Security Now Episode 885 Transcript
Please be advised this transcript is AI-generated and may not be word for word. Time codes refer to the approximate times in the ad-supported version of the show.
Leo Laporte (00:00:00):
It's time for security. Now, Steve Gibson is here. Whoa, we got some good stuff to talk about. A very worrisome flaw in the wan interface of the routers. Many of us own. That's probably not where you want that problem. Another record D dos attack and how Google mitigated it. And then a blow by blow step by step list of how the newest and meanest kid on the block works. The bumblebee malware loader. It's all coming up next on security. Now podcasts you love from people you trust. This is TWiT. This is security. Now with Steve Gibson episode 885 recorded Tuesday, August 23rd, 2022. The Bumble bee loader. Security now is brought to you by Thinkst Canary. Detect attackers on your network while avoiding irritating, false alarms. Get the alerts that matter for 10% off and a 60 day money back guarantee. Go to canary.tools/twit and enter the code TWiT in the, how did you hear about us box.
Leo Laporte / Steve Gibson (00:01:13):
And by Barracuda, Barracuda has identified 13 types of email threats and how cyber criminals use them every day. Fishing conversation hacking ransomware, plus 10 more tricks. Cyber criminals use to steal money from your company or personal information from your employees and customers. Get your free ebook at barracuda.com/securitynow. And by Melissa, make sure your customer contact data is up to date. Try Melissa's APIs in the developer portal. It's easy to log on, sign up and start playing in the API sandbox. 24 7. Get started today with 1000 records cleaned for free at melissa.com/twit. It's time for security. Now the show we protect you online with this guy right here, Mr. Steve Gibson. Hello Steve. Yo Leo. Great to be with you. Good to see you as we start into our 18th year. Oh mg. Wow. So who would ever thought that? Not me kind of have the hang of it now.
Leo Laporte / Steve Gibson (00:02:25):
<Laugh> so we've got episode 8 85 for August 23rd. This one, I think a lot of our listeners are gonna find this one. Interesting. I hope because a security firm did a complete step by step. This is what we saw happening with a brand new piece of malware, which is called bumblebee due to the name of the first DLL, which contains it, which it arranges to get loaded. And, and as we'll see this is not a bumblebee that you want your enterprise to get stung with. Basically this thing is taking over the previous means for getting malware onto people's like some poor unwitting person who clicked a phishing email that in an enterprise, this thing gets in and it never lets go. So it, and it's one thing just to kind of wave our arms around and say, oh, you know, malware.
Leo Laporte / Steve Gibson (00:03:34):
But when you, the reason I wanted to take our listeners through this is that you, you really, it sort of gives you chills when you think about what this thing does. And it is also just a textbook perfect example of the new approach, which is being called living off the land, where rather than bringing a bunch of stuff in, which has the danger of tripping security alarms, increasingly we're seeing advanced malware using and abusing existing code on machines that thus the term living off the land. Anyway, that's at the end, we're gonna start off with a bit of fun over the most tweeted by far wacky news item ever. Well I maybe, well now, okay. Not we've had some wacky ones, so probably not ever, but still definitely it, it swamped my Twitter feed. Now I'm trying to think what could it be?
Leo Laporte / Steve Gibson (00:04:38):
Cuz there've been so many wacky stories this week. You, you will know. I heard you talking about it. I think maybe on Sunday anyway we're then gonna get serious with a very worrisome flaw, which likely exists in the wha facing interface of the routers that many of us probably own. We've got a new record having been broken for DDoS tax, which Google managed to fend off. And that's B broken by a large margin. We have both Chrome and apple dealing with if not emergency, then at least high priority software updates to squash some zero days that were in active exploit. We've got another major software repository tightening up its security against software supply chain attacks. And then after sharing just a few powerful bits of feedback from our listeners, we're gonna step through, as I said, this, the operation and actions of the newest and meanest kid on the block with the emergence of a powerful malware loader that is called bumblebee.
Leo Laporte / Steve Gibson (00:05:49):
And, and of course a great picture of the week too. Nice bumblebee bumblebee fly away home. Oh no. That's lady buby bug. That's a different one. Our show today brought to you by something that's gonna help keep you and your enterprise safe Canary. I'm sure you have secured, your perimeter locked everything down, right. But still the bad guys get in. They they're, they still get in. And then do you know if they've gotten in? How do you know if there's one thing we've learned from the last year and, and many shows on security now is that you've got to make it a priority to layer the security of your network. And one of those layers. Absolutely. Probably at the heart and center of it. The thinks Canary I've got mine right here. I'll show you. Oh, somebody glued it down. John why'd you glue it down.
Leo Laporte / Steve Gibson (00:06:43):
<Laugh> I'll GL it real briefly to show you this is the thanks. Canary. It's kind of unassuming. John probably thought, oh, it's a hard drive. You know, it looks like it looks external hard drive, but it's not. It's a honey pot. It is the bestest ever honeypot, easy to configure, easy to deploy. It can impersonate pretty much anything. And then when an attacker is wandering around your network, they don't look vulnerable. They look valuable, they look like something they're gonna wanna explore, but the minute they do you're Canary will say hello, not to them, but to you say, I got one, I got one. So it's like, you know, honeypot is, is, is, is an attractive nuisance, but it's not a nuisance for you. It's for the it's for the hackers. When attackers browse active directory file servers. When they explore file shares. When they look through different hard drives, we'll be looking for documents.
Leo Laporte / Steve Gibson (00:07:39):
They'll try default passwords against network devices and web services. They'll scan for open services across the network. And your think Canary can look like any of that. All the things hackers want to get to, you can deploy 'em throughout your entire network. You can make, 'em look identical to a router, a switch, a NAS server. That's what this one is a Sonology NA server. And when I say identical, it's got a Mac address, a Sonology Mac address. It's got the log in for DSM seven looks exactly like the real thing. Nobody's gonna be able to tell the difference, but the minute somebody does log into this, I'm gonna get an alert and I'm gonna get it in the way I want it. A meaningful alert. That's gonna help me understand somebody's in the network. It could be a windows server. It could be a Linux box.
Leo Laporte / Steve Gibson (00:08:25):
You can have one or two services judiciously lit up, or you can turn it on as a Christmas tree. It's up to you. And if you change your mind or you want reconfigure, it takes seconds to do that. You get a, a, an interface to it, just like a website. You could drop downs, you could pick whatever you want. Another thing you could do with your things, Canary that I love is you could put fake files on them and name them in ways that get hackers attentions. And you could actually take those files. They call 'em Canary tokens, spread 'em throughout your network. Just scatter 'em on hard drives everywhere. You know, know employee information or payroll, information dot XLS, something like that. Hacker can't stop themselves. They're gonna open that up the minute they do, you will know you can enroll your Canary active directory.
Leo Laporte / Steve Gibson (00:09:09):
As soon as attackers investigate, they give themselves away. You're instantly notified tiny trip wires into your organization. You can drop in hundreds of places. And if there's somebody there they're gonna get tripped, canaries are designed to be installed and configured in minutes. You don't have to think about 'em again. In fact, they they're no false alarms. So if you get an alert you know, something's going on, Canary can notify you as you like. So email text message with every Canary, you get a console. You can do that. You've got slack. They support that. Webhooks means they support a whole lot of stuff. Of course they support syslog. They even have an API. So you can write your own little Canary notify. If you want, you won't be inundated by false alarms. You'll just get those messages that really matter. You know, data breaches typically happen through your staff, social engineering when they do, it's very common.
Leo Laporte / Steve Gibson (00:10:04):
The companies aren't even aware they've been breached because the bad guys, they don't wanna announce themselves right away. Right? They wanna explore. They wanna learn. They wanna exfiltrate vital information. That kind of thing. On average, it takes 191 days for a company to know there's been a data breach. That's six months. That's crazy. Canary is, is the way to solve that problem. It's like the Canary in the coal mine. And it's been created by people who really understand this stuff. They've trained companies, militaries, and governments on how to break into networks. They know they use that knowledge to build the Canary. You'll find canaries deployed all over the world. They're one of the best tools against data breaches. Here's what you do. Go to canary.tools/twit canary.tools/twit. If you use the code twit and how did you hear about us box 10% off the price forever for life.
Leo Laporte / Steve Gibson (00:10:57):
You probably wanna know about pricing. I'll give you an example. Sometimes people have a, you know, a few canaries, many big institutions have dozens, maybe hundreds of canaries. But let's say you wanted five, which would be good for a small business, perhaps 7,500 bucks a year, five canaries, your own hosted console. As I mentioned, all the upgrades, all the maintenance, all the support for that whole year. And again, 10% off if you use the offer code TWiT, and how did you hear about his box? I know you're gonna love your thanks to Canary, but if you're not happy, you can always return your canaries within two months for a 100% money back guarantee full refund. So two months is a long time that really give you a chance to try it, but don't get alarmed. If you don't hear from your Canary, that's good.
Leo Laporte / Steve Gibson (00:11:37):
<Laugh> a silent, Canary is a good Canary it's it's when you get a notice and I tell you it's happened to us when you get that text message, somebody is in your system. That's when you'll be very glad you have Canary canary.tools/twit end of the code TWiT. And how did you hear about his box? Thank you, Canary. They've been longtime supporters of security. Now. They love what you're doing, Steve. They're really a, a great organization. We talk to 'em all the time and I, I couldn't recommend more highly canary.tools/twit. This is a video video of the week, this week, Steve. It is, I, I should say though, that if you're not convinced yet that something like a Canary is what you need you will be by the end of this podcast. <Laugh> oh, oh boy. <Laugh> because, because it is exactly the sort of thing that the guys behind bumblebee loader.
Leo Laporte / Steve Gibson (00:12:33):
Oh yeah, yeah. Would trip over. Right. And, and in fact, the timeline I was, I was thinking about this already, that there's enough manual side to this, that if you did receive notification of an, of early strange behavior, that there would be time. Oh, that's good. And that's good. So anyway it does play perfectly into today's topic. So yeah, we have a video of the week. I had not seen this before. I don't know YouTube. I was, oh, I, I was looking for something else and it, it came up and said, you might think this is interesting. I thought, huh, it's a little freaky. How correct. You are Google. So we're playing it now. And I, I played it for Lori and she's like, what? <Laugh> last year my trainer said, I saw UFO last night. I said, you did, what did it look like?
Leo Laporte / Steve Gibson (00:13:30):
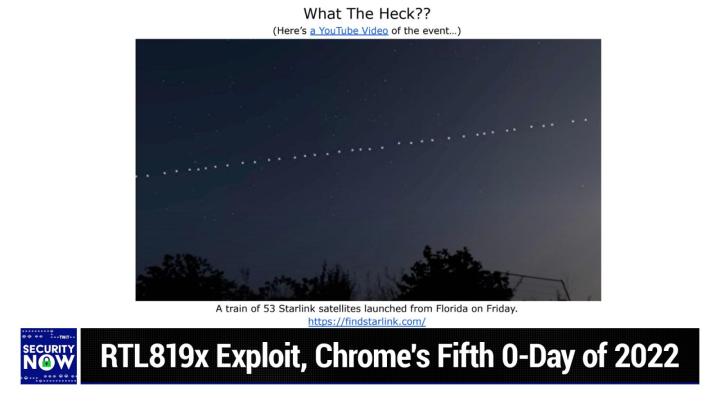
He described what you're seeing right now. And I said, oh, that ain't no UFO. What is it, Steve? So it is it it's and I describing it can't do it justice. I mean, it, it would be, I, I guess we're sort of used to stuff happening near earth. So maybe it wouldn't be that surprising, but it's extremely cool. What you're showing is a video of the light reflected the sunlight reflected off of a train of 53 Starlink satellites, which had been, and this was taken a couple days ago, which had been launched from Florida on Friday. And this has, this has been going on for a while, as Elon's company is getting the Starlink constellation of satellites up in the air. But I mean, the idea of, and, and this is just some random guy with a cell phone recording this the, I mean, and it is like, it's a series of dots, spaced somewhat evenly.
Leo Laporte / Steve Gibson (00:14:35):
I mean, it's kind of perfect that they're not perfectly, even because, you know, I guess these have been released from the, the transport vehicle. Yeah. They've got them up into orbit. They do this every time they fly in formation and then they deploy to their locations. But when they first come off of a, it's like a, a me, you know, when they first come off of the rocket, they're all in formation. Isn't that cool? It's just too cool. It's a train train. They call it anyway. Nothing. Yes. Nothing to do with security, but just something very cool. Yeah. And if you ever, you know, you can see it, it's it's happening all the time. They've, they've done many, many launches. So if you get a chance it's worth seeing. So since we're on the topic of nothing to do with security, I needed to respond to what was by far the most tweeted to me news item in a long time.
Leo Laporte / Steve Gibson (00:15:22):
And our listeners who are naturally on top of their game, felt about this pretty much as I do for more than two and a half decades, the highly respected Microsoft engineer, Raymond Chen has been blogging. Oh, I do know what you're talking about. <Laugh> I love this. I knew you would. Last, last Tuesday, he posted a blog entry. That was just so weird that everyone picked up on it. Raymond's posting was titled Janet Jackson had the power to crash laptop computers. Now the fact that this was assigned a CVE number that CVE 20 22, 38, 3 92 has apparently lent it more credibility, or at least more notoriety. I, you know, than I think it deserves. And the fact that the CVE refers to Raymond's blog as its sole reference seems to be somewhat self-referential Raymond refer recites, the CVE, which cite Raymond. And I'm actually wondering whether it might have been a slow blog week and Raymond was, you know, may have needed a bit of filler.
Leo Laporte / Steve Gibson (00:16:37):
So his blog post opens with two lines. A colleague of mine shared a story from windows XP, product support. Okay, well that wasn't recent. Presumably, anyway, he said a major computer manufacturer discovered that playing the music video for Janet Jackson's rhythm nation would crash certain models of laptops. Okay. <laugh> so from, from the CVE, we learned that this was certain models of laptops circa 2005. So 17 years ago, the CVEs formal description says, cuz you know, if it's a CVE, you need a formal description. It says a certain unnamed 5,400 RPM OEM hard drive as shipped with laptop PCs in approximately 2005 allows physically proximate attackers to cause a denial of service, you know, device. It says device malfunction and system crash via a resonant frequency attack with the audio signal from the rhythm nation music video. <Laugh> if this wasn't April, if, I mean it's not April 1st.
Leo Laporte / Steve Gibson (00:18:02):
Right? So really, so we can see now why the tech press thought that this was just too wonderful to pass up. On the other hand, we have a C V E that was apparently issued based upon what amounts to a friend told me, rumor, no mention of the maker model of the 5,400 RPM OEM hard disc that should be kept away from discos. So this begs the question of just how low the bar has been set for issuing CVEs. You know, this is not an attack, although, okay. There are a vocal group of people who feel that any playing of Janet Jackson's rhythm nation should qualify as a form of terrorism. And neither is it a bug that needs to be fixed nor malware that needs to be expunged. There's no action that can or should be taken today. It's from 17 years ago.
Leo Laporte / Steve Gibson (00:19:06):
So why give this, you know, heard it from an XP support guy, a CVE in 2022. I have no idea. Of course those who've been following this podcast will recall that video, which was also cited in some of the coverage of this rhythm nation hard drive DDoS attack where somebody and we show this on the podcast, right, was monitoring the dynamic throughput of an array of spitting hard disc drives while screaming at the array at the top of his lungs. And sure enough, the throughput visibly dropped during the screaming. And as we noted at the time, the throughput dropped because modern mechanical, hard drives have crammed their tracks so closely together. I mean, actually they're now overlapping each other. That's like, you know, this is what engineers do, right? They engineer DRAM. So tightly that neighboring rose inter interfere and cause bits to flip well, they're, they're, they've also crammed hard drive tracks so closely together that they are, have become quite sensitive to any exogenous vibration.
Leo Laporte / Steve Gibson (00:20:26):
And in fact, the way they're mounted in the server chassis can be critical. Now, Raymond of course also referred to the famous video, showing that 1940 collapse of the Tacoma narrows bridge in the same way that rhythm nation was able to rub some hard drives the wrong way back in 2005, the coincidentally timed gusts of wind through the Tacoma narrows rubbed the bridge the wrong way until it disintegrated. Anyway, I felt that this podcast needed to at least acknowledge this story that everyone tweeted to me over the last week and that most of the tech press had a lot of fun talking about you know, as did we hear <laugh> in a not so fun and much more relevant issue during one of the recent DEFCON presentations in Las Vegas, a team of four Argentinian researchers from the cybersecurity company, Faraday security, detailed their discovery of what was subsequently classified as a CVSs 9.80 click remote code execution vulnerability in the interface stack, which real tech provides in the SDK for their, for their hardware's use with the very popular open source eco operating system since they had previously responsibly disclosed their discovery.
Leo Laporte / Steve Gibson (00:22:06):
And since real tech had patched the flaw in March, their presentation during DEFCON provided full disclosure of all the technical details needed to replicate the attack. After all, it's been a few months, consequently, there is now exploit code released publicly for this critical security vulnerability affecting networking devices, which use real tech RTL, 81, 9 X system on a chip and those devices number, unfortunately in the tens of millions being, you know of the turnkey consumer, plug it in and forget it variety. There's little chance that most of these tens of millions of devices are ever gonna be updated. Many will have long since gone out of warranty since this real tech system on a chip RTL, 81, 9 X is incredibly popular. We're talking about devices that many of us probably already have since the chips are used by more than 66 0 vendors, including Aztech Bekin Buffalo, delink ed max, Trent net, and Zeke cell.
Leo Laporte / Steve Gibson (00:23:32):
And again, zero click on the wan interface. The vulnerability presents on the wan interface and because it's a stack based buffer overflow, it allows for no operator needed compromise of the host upon receiving a UDP packet from the public internet, the Def con presentation left nothing to the imagination. The S I P you know, sip protocol, the, the ALG, the application layer gateway function that rewrites SDP data has a stack based buffer overflow. This allows an attacker to remotely execute their code without authentication via a crafted sip packet that contains malicious SDP data, which ends up getting written onto the stack, and then executed. Now we've spoken about the abuse of application layer gateways in the past. Remember that ALGs are essentially enhancements to the baseline Nat routing functionality, which allows Nat to handle what would otherwise be NA's interference with the details of specific Nat unfriendly protocols.
Leo Laporte / Steve Gibson (00:24:57):
The simplest example is the original FTP protocol where the client instructs the server, which port it has opened to receive the reverse connection from the FTP server, the router's application layer gateway monitors, the outgoing data sees the port being specified by the FTP client by looking in the packet as it's leaving the router. And then either opens that port in its one side interface so that the remote FTP server can connect in or modifies the outbound port specification to a port. It wishes to open the point being that it allows a Nat router to become transparent to the otherwise Nat hostile FTP protocol. Now, in this case, the trouble exists in the application layer, gateway logic for handling sip. That's the session initiation protocol used in V O I P systems. It's not clear whether disabling sips, ALG, if that's even an option in the router would help Johanna's Ulrich.
Leo Laporte / Steve Gibson (00:26:16):
Who's. The Dean of research at Sans says that a remote attacker could exploit the vulnerability for the following actions. They could crash the device. Okay. That's easy execute arbitrary code, a little more tricky, establish back doors for persistence. That's what you want to do. Reroute or intercept network traffic, you know, turning it into a proxy, basically take over any vulnerable router. And he warned that if an exploit for CVE 20 22, 20 7,255 were turned into a worm, it could spread throughout the internet in minutes. Now, while Johanna's is technically correct about a worm, as I've been saying recently, a massive worm attack no longer makes any sense. They made sense back when email viruses just existed to see whether they could, but in today's world, it's about money. Anyone who's capable of writing a working worm would also be capable of using the router as a proxy to bounce malicious traffic or to quietly mine cryptocurrency, or to enslave the router into the service of one of today's massive botnets.
Leo Laporte / Steve Gibson (00:27:39):
As we'll see in the next story, or to pivot into the network behind the router to see whether there might be something juicy, worth attacking somewhere on the router's land for their part. The four security researchers said that devices using firmware built around real tech eco SD K before March of 2022 are vulnerable period. Full stop users are vulnerable, even if they do not expose any admin interface functionality, TA attackers may use a single UDP pack it to an arbitrary port to exploit the vulnerability. And this vulnerability will likely affect routers the most, but some OT devices built around real tech SDK may also be affected real Tech's own vulnerability report. I went looking for it and found it is two pages and provides no guidance. There's no list of manufacturers or makes and models of affected products. Nothing there's no action that any responsible end user can take.
Leo Laporte / Steve Gibson (00:28:57):
There's no obvious way to know whether any particular router or O T device might be affected. The only recourse would be to proactively verify that your router is running the latest firmware available for it from its vendor. And to hope that they care enough to update their firmware for the model of router you have, if your system can run one of the alternative router firmware systems, such as D D w R T, I think that's what I would do. That would be one way to move it to safety into a platform that is being continuously kept up to date. So many of these sorts of things have come out through the years problems that are unlikely to ever be fixed. That it's possible to imagine the, what must exist, that the sort of massive known vulnerability database that both nation states and sufficiently large criminal enterprises must now be maintaining.
Leo Laporte / Steve Gibson (00:30:08):
You wanna get into which organization, what equipment do they have on their border. Look up all of the known exploits over time that have been available against it, and start working down through the list until you get in 17 years ago. Back when we were launching this podcast, that scenario would've seemed like pure speculative fiction today, I'd lay money down that such databases must now exist all over the world. Yep. And it's difficult to see how this changes. Nothing that we are like, there are no plans in a, in motion right now, cuz anything would take a while to have any effect. Nothing is going on. That's gonna like change the way the world is working now. And the way the world is working now is deeply broken.
Leo Laporte / Steve Gibson (00:31:01):
So those who can afford to be truly aware and concerned about security could choose to use a non-consumer router on their borders. You know, such as something running PF sense as I do at my locations, but that still leaves the much larger majority of end user consumers, potentially vulnerable for decades to previous old vulnerabilities. And every month more of these surface and routers are not being updated with nearly the speed or reliability that they should be. As I said, we don't seem to be taking any action. Okay. 46 <laugh> is hard to say this 46 million requests per second, after standing up to the largest ever DDoS attack on behalf of one of its cloud armor, adaptive protection customers, Google said it had blocked a record breaking HT TPSs based D query attack that hit at its peak, a whopping 46 million requests per second, that puts it 76% higher than the 26 million RPS attack, which we talked about previously, which had been mitigated by CloudFlare in June, Google chose not to disclose the target of this attack, you know, its customer behind this protection, but said that it believes the attack was carried out with the help of the Maris botnet to put the scale of this attack in perspective, it's an HTTPS request rate equivalent to receiving all of the requests to the WikiEd domain, which is one of the top traffic domains in the world, which Wikipedia would receive during 1 24 hour period, take all of those requests and compress them into just 10 seconds.
Leo Laporte / Steve Gibson (00:33:32):
It's that much traffic. And this thing went on for quite a while. Google's report of the attack and we've and Leo, thank you. We got the, the, the, the chart showing the shape of the attack peeking at 46 million RPS Google's report of the attack contains lots of interesting details. Here's what they shared. They said starting around 9:45 AM Pacific time on June 1st, an attack of more than 10,000 requests per second began targeting our customers. HT T P S load balancer. Eight minutes later, the attack grew to 100,000 requests per second. They said cloud armor, adaptive protection detected the attack and generated an alert containing the attack signature by assessing the traffic across several dozen features and attributes. The alert included a recommended rule to block on the malicious signature. They said our customer's network security team deployed the cloud armor recommended rule into their security policy and it immediately started blocking the attack traffic.
Leo Laporte / Steve Gibson (00:34:58):
In the two minutes that followed the attack began to ramp up growing from 100,000 requests per second, to a peak of 46 million requests. Per second, since cloud armor was already blocking the attack traffic, the target workload continued to operate normally meaning their site wasn't adversely affected. It stayed on the air. Everything was fine. Over the next few minutes, the attack started to decrease in size, ultimately ending 69 minutes later at 10:54 AM. Presumably the attacker determined they were not having the desired impact while incurring significant expenses to execute the attack. Now I would argue that point. I suspect that the attack cost the attackers. Exactly nothing other than the exposure of the IP addresses of their fleet of infected consumer routers, hosting the Mari botnet, but maybe not even that they said, in addition to its unexpectedly high volume of traffic, the attack had other noteworthy characteristics.
Leo Laporte / Steve Gibson (00:36:19):
There were 5,256 source IPS from 132 countries contributing to the attack. The top four countries, Brazil, India, Russia, and Indonesia contributed approximately 31% of the total attack traffic. The attack leveraged encrypt encrypted requests, HTTPS, which could have taken, which could have, which I'm sorry, which would've taken added computing resources to generate again, Google appears to be deliberately missing the whole point. If there were fifty two hundred and fifty six observed source IPS, then that crypto burden will have been well distributed across the globe. And then we learn that HTTPS pipelining was also in use further limiting the crypto overhead. Google said, although terminating the encryption was necessary to inspect the traffic and effectively mitigate the attack. The use of HTTP pipelining required Google to comp to complete relatively few TLS handshakes, right? And thus also much less burden on the attackers. It required them. The attackers to similarly terminate relatively few TLS handshakes.
Leo Laporte / Steve Gibson (00:37:54):
The attackers were establishing a single TLS connection than attempting to flood that connection with pipeline HTTP requests. There's no reason to believe that any IP that's flooding HTTPS requests down the pipe will ever generate a valid request. So those IPS should have, and hopefully were simply dynamically blacklisted. They said approximately 22%, which was 1,169 of the source IPS corresponded to, to exit nodes. Although the request volume coming from those nodes represented just 3% of the attack traffic. Now let's stop there for a second. That's interesting. 22%. So just shy of one fifth of the total source IPS were coming from tour yet its traffic was just 3%, which is what we'd expect, right? I mean, tour incurs, a huge latency burden and, and bandwidth burden on its user in return for giving you some hope for privacy on the internet. Anyway, sort of an interesting data point.
Leo Laporte / Steve Gibson (00:39:17):
They said while we believe tour participation in the attack was incidental due to the nature of the vulnerable services. Even at 3% of the peak, which would've been greater than 1.3 million requests per second, our analysis shows that to exit nodes can send a significant amount of unwelcome traffic to web applications and services. And finally, the geographic distribution and types of unsecured services leveraged to generate the attack, matches the Maris family of attacks. And I'm sure they couldn't resist poking at a few of those IPS and confirming that. Yep. In fact, that was Mars. Anyway, they said known for its massive attacks that have broken DDoS records. The Maris method abuses unsecured proxies to obfuscate the true origin of the attacks. So yes, Mary, if it was MAs, then they were bouncing their traffic through proxies like routers that have been compromised. Remