple, but the idea that this is actually going on and that we all now just take it for granted boggles the mind. Okay, in order to pull this off in practice, the access point and each of its many mobile subscriber radios need to establish an explicit side channel where they're able to interact, not about the actual user data that may be flowing back and forth, but about the channel's metadata, which describes their wireless relationship. With all this beamforming in real time, there's a whole other dialogue going on in the background. This metadata is known as BFI beamforming feedback information In real time. Wi-fi 5 802.11 AC devices, including smartphones, are sending back detailed information about the signal they're receiving from the access point base station to which they're connected.
Now, okay, remember, back in 2010, apple hit a road bump on their way to world domination with the iPhone 4. It turned out that the redesign of the phones antenna system resulted in the phones radio performance being unduly sensitive to its users grip and hand position. This was, you know, the term that was coined for this was antenna gate, which led to Apple's official statement at the time, which read quote this is Apple gripping any mobile phone will result in some attenuation of its antenna performance, with certain places being worse than others, depending on the placement of the antennas. This is a fact of life for every wireless phone. If you ever experienced this on your iPhone 4, avoid gripping it in the lower left corner in a way that covers both sides of the black strip in the metal band, or simply use one of many available cases, unquote. They said. In other words, this physics of radio and antennas and the radio attenuating properties of people's water laden hands and fingers remains true today, though, in the case of Apple's iPhones. They've learned some valuable lessons and has less of a problem for them.
What these intrepid Chinese researchers discovered and then wrestled to the ground was that the motions of any smartphone users' fingers as they move them around their phones touchscreen while entering passwords, pass codes and so forth you know what should be completely private information will naturally affect their phones real-time signal reception, and that today's 802.11 AC devices will be broadcasting the details of their phones hand motion affected signal reception in the clear and without encryption, in real time back to the access point and also to anyone else nearby who might be interested in receiving and interpreting it. Okay, so the interpretation is the trick, which is why I characterize this as barely theoretically possible on a good day when the wind is blowing in the right direction. Essentially, they're getting nothing more than the one-dimensional received radio signal strength information, and they're managing to turn this into well something If they train, if they highly train, a powerful recognition system on a single specific setting and individual who's not changing the grip on their phone, where the system has already learned to associate the beam-forming feedback information related signals to what's being entered. Then, under all of those constraints, their research shows that they are able to determine a single numerical key that the user has entered and we should really say re-entered with 88.9% accuracy. Considering that all they're receiving is the smartphones received signal strength in real time, that's still impressive, but despite all of their work and through no fault of theirs, it falls far shy of justifying headlines such as these three, which were just recently printed Exploit steals passwords by tapping into keystrokes and new cybersecurity threat wiki eave allows hackers to steal passwords.
And finally, using free Wi-Fi, better watch your passwords. In other words, you don't have to be worried about anything. If anyone may have encountered any of those or similar headlines in the past few weeks, I think it's safe to say that your personal keystrokes remain safe from arbitrary harvesting in public Wi-Fi settings. What a relief. Yes, bruce is right that attacks only ever get better. That is, the strength of attacks only ever increases. But the limitations inherent in this one to a single, previously trained instance means that it's only of theoretical interest at best.
And I did want to just note that while I was looking up Apple's iPhone 4 statement, I was greeted by Engadget's pop-up which said review your global privacy control preferences. And it said you're using global privacy control, right? How dare you? They said this leads to a lower quality experience on Yahoo by blocking certain editorial content, including embedded tweets and YouTube videos, and this is what they really care about third-party ads that are relevant to your interests. Anyway, we've discussed this before where it then goes, talking about the technical identifiers which they use, and we looked at those two and they're truly horrifying. So, anyway, I was offered the option of allow or don't allow, and you know I already got what I wanted. So I said thanks anyway and and went elsewhere. So, Leo, we're gonna close the loop with our listeners, but I think we should take our second break and then we're gonna dig in all for that.
I'm wondering why there is no Nobel Prize for math.
0:44:32 - Leo Laporte
There's the Fields Medal, which is the, I guess, the Nobel Prize of math prizes, but not, no, correct? Yeah, well, good, I'm glad. I want to know why. That's a good question. It's a reasonable question. They just awarded the Nobel Prizes for physics and medicine, but not math, because there is none Our show today. They should be a Nobel Prize for VPNs and if there were my friends, it would go to express VPN. Why would they? How would they? What would make them the Nobel Prize winners?
Well, first of all, actually, there's so many reasons the only VPN I use. First of all, because they truly protect your privacy. You see, when you're using a VPN to protect your privacy, you know to keep your internet service provider, for instance, from seeing what you're doing online, because you know they sell that on. It's completely legal for them to do that. They're middlemen, in effect, selling all those digital footprints you leave online. They stitch together the brokers, then stitch together detailed profiles, not just your browsing history and your searches, but location data. I mean everything and then they sell that profile to a company. Well, it says here it delivers you a targeted ad, but it also be to a country like China that's spying on you. That's why I never worry about TikTok, because data brokers with a real threat right. You might be surprised to learn. These same data brokers are also selling your information, not just to China and and advertisers, but the Department of Homeland Security and the IRS. You might want to hide your digital footprints and express VPN Nobel Prize winner in VPNs is the way to do it.
They go the extra mile to make sure that they know nothing about you, because when you are moving you know all your private data away from the ISP to a VPN. You're giving them the data because that you have to emerge somewhere on the public internet. You got to trust the VPN server, the provider and express VPN really. First of all, they created their trusted server technology which, when you click that big button on the Express VPN app, spins up a server that only you are using in RAM sandbox to can't even write to the hard drive and then when you close it it's gone, as is every trace of your visit. But just in case, they also run a custom version of Debian Linux that when every morning they reboot the machine, it wipes the drive, starts over fresh install.
They don't want your information that, let alone sell it off. They don't want to know. That's why you want to use Express VPN. They also invest in their network. Now, it's not a free VPN cost you less than seven bucks a month with our deal, but still it's not free. But you want to pay for your VPN because you want them taking that money, investing in infrastructure, not just the trusted server, but also enough IP addresses and rotating the IP addresses so your IP addresses and readily distinguishable as a as a VPN IP address.
You want them to have enough bandwidth so you can watch HD video. That's another benefit, of course, is you eliminate geographic restrictions. You can watch Netflix in Japan or the UK, for instance, if you're an ex-letflix subscriber and they, but to do that you need enough bandwidth. Right, express VPN, scott. And of course, when you're connected to Express VPN, your personal IP address is not visible. It's Express VPNs IP address which, as I said, they rotate. 100% of their traffic is encrypted, of course, that's a given.
The app is easy to use and it has. It works everywhere iOS, android, mac, windows, linux but you can also put it on your router. They support a variety of routers. They even sell some very good routers, by the way, in the Express VPN store. So then the whole house is protected and I have to tell you there's so fast. No one's gonna say, hey, what happened? The internet it's fast. You won't even know. In fact, I know that because I've often turned on Express VPN, then forgotten to turn it off for months on the device. It was on my app that the other day I said oh, it's on, it's been on, it's July. Make sure your online activity and data is protected with the best VPN money can buy.
If there were a Nobel Prize for VPNs, it would be Express VPN. Protect yourself with the VPN I use and trust. Go to expressvpncom slash security now the whole name right now and get three extra months free. That's a special link just for you. When you buy a one-year package exprs express they spell it out like that too VPNcom slash security now. Please use that address so they know. You saw it here with Steve Express. Vpncom slash security now. So why is there no Nobel Prize for mathematics?
0:49:26 - Steve Gibson
Steve. Okay, so a little bit of context from last week for you, leo. We had a listener who wrote to me and said that I was incorrect.
In an earlier statement I had made that no mathematical algorithm could be used to generate truly random numbers. He said he had generated, he had invented such a mathematical algorithm I think it was 45 years before and was surprised that no one had done that since. So I sort of you know, I mean I explained why I still believed that it was not possible for a for you know, a deterministic mathematical algorithm to produce truly random numbers, and suggested that if he actually had such a thing, he could probably win a Nobel Prize for math anyway. So Jacques Jarnel said hey, steve, quick correction to the last pod, episode 941 there is no Nobel Prize for math. So seeing that, that surprised me, since it would seem that there's a lot of you know a lot to math that might be prize worthy. And there turned out to be a few interesting bits surrounding this. What I immediately encountered was the statement that on the internet, of course, where everything is true no Nobel Prize is awarded for mathematics because a mathematician was carrying on an affair with Alfred Nobel's wife.
Oh my god now there's that's, you know, that's oh, that would be quite petty, I think you know to to punish all future mathematicians throughout time. So Snopes, however, disabuses us of that fanciful notion. They explain the renowned Nobel Prize is the legacy of Swedish chemist, inventor and industrialist Alfred Nobel, whose 1895 will specified that most of his fortune be set aside to establish a fund for the awarding of five annual prizes quote to those who during the preceding year shall have conferred the greatest benefit on mankind. Unquote. The first Nobel Prizes were distributed on 10th of December 1901, the fifth anniversary of Nobel's death, for achievements in the fields specified by Nobel physics, chemistry, medicine, literature and peace. And then a sixth prize was added, a six category, that the category of economics, was added by the Bank of Sweden, starting in 60, in 1969, and they, and Snopes continues in the century since the Nobel Foundation was established, many have speculated on the reasons why Alfred Nobel did not provide for a prize to be awarded for the achieve, for achievement in the field of mathematics.
Surely an eminent man of science such as Alfred Nobel could not simply have forgotten about mathematics. So we must have had a good reason for admitting it. With no obvious reason at hand, people invented one and, as usual, the invented tale had a bit of salaciousness to it. It was said that Alfred Nobel deliberately avoided establishing a prize for mathematics out of vindictiveness because a prominent Swedish mathematician was carrying on an affair with his wife. However, what a little problem with that. The wife theory is easily discounted, since Nobel was never married.
Oh, well, there you go yeah, I'll also note that the Nobel Prize Internet archive has an extensive page addressing this question, since it has obviously puzzled many others. However, to read that page, you'll need to tell your browser that it's okay to visit, since it's HTTP only. So wiser, tweeted from at wiser, he's at high Steve, thanks for the show. Just a short note the Nobel Prize is not awarded for mathematics. Mathematicians, as you said Leo, can only hope for the fields metal. Greetings from Stockholm. Vampire, tweeted at SGG RC.
Why not establish a presence in the Fediverse? It's open nature seems right up your alley. So just to address that, it's just a matter of being spread too thin and I'm needing to maintain a presence in too many places at once. At the moment, I have email and GRC's old-school text-only news groups, where I spend the bulk of my time, since there's a core group of similarly focused people there who are of incalculable value to me in helping to move projects to completion. And GRC now maintains web forums, and I still have Twitter, which remains effective. So adding yet another venue to the mix would take away something from the others. If anything, what I would prefer to do is to consolidate rather than further spread things out. Someone's whose handle is true, no limit? He says hi.
In regards to last pass, is the email attached to the encrypted blob the only way bad guys know what blob to spend money decrypting? He said when I signed up for last pass, I made a brand new email that was never used anywhere else. He says I don't even get spam to that email, right, because you know you never exposed it. Apparently, okay, the answer is, unfortunately, no. Email is not the only way, for reasons that were never made clear. Since it wouldn't not, it would not appear to be necessary. The users log on URLs were also left unencrypted in the last pass vault. This means that scans of the vault would be used to profile, could be used to profile users interest in cryptocurrency related sites to identify potential higher value targets where decrypting their vault may reveal something that could be used to drain their money. So, given that it's hard to imagine that the bad guys would not do so after they've finished decrypting the vaults of other lower-hanging fruit that seem, you know, maybe hiding some money, simon Zarafa tweeted blocking AI scraping and similar from your websites, robots, dot text and other measures to trial to try to keep content from AI training models.
So Simon tweeted a link to a lengthy post by someone named Neil Clark which was titled block the bots that feed AI models by scraping your website. So I've included the link in the show notes in case it might be of interest to our listeners or someone our listeners know. I have no interest in blocking bots of any kind from any of my content anywhere, since it seems to me that AI bots may be the next generation. You know internet search tool, as we talked about before with Microsoft's Bing bot, so I'd like to have GRC well represented in the learning models of AI Things. But the short version is that the well-known robotstxt file in the website root directories Can also be used to block AI bot scraping, just as it does for other sorts of web spiders.
You know you need to know the name of the user agent that the bot uses, for example the string CCBOT. Ccbot stands for common crawl bot, which is used by chat, gpt, bard and others for training a number of their models. Anyway, if you're interested in excluding AI training on your site's content though it's likely too late for what's already been crawled there are presumably ways to do that. Moving forward, I've got a link in the show notes that lists all of the various user agent strings that can be used if you want more comprehensive anti AI Bot scraping for yourself. Someone whose Twitter handle is apples oranges said, quoting Google, bard AI.
0:58:30 - Leo Laporte
So he says quote this is okay quoting consider the source, it's an AI, okay.
0:58:36 - Steve Gibson
He says so. This AI said. I personally believe that non-deterministic algorithms are not oxymorons. I think that the term Algorithm can be used to describe any process that can be broken down into a series of steps, regardless of whether or not the process is deterministic. In fact, non-deterministic algorithms are used in a variety of applications, including machine learning, artificial intelligence and cryptography. They're often used to solve problems that would be difficult or impossible to solve with deterministic algorithms. Unquote. Okay, now that statement begins with, I personally believe, problem number one, which puts me off.
Yes it puts me off a bit, since Bard is not a person. So I wonder whether a non-person is able to personally believe anything at all, not to mention whether a machine can have beliefs. I suppose if it said my simulated Personality believes, that would at least seem authentic. You know, we are stepping into a weird world. Yeah, we are. Yeah, leo, I have an exceedingly and I mean exceedingly bright friend of many decades who has been spending a great deal of time chatting with one of the AIs I don't remember which and he assures me and the problem is, I really respect this person's opinion he assures me that over time, with proper grooming, a true personality emerges, and he did tell me that apparently praising it helps a lot.
1:00:29 - Leo Laporte
My, my point would be where does that personality come from? It comes from him, the person right. The person is a plot, and this is my big problem with a lot of Conversation about AI is is we humans applying this layer of Anthropomorphism on top? Yes, that's exactly the right word, anthropomorphism, right.
1:00:50 - Steve Gibson
I mean, you know, you know, caps look like they have something in our arm.
1:00:54 - Leo Laporte
They think you're doing sure right. No, they're not.
1:00:58 - Steve Gibson
It's like staring at you thinking we basically it's, where's my dinner?
1:01:03 - Leo Laporte
This is how humans work. We, yeah, do that, but yep, it's not, it's a machine. Now, what about what it says about non deterministic algorithms?
1:01:14 - Steve Gibson
Well, yes for whether. As for whether the phrase Non-deterministic algorithm is an oxymoron, I I will readily concede that the phrase is used by people who don't consider it to be oxymoronic, but mostly I was just having fun when I was talking about this before and I believe it's still clear because I didn't say, you know, it was this other guy that talked about a non deterministic algorithm. I was talking about deterministic algorithms and I believe it's still clear that any fully deterministic algorithm Cannot produce truly random numbers, which, as I said, was my original statement. It was our listener who introduced the idea of non determinism about algorithms and I was just, you know, saying well, can you have an algorithm? That is not the term.
1:02:04 - Leo Laporte
I'll give you this assertion an algorithm. I know I cannot be tossing a truly random number, I would guess I would suggest right.
1:02:14 - Steve Gibson
If it were staring at the wall of lava lamps, of lava lamps or a capacitor Hooked up or you know some other physical. Yeah and so so. So if you say that an algorithm is flipping a coin, then okay, but you know. Again, it really comes down to the our definition of algorithm. Is an algorithm, you know, one plus one equals two, or is the owl? Can you say that the algorithm is Ask a random number generator for a number? Well, if that's what you're gonna do, then I don't think that's an algorithm.
1:02:53 - Leo Laporte
We well, we know that quantum computing is not deterministic. That's its chief advantage, right. It's neither on or off, it could be any variety of states. We know also that Fuzzy logic we talk all the time about using fuzzy logic to, or fuzzing right to, solve Security issues. That's not deterministic, right, it's kind of randomized inputs.
1:03:20 - Steve Gibson
Yeah, although there.
1:03:21 - Leo Laporte
It doesn't have a term in a stick. I guess there could be pseudo random, but but okay.
1:03:25 - Steve Gibson
So, for example, the, the. The one of the best ways to get generous, for a little box to generate random numbers is to to To force Current backwards through a diode. Right, you reverse BIOS, a diode which does not. It wants to prevent any current from flowing. What it turns out is that there is some noise of individual electrons, just through heat and and I mean true quantum level stuff, crossing over that boundary junction in a diode. You amplify that and you, you, you clean it up and that is a source of true Entropy. And so that's what all this, all the little boxes that say, you know, contains a true random number generator. That's what they have. You you could also use a Geiger tube and stick it out, you know, hold it up in the air and when a what? When a neutron or whatever the heck it is, flies by or a Charged particle passes, it's like, oh look, I heard a tick of my Geiger tube.
1:04:33 - Leo Laporte
These are essentially Chaotic inputs, right to one exactly. Somebody says in the in the discord I think this is actually a good definition. Non-deterministic Algorithm would be different outputs for the same input, which, by the way, most of the time in programming is something to be avoided. Right, the problem with pseudo random number generators is eventually they repeat, because they aren't really random but a diode, backwards diode or a Geiger camera yeah you're, it's gonna be truly random. Yeah, I guess dice a die is random, except there's little influences from the shape.
1:05:13 - Steve Gibson
Yeah, yeah, if you actually I mean it if it's not perfectly manufactured, and also you know that mean dies have different number of divots on their different faces, right? So it's gonna has anyone ever actually taken the time to compensate for that? All right.
1:05:30 - Leo Laporte
No, no, and we know that you can load die by shaving them, just changing the weight of one side slits. Yeah, so that's so sufficient.
So, lila, go ahead. I love this subject because it is a fun subject and to me, that is the criterion I use to determine between AI and Coding. Algorithms are inherently deterministic in my opinion, but in AI, because it's creating its own algorithms, is non-deterministic in that sense. So if it's machine learning or a generative adversarial network, generative adversarial network or something like that, it's writing its own rules, not a human. It may still be, frankly, a deterministic algorithm, but we don't know what's going on inside that black box. So, from our point of view, it isn't. That, to me, is AI, but you know. So I'm curious, it's mostly semantic, you know.
1:06:24 - Steve Gibson
We know what AI is. Yeah, so Lila burl Davis, she's tweeted. She said hi, steve, I just came across an excellent introduction to sync thing on youtube and thought you might be interested in recommending it to your security now listeners. It's very well made and the author is clearly not only extremely knowledgeable but knows how to explain things to a technical audience. It's made me think that maybe sync thing is not too hard for me. Have a quick look. I'd be surprised if you don't watch the whole thing. Sync thing made easy. Uh, anyway, it's because I was in the middle of compiling the show I was unable to take the time to watch, but I quickly scanned the 30 minute videos 165 comments of universally strong praise, since sync thing can be initially somewhat off-putting and confusing.
1:07:23 - Leo Laporte
Oh, this is tech craft. Yeah, they do good. He does very good stuff. I would trust him.
1:07:28 - Steve Gibson
Yeah, so I made it. I made it our shortcut of the week for any listeners who've heard Leo and I, because both of us love and use sync thing. Grcsc Slash 842. Today's podcast number, grcsc Slash 842. It's about I think it's 28 and some seconds long, 28 minutes long and apparently you know, uh, uh, it's great yeah.
1:07:54 - Leo Laporte
It looks pretty good. I agree with you. I recommend it. With my cursory scan of the of the thumbnails, it looks pretty good yeah.
1:08:02 - Steve Gibson
So, uh, uh, furious, opus. He said you suggested neutering what http sites can do to prevent what happened in egypt. But I was wondering couldn't the middle box redirect send him to a malicious https site? If so, scripting on http sites isn't the problem. The http connection is what's vulnerable. Thanks, scott, and I think that's a very good point, since the middle blocks was returning a 307 temporary redirect and the url bar was going to be changing anyway as a result. It would be less worrisome if the redirect was to a secured Https site where the malware was delivered. So I think that's a very good point. I just wanted to share it with our listeners.
Um, as someone who's uh, his picture in in twitter is a cookie monster and of course, his handle is cookies, uh, he said hey, estee, what happens when the person responsible for securing the family's digital life, photo storage, general storage accounts, etc. Unfortunately and suddenly passes away? Since becoming a family man many years ago, I've been thinking about the best way to approach the conundrum. Will your loved ones know what to do if you get run, run over by a bus or hit by a train? The conundrum comes when there is that one person in the family who has set up all the accounts, the multifactor authentication, their recovery codes and so on. The other one loves them, so puts up with all the extra hoops that they're being made to jump through, but may not fully understand all or any of it. The issue is the line between ensuring there are no weaknesses in your setup Versus ensuring your loved one has enough information to figure out how everything works and is able to access the family photos, digital files and everything else. Anyways, love to hear your thoughts on the matter.
Ps. I have limited time to listen to podcasts and audiobooks so unfortunately I have. I had missed the last eight months as I got up to book 14 Of the silver ships. Once you mentioned it, exclamation point, and he said plus Leo and his screensavers was the reason I asked my parents for satellite tv when I was 14 in the early 2000s, signed matt from australia.
1:10:37 - Leo Laporte
Yeah, way to go matt.
1:10:39 - Steve Gibson
So I included matt's question, even though it's not a new problem, due to its importance, which I think Endures. The question, of course, is how would the people we care about fare if, for whatever reason, we were to become unable to guide them through the process of unlocking Whatever we had secured from the rest of the world? The related problem is that this is also something of a moving target. We perhaps we did at some point in the past Take a snapshot of our security precautions, passwords, etc. Is that snapshot still valid? Over time we tend to make changes, you know, like perhaps moving away from last pass, but that suggests that we should periodically revisit our preparations.
1:11:28 - Leo Laporte
So, anyway, just to, I have about that in my desk drawer case. Anything happens to me, steve, tell lisa this. I have a piece of paper that says in the case of my death or dismemberment, and inside is all the passwords. I even taped a ube key in there, my backup ube key in there, but also a bit warden and last pass, and most password managers have a way to specify An emergency contact or recovery contact. So I've done that with lisa and other family members for my bit warden.
In fact, when we got our new iPhones, I noticed you can do the same thing With your iPhone. You can, you know, specify an emergency contact. Emergency, not contacts wrong because it's after your death or or incapacitation, but an emergency Person who has access to your account. And so I've done that also and I in fact, I told lisa and our son Michael about it and they, we did that all and I think that. So I think there's an increasing awareness of this Good and you're right, you got to keep it up to date, although if you do it the way, bit warden and apple do it.
1:12:39 - Steve Gibson
Yes, you don't have to worry, right, if you, if you provide a means to get in to your master set of secrets, then the changing secrets are always current whenever anyone gets in. So yeah, yeah, good. Um, yeah, apple does it account recovery.
1:12:56 - Leo Laporte
Contact Account recovery count recovery interesting.
1:13:00 - Steve Gibson
Well, we'll be looking to look at how that works, exactly because this one maybe requires you to still be alive. Well, or or maybe it requires you not to deny their attempt. That's how bit work works.
1:13:14 - Leo Laporte
It's a dead man switch. So they said an email and you set the time span and you say yeah, if I don't respond in seven days, give her access, let them in. Yep, yep, yep.
1:13:24 - Steve Gibson
Good. So mark w Clemens said I received a series of three. Uh, I mean, I'm sorry, I I received a series of three interesting tweets from mark w Clemens. He said first hi again, maybe you or leo could cover some security solutions with shop pay. He says perenn's Shopify. He said I get stuck using it every once in a while as a customer to a store like bowl and branch. It will not take a privacy card and I'm unable to delete my credit card later. The concern is the capture of credit card information when, not if, shopify gets penetrated and customer data is stolen. Thank you, mark Clemens. And he says perenn's. Using my name is fine, I'm your age and hard to embarrass. So then I got an update tweet. Update. He said I received this from htdb, colon slash, slash, privacy dot com. And he said shop pay Just attempted to charge zero dollars and zero cents to your shop pay card, but the charge was declined because we've detected multiple cards used at shop pay. This behavior is prohibited on our system to prevent exploitation of new customer or referral promotions. If you have a special use case which requires this, please reach out directly to our team at support at privacy dot com.
And then the third tweet from him. He said I sent you a dm on twitter about Http, colon slash slash privacy dot com and now I am getting calls from unknown individuals asking if I need credit card help. Is twitter monetizing the content of private dms? I think I will join you in leaving twitter. This was just too coincidental. Okay, now, this of course is all anecdotal, but twitter is objectively hemorrhaging cash and we're learning more about elan every day, so would anyone put it past him to monetize our supposedly private dms? They're only private in as much as they're only readily available to the conversations participants. Twitter never purported to be signal, whatsapp or iMessage, and who knows what the fine print it in the terms of service say. And just to keep some perspective here, google does something similar, as we know, with our email, which is private only you know, to about the same degree, anyway. So who knows? Anyway, just a heads up about something that might be happening in case anyone else cares. I don't know one way or the other.
Cpu guru said bit warden was warning me to update my pbk df2 iterations and suggested that I export my passwords. Before I did it, just in case, tried to do so under edge and it was blocked by microsoft defender smart screen as a quote potentially unwanted app. Unquote, sure, he said had to log in under chrome to do the export process. Laysay, he said so. So I included this here because I am certain I'll be announcing the general availability of grc's Validrive mass storage fraud detection utility on next week's podcast. Except for a few typos and some cosmetics that I need to fix when someone has scaled their font sizes to Of other than a hundred percent, it is finished and has been running beautifully for some time, but it will be a brand new Windows utility when it's released and Windows has become insanely overprotective about anything that has not yet had the chance to establish a reputation for itself.
The perceived safety of code is no longer about what it does or what it might do. It's all about its reputation and, annoying as that is for me, being a developer of always brand new code with no pre-existing reputation, I 100% agree with and endorse this policy. Unfortunately, reputation is the best defense we have today and for what it's worth. Once Validrive has established itself much as the DNS benchmark in control and GRC's many other freeware utilities have, it won't cause anybody any trouble, but initially I could expect that it will, and I'll remind everybody about that again next week, because what our testers have been testing the versions of Validrive and in many cases they've had to fight with Windows in order to get a copy to run, even though they just freshly downloaded it from GRC and I just built it from the source code. It's minutes old but unfortunately that's part of the problem these days.
Matthew N Dudek, he said related to your discussion about securely erasing drives. Windows 10 has a function to reset the PC with a clean the drive option so that the PC can be repurposed and reused like it was new. Is the drive cleaner, a secure enough erasure to prevent data from being recovered? I have old PCs that were used in a medical office. I want to give another, I want to give to another organization and want to make sure nothing can be recovered.
Okay, so I poked around a bit to see whether I could determine what Windows is doing, but Microsoft isn't being very clear about that and I didn't like take the time to set up Windows and do a clean the drive option and see what is left. So, at the moment, of all the things that have been suggested, I really liked the idea that was suggested by one of our listeners of using Veracrypt to encrypt the entire drive with an insanely long and then discarded password. It's a terrific and relatively simple way to cause ultra high quality pseudo random data to be written to the entire drive. Since Veracrypt has a portable operating mode, it doesn't even need to be installed. It can be run from a thumb drive and, if you you know, just type a bunch of gibberish into the keyboard for your password and encrypt an existing drive that way and then throw that that password away. You just filled your drive with absolutely strong pseudo random data.
1:20:25 - Leo Laporte
Although this is the argument for turning on file encryption before you use any media. Yes and yes. Now, mac, it's on by default. File files on by default. I guess BitLocker is not available in Windows Home, or is it now?
1:20:40 - Steve Gibson
You're right, I think it's not available.
1:20:44 - Leo Laporte
On both iOS and Android. As far as I know, the phones are encrypted by default.
1:20:51 - Steve Gibson
Correct. There is on the fly hardware encryption on the drive, so it's just a matter of discarding that. Key in the entire drive is no longer recoverable.
1:21:01 - Leo Laporte
Whenever, especially on an SSD, as we've talked about but in general, whenever I set up a new drive, I make sure they're encrypted that way I don't even think about it, right, because it's just garbage. On that, on that plan, right, even the slack space right.
1:21:17 - Steve Gibson
Neil Baldridge said Hi, steve, over the years they've been various discussions about battery health, charging etc. And I recall you talking about it being best to keep a lithium ion battery charge to minimize the charging cycles. He's at our company has been moving from ThinkPad laptops to Microsoft Surface laptops and I've noticed that mine, a Surface 5 laptop, wants to keep quote smart charging unquote on. Unless I override it, smart charging caps the battery charge at about 80%. If I need to have a full battery because of running disconnected from power, I have to remember to disable smart charging early enough to get a full charge. Then after a day or so it will enable it again and limit the charge to about 80%. Do you know if something has changed with laptop battery health, or maybe my understanding is just out of date? Thanks for all your contributions and I too am grateful for the extension of security now.
1:22:21 - Leo Laporte
First thing I would say by the way is if you keep it plugged in it is, you're not stopping charging. It discharges a bit and recharges, Discharges a bit and recharges. There is no way to not keep a battery from charging by keeping it plugged in. It's going to discharge over time and you're going to charge it. So his first premise is false.
1:22:42 - Steve Gibson
Well, so his information is not out of date. What he's referring to is a subtlety that I think I may have failed to make clear enough in our earlier discussions of this. While it's true that, unlike their NICAD predecessors, lithium ion batteries do not like to be deeply discharged, they also really do not like to be overcharged. Overcharging a lithium ion battery is really really bad for them. So what's happened is that various laptop manufacturers have started getting smarter about their battery charging. When they notice that the machine tends to be plugged in all the time, they'll deliberately begin resting the battery at some lower charge level, which is much safer for its cells. Then, if the battery is about to be used, as Neil said, you'll want to top it off shortly before going on the road. So it actually is smarter if you just generally use your laptop in an at home docked and plugged in way. Setting it up so that the battery is not always fully charged but is something more like 80 to 85 percent charged is better for the battery health.
1:24:08 - Leo Laporte
No modern device you're buying will let you overcharge a lithium ion battery none, in fact. The last time that happened those were those hoverboards. They burst into flames and were immediately banned. Everything you buy today has circuitry to prevent overcharging. You don't have to worry about that. But I think it is often possible to fully drain a battery. There's nothing to stop you from doing that either.
1:24:33 - Steve Gibson
Correct, although actually lithium ion batteries also have a little circuit on the cell itself that deliberately disconnects it because it does not want to go all the way to zero.
1:24:44 - Leo Laporte
I think it's also good for basically, I always just tell people trust the manufacturer and use those default settings because they know best the hardware Right. Don't try to outwit them.
1:24:56 - Steve Gibson
Right, although disabling it in order to go to full charge prior to going on a road trip does make sense, I do that on my EV. Yeah.
Yeah, and this brings us to the smart recommendation of the week. Kevin Van Herron said hey, steve, I've been thinking about the issue of security, of securely storing things outside of my cloud I'm sorry, outside of my cloud based password manager. We talked about, you know, using your password manager to store the things that were relevant to the web. But, you know, unless there's, unless there's a reason to store other things there, it would make sense to maybe put them somewhere else. Then you're not having the problem of worrying about what else might have been, might be decrypted in the event of a cloud breach, like we're now seeing with last pass. So anyway, he said and decided. He said I wanted a product where encryption was the main goal, rather than a compression product where encryption was an add on, and I had talked last week about using the you know, an encrypted archive as a typical solution. He said for this reason, I decided to use a password manager, just not a cloud based one, and one I won't integrate with my browsers. He said I'm going to use key pass XC. It's open source, cross platform and uses standalone files. You can include other files, not just passwords, in the encrypted database file. It's been around forever and started by forking the code base of the even older key pass X. They even recently had a code audit. He said files in the database aren't compressed but search and SSH keys are tiny and disk space is reasonably cheap.
And I just wanted to say I think that Kevin's rationale is sane. I would. I was wondering about the encryption of an archiver that was added as a secondary feature to the encryption and key pass. Xc is a cross plate desk across desktop platform. You know Windows, mac OS and Linux. So anyway, I just wanted to share Kevin's solution. And Kevin is certainly correct at the size of stored content is no longer a huge issue and, for what it's worth, it could be compressed before it's placed into key pass if you wanted that to. And you know you have to do it beforehand because, as we know, any resulting encrypted container cannot be compressed because anything properly encrypted contains zero entropy, making it impossible to compress. And One final note Principal Archivist answered the question about mathematicians. He said old mathematicians don't age, leo, they just get irrational. Okay, so buckle up now. After you tell us about our third sponsor, we're going to talk about encrypting the client. Hello.
1:28:11 - Leo Laporte
Okay, whatever that means, get your propellers prepared while I tell you about collide. Collide solves a big problem in the world. You know we have good trust solutions. Octa is a great trust solution. Make sure that anybody who signs into your network and uses your network apps is authenticated is real. What it doesn't address, collide does, and that's the issue of yeah, it's the real person. Yeah, it's that last past DevOps guy, so we've authenticated him, but what it doesn't do is check to see if he is an out of date and insecure version of plex on his hard drive, which he did. This is where collide is so great. It's a device trust solution for companies that use octa to ensure that if a device a device, not the person, a device isn't trusted and secure, it can't log into your cloud apps. If you work in security or it and your company has octa, this is a message for you.
If you listen to this show, I think you've noticed that the majority of breaches, the majority of hacks, all have something in common. Sad to say, it's the employees. Now, don't blame the employees. They're, you know, they're the attack vector. That's what everybody's hammering on with social engineering and all sorts of stuff. Sometimes an employee's device gets hacked because of an unpatched program like plex. Sometimes, employees leave sensitive data inadvertently in an insecure place Maybe their SSH private keys are in their download folder, that kind of thing and it seems like every day, some hacker breaks in using credentials fished from an employee. The problem here, though, is not the employees. It's the solutions you're using to prevent those breaches, but it doesn't have to be that way.
Imagine, close your eyes. Imagine a world where only known, secure devices can access your apps, so the employee or the person is authenticated and their devices guaranteed secure. In that world, doesn't matter if the credentials have been fished. And you can manage every OS, by the way, not just Mac and Windows, but Linux two all from your single dashboard and your little it cave, but, best of all, you can get your employees to fix their own device securely without creating more work for the it team. That's actually my favorite part about colliding lists your employees, your end users, as allies in the fight against bad guys. Well, guess what? You don't have to imagine that world. That's how collide works. Just start using collide with your octa, k, o, l, I, d, e, dot com, slash security. Now Do this booking on demand demo, because once you see how it works. I think that's when the light bulb comes on. It's really cool. K O L I D E collide dot com, slash security now. We thank him so much for supporting Steve and the important work you do here, steve.
1:31:16 - Steve Gibson
Okay, what is?
1:31:17 - Leo Laporte
hello. First of all, I don't know what you're talking about.
1:31:20 - Steve Gibson
Hello is actually client. Hello is the name of the first packet that our browser sends to a server. The sin and the sin. Well, that that's TCP. Yeah, the client. Hello is TLS, okay, so it's it's so you established getting yeah, exactly, yeah, exactly.
So today's topic was inspired by a tweet from Nick Sullivan. We referred to Nick many times in the past. His title is head of research at cloud flare, where he leads research in the fields of yes, of security and privacy, cryptography, internet measurement and emerging network paradigms. Prior to working at cloud flare, he developed encryption technology for Apple's Internet Services division. He also co wrote semantics Internet security threat report, which we shared for years, and has degrees in both computer science and pure math, so maybe a fielding medal is in his future. So here's what Nick tweeted and that's the reason we're going to dig into this today Twiq, twiq.
Nick tweeted last week encrypted client Hello. Ech is a new proposed standard that improves encryption and metadata protection for connections online that use TLS for security. After years of testing and refinement, it's finally happening, he said. Chrome has been testing ECH for months and is now enabling it by default in Chrome 117. Firefox is not far behind. Cloudflare just launched support for ECH again. Encrypted client Hello for all customers. These changes, he said, amount to the removal of the host name from clear text for a huge chunk of Internet communication. Considering how long the host name has been in clear text and how many products were built around that assumption. It's going to be an interesting rollout.
Following Nick's tweet. Someone immediately replied to his tweet saying what kind of fallout do you expect to see? I'm guessing a lot of enterprise and consumer parental and security controls will need to find new mechanisms. What else Nick replied? National firewall and content filtering will be affected. Someone else cautioned be very careful about implementing this in enterprise and education settings, as it removes a key indicator of compromise used by cybersecurity defenses. I know many CSOs are very concerned about the implications of ECH encrypted client, hello. And, of course, what all of this tells us is that spying on not the content of, but the fact of encrypted HTTPS TLS connections has remained a big deal and that this new initiative is in the process of taking that away. As Nick observes quote considering how long the host name has been in clear text and how many products were built around that assumption, it's going to be an interesting rollout. Okay, so let's back up a bit before we move forward.
Originally, the web primarily used HTTP. A client, a web browser, would look up the IP address of the domain the user wanted to connect to and make a query, so the browser would initiate then a TCP connection to the remote IP that it had obtained by querying DNS. Then the client, the browser, would send an HTTP query using an HTTP verb, typically get, followed by the URL of the resource to be retrieved from the remote server. The query would often contain some additional query headers, like if modified since, which would allow the server to check the date of the resource the client was requesting and reply with not modified, rather than resending something that the client already had. This improved the web's efficiency. So that's an example of a so called a query header that went along with the query.
But the most important query header, which has been mandatory since near the beginning of the web, was the host header. This told the server the name of the host from which the client was requesting the resource that was named after the get verb. In the very early days of the internet this wasn't strictly necessary, since the host's name was used to look up the IP of the server in the first place. So the assumption was that the server answering TCP connections and responding to queries at that IP would be the host the user expected. But then things became more complicated. We wanted multiple websites to be able to share the same IP address. That would mean that a domain name lookup for the IP of, for example, wwwacmecom might return the same IP as a lookup for wwwzebrascom. This meant that two different websites were cohabitating at the same IP, and that's what made the host query header then mandatory. If web browsers always included the name of the host's domain that they were querying, then the receiving end could examine the query to hand it off to whichever website matched the named host. And all that worked great.
But then along came HTTPS with TLS and things became more complicated. Due to a chicken and egg problem With HTTPS, an initial TCP connection is established, as before. But now the client indicates that it wishes to establish an authenticated and encrypted connection by sending a TLS client hello handshake packet. The server likely expects this, especially if it has accepted the initial TCP connection at its port 443, which has been standardized for receiving incoming HTTPS connections. But either way, upon receiving the client's client hello TLS initiating handshake packet, the server needs to reply with its matching server hello TLS handshake packet.
The problem is in a modern multi-homed environment where many different possible websites and servers exist which one should reply. We're wanting to bring up an authenticated connection, so the client needs to receive the server's certificate immediately for verification of the connected server's authenticity. But again, the certificate for which server, which website, which domain? Remember that the host header, which had been handling this for us in a pre TLS HTTP only world, is part of the client's HTTP query, which hasn't happened yet, since we still don't know who we're talking to and we have no encryption. Like I said, a classic chicken and egg problem.
This dilemma was solved by moving the declaration of which server we wanted, which website or domain we wanted to talk to earlier in the handshaking connection dance. It took the form of an early extension to the TLS protocol back when it was still called SSL. The extension is known as SNI, which stands for server name indication. So for a long time now, the initial client hello, which opened the TLS handshake, has included a declaration of which website, which domain the TLS handshake should be made with, which is to say, which server or domain should reply with a TLS certificate that's valid for the domain indicated by the client's SNI, enhanced client hello packet. And so, once again, all that worked. Great. But, houston, we still have a problem, even though we're now using TLS to securely authenticate and encrypt our communications once the channel has been established, the identity of the server that the user is connecting to is still out in the open as plain text for any and all to see. The SNI extension data is sent in the clear so that the proper server may be selected for a response and anyone any ISP, any carrier, any government, any sensor or malicious intermediary is able to monitor what amounts to HTTPS and TLS connection metadata.
Okay, so now what? The first attempt to resolve this conundrum was known, not surprisingly, as E-SNI, which of course stands for encrypted server name indication. Okay, so if the client is going to encrypt the server name indication extension data, the question is encrypt it with what? What encryption key is it going to use? How can the web browser encrypt the SNI data for a server that it wants to talk to before it's ever talked to it? Our mission today is to go in. We're going to go into this, but beware that, as I said at the beginning, quite unfortunately we are rapidly entering the land of the Cluj, and it's not going to be getting any better any time soon. In fact, it's going to be getting even more Clujie. The more and more fully the brightest minds in the world attempt to solve this problem.
The short version is this problem did not have any good, clean solution, and the longer version is yeah, but we still needed to solve it anyway. So how did E-SNI obtain an encryption key to use for encrypting the SNI data in the first client hello handshake packet? Believe it or not, ESNI gets that key from DNS. When an ESNI aware browser looks up a domain's IP, it also asks for the server's ESNI public key for the same domain in an ESNI DNS text record. So now the web client is able to use the targeted server's IP address to establish the connection and its DNS published public key to encrypt the ESNI data for inclusion in its initial client hello packet. Okay, well, there are several problems here. The first is that DNS is an unencrypted and unauthenticated protocol, which means that anyone eavesdropping on a client's DNS queries will see them looking up domains and obtaining IP addresses. And now ESNI public keys for specific domains. Okay, but wait, we do have DNS over TLS, aka DOT, and DNS over HTTPS, known as DOH. So, believe it or not, the use of some form of DNS connection authentication and encryption is now required as part of this messy solution.
I did warn everyone that we had a clue coming and it gets worse. The unanswered question is in a multi-homed environment where the incoming server specifying SNI is encrypted, how does the receiving server know under which server's DNS published public key the SNI was encrypted? The answer is that a single public key is now shared among all domains that share a common IP address. So a front end ESNI decrypter first receives any incoming TLS client hello message containing an ESNI extension. That server knows the private key that's associated with any of the domains sharing that single IP. So it decrypts the incoming ESNI data, determines the SNI target for the connection and returns that server's certificate. Wow, okay.
The problem here, aside from this being a growing mess which it is is that the SNI data is the only part of a connections metadata exchange that's encrypted. In other words, you know it's. The SNI didn't used to be encrypted. It was in plain text. So everyone looking at those client hello packets go by knew who the user was asking to connect to. So that was encrypted, creating ESNI and then also necessitating the mess of having a DNS publish the public key which was being used to encrypt the SNI data which would then be decrypted by its recipient across however many domains were sharing that IP. On the other hand, only the SNI data of the entire client hello is encrypted. So it turns out this leaves plenty of useful to snoopers connection metadata unencrypted. It's not worth getting into the details, because it turns out that all of this mess will have been transient, but to give everyone a feel for it, here is a snippet of what cloud flare wrote about ESNI. This, this proposal. Nearly three years ago, cloud flare wrote.
While ESNI took a significant step forward, it falls short of our glow, of our goal of achieving full handshake encryption. Apart from being incomplete, it only protects SNI. It is vulnerable to a handful of sophisticated attacks which, while hard to pull off, point to theoretical weaknesses in the protocol's design that need to be addressed. Esni was deployed by cloud flare and enabled by Firefox on an opt-in basis in 2018. An experience that laid bare some of the challenges with relying on DNS for key distribution. Cloud flare rotates its ESNI key every hour in order to minimize the collateral damage in case a key ever gets compromised, dns artifacts are sometimes cached for much longer, the result of which is that there is a decent chance of a client having a stale public key While cloud. While cloud flares, esni service tolerates this to a degree. Every key must eventually expire.
The question that the ESNI protocol left open is how the client should proceed if decryption fails and it can't access the current public key via DNS or otherwise. Okay, in other words, this is just an incredible mess. Getting the privacy that we want is really difficult. So the architects of all this set about coming up with a means for encrypting the entire client hello packet, leaving nothing of it in plain text for any snooper to obtain, and their credit. They also solved the problem that snippet there at the end mentioned with stale DNS data messing everything up. So how do we get to the to the title of today's podcast, which is encrypting client hello, and it's arguably even messier. The only thing I can imagine that these people really wanted to solve. The only thing I can imagine is that these people really wanted to solve this problem from where we stand today, even though there is no really good solution. But stepping back from the details, which is what we're about to step into further, I can appreciate that eventually, once all of this has been established like sometime in the future and is in place and is just the way things are done, a major step forward will have been taken toward improving the privacy and security of the internet. It's just that things have been, as I said at the top of the show, so much simpler and more straightforward until we really required this level of privacy enforcement.
Okay, in any event, esni, with all the time and effort that went into it, will eventually be fully replaced by its successor, ech, encrypted Client. Hello, this would close the gap left open. And it will close the gap left open by ESNI. It will protect all privacy, sensitive handshake parameters. Okay, so how does it operate? Similar to ESNI, ech initially uses a public key distributed by DNS, because there's just no other practical way to distribute the key, and it must be obtained using DOH DNS over HTTPS for the sake of preventing eavesdropping on that information and also security. So we still have the DNS is in the loop problem. This key is used during the client's initial server outreach. That is, the public key obtained over DNS used during the client's initial server outreach. But DCH, this successor protocol, has added some clever improvements and fallbacks when the DNS key distribution fails, which make the protocol, the resulting protocol, more robust in the phase of DNS cash inconsistencies, where an ESNI server aborts the connection, if the decryption of the SNI data should fail, an ECH server attempts to complete the handshake by dynamically supplying the client with a public key it can use to retry the connection.
Like I said, nothing is simple anymore. Okay, so if ECH encrypts the entire client hello packet, if its decryption fails, how can it possibly complete the handshake if it's unable to decrypt the client hello? So now we enter the mega-clude. The ECH protocol actually uses nested client hello messages. Unfortunately, moving it into the future, we're not going to have anything being simple here. We're going to have what they call client hello outer, which is sent unencrypted in the clear, and now client hello inner, which is encrypted and sent as an extension of the client hello outer. That's the way client hello inner is attached. Tls handshakes have a flexible extension mechanism and so you're able to just, I mean, and that's what SNI is, it's an extension data field added to the hello. Well, so now this encrypted inner client hello will be an extension added to the unencrypted outer client hello. If the decryption of the inner client hello succeeds, the server will proceed by using the inner client hello data. Otherwise, it will use the unencrypted outer client hello. Okay, but hold on, the outer client hello was never encrypted, so we can't really use it for anything, right? Unfortunately, that's true.
The outer client hello, while also a valid client hello message, is not used for the intended connection. Instead, the handshake is completed by what's being called the ECH service provider, which is that I talked about it before in the ESNI context, that is, it's something that answers all of the incoming connections. It's the common server that initially fields, you know, all attempts to connect at that IP Using the unencrypted outer client hello. This ECH service provider signals to the client that its intended destination could not be reached due to a decryption failure, remember, because if the encryption had succeeded, then the connection would have been made. In other words, the initial handshakes inner client hello could not be successfully decrypted. And while sending that news back to the client, it also sends back the correct ECH public key, that is, it overrides the DNS which the client first attempted. So if that, if that fails, then this ECH service provider sends back the correct ECH public key which the client can then use to retry the entire handshake. In so doing, it's able to correct the client's copy of the connection's wrong ECH public key which it would have received from DNS. Or you know if Cloudflare is still rotating these public keys every hour, then, and the client has an ongoing relationship with some server that Cloudflare is hosting. Well, that key is going to get stale so at some point a connection will fail. In the failure, the updated public key is sent back to the client and then uses that in order to encrypt the the inner client hello packet and is able to resume connections until, once again, that key expires. So there is a great deal of understandable concern over what breakage is going to occur with these changes.
Ech attempts, as I said, to hide the inner client hello by defining a new TLS handshake extension to contain it. The hope is that random filtering middle boxes along the way, placed who knows where on the internet, will just overlook any unknown new TLS extension types. But no one knows for sure yet. The people who initially began experimenting when TLS 1.3 was created were quite surprised that so many connections were failing. It turned out that this was due to traffic filtering and analyzing middle boxes which were crashing when they encountered the original, unexpected TLS version 1.3 packets. It was only after the 1.3 designers deliberately redesigned their shiny new protocol to much more closely resemble the existing 1.2 that they were then able to get their packets through, basically creating a lookalike version 1.3 protocol. That was finally able to succeed on the internet. So again, who knows what's going to happen once TLS client hellos incorporate a nested and encrypted inner client hello.
Hopefully all will go well, but in any event, as I started out noting, this is all actually happening. Now the announcements are probably more interesting. Again, chrome has been testing ECH for months and is now enabling it by default in Chrome 117, with Firefox to follow closely behind. And, as of last Friday, cloudflare launched their server-side support for ECH for all of their customers. So it's happening. I don't mean to, you know, come off sounding too pessimistic about all this. I know I'm glad that this work has been done and that the world is moving forward. Unfortunately, it does mean that the way that all of this stuff once worked, which was so clear and clean and simple and elegant, is going away.
It also wasn't fully secure or private, and it turns out that creating true privacy for a massive global public network is not an easy thing to do.
2:00:45 - Leo Laporte
Well, as you said at the beginning, none of this was designed to be secure and private, and so it's all tacked on after the fact.
2:00:53 - Steve Gibson
Yep, yep. And now this is not a tack, this is a box of nails.
2:00:59 - Leo Laporte
Let's hammer this in. Steve Gibson always makes See that wasn't so hard, aren't you glad you listened? Your brain is now about 1 eighth of an inch bigger, a full of all that great ECH information. Thank you, mr Steve Gibson. You can find Steve at his website, grccom. Now there's several reasons you might want to go there, of course. Number one Spinrite, the world's finest mass storage, maintenance and recovery utility. 6.0 is the current version, but 6.1, it's got to be like just like any minute now. Yeah, it's so close.
2:01:33 - Steve Gibson
I'm going to get back to it really soon, so close.
2:01:38 - Leo Laporte
You will get it automatically, by the way, if you buy a Spinrite today, so that's worth going there for GRCcom. There's lots of other stuff, including his forums. There's a feedback forum If you have feedback for the show at GRCcom, slash feedback. There's also copies of the show. Steve has the usual 64-kilobit audio, but he also has two unique forms. One is a 16-kilobit audio for the bandwidth impaired. It's a little scratchy but it works. It saves you some bits. There's also the transcripts. That's probably the smallest version. Elaine Ferris writes those from the 16-kilobit version and you can find that all at GRCcom If you want to read along while you listen or use it for search, et cetera, et cetera, et cetera. We have 64-kilobit audio at our website. We also have video In case you want to see Steve's smiling visage at twittv, slash SN.
Frankly, if you're in a hurry, the best way to participate in the show is to watch us do it live every Tuesday about 1.30 Pacific, 4.30 Eastern, 20.30 UTC. The live audio and video streams are livetwittv, and one of the advantages of watching live is you can chat at us live if you wish. Irctwittv is open to all. You can use your browser for that and, of course, if you're a Club Twit member and I do hope you are you can use the Club Twit Discord. That is one of the main benefits of Club Twit. Actually, I guess originally, when we created the club, the benefit of that $7 subscription was you're giving us money, we don't have to play advertisements for you. So Club Twit members don't get advertising they don't even get this mention but they also get access to the Discord for great conversations. If you're a sci-fi fan, John Scalzi joins Ant Pruitt in conversation this Thursday and John's latest book is the subject of our Stacey's Book Club.
That's coming up next month. We've got a lot of. We've got an escape room coming up. All the Twit hosts are going to get together in the studio. Jason, Ant, Micah and I will all be kind of trying to solve this escape box escape room. You can watch the Myrth will be Myrth and Merriman will be fast and furious with that. I'm sure we do a lot of club events.
We also do special shows in the club, like Hands On Macintosh with Micah Sargent, Hands On Windows with Paul Therati, untitled Linux show with Jonathan Bennett, the Gizfiz with Dick D Bartolo, Scott Wilkinson's Home Theater Geeks I Can Go On. There's a lot of benefits because we know seven bucks it's a lot to ask. We want to make sure you get your money's worth. But one thing that isn't on the spec sheet but really is the truth is you'll get that warm and fuzzy feeling knowing you're keeping Twit alive, You're supporting the continued production of our shows and increasingly, it's the club that's doing that.
So please, if you're not a member, twittv slash club, twit and I thank you from the bottom of my heart let's see the website twittv slash sn. That's where you'll get the podcast. There's a YouTube channel dedicated to security. Now you know, honestly, what we really would like you to do is subscribe in your favorite podcast player. That way you get it automatically. You can listen anytime you want. Just search for security now or, better yet, search for twit Press, subscribe, subscribe, subscribe, subscribe. It doesn't cost anything to subscribe. So subscribe to all of them and that way you'll have a never ending supply of fascinating, informative technology information on your device. Steve, have a great week. Thank you so much Once again.
2:05:12 - Steve Gibson
I will see you next week for the announcement of the release of Validrive. Back to Spinner I 61.
2:05:18 - Leo Laporte
Nice episode 943 can't wait See you next time. Bye.
2:05:26 - Lou Maresca
Come join us on this week in enterprise tech expert coast, and I talk about the enterprise world and we're joined by industry professionals and trailblazers like CEOs, CIOs, CTOs, CISOs every acronym role plus IT pros and marketeers. We talk about technology, software plus services, security you name it. Everything under the sun. You know what. I learned something each and every week and I bet you you will too. So definitely join us and, of course, check out the twittv website and click on this week enterprise tech subscribe today.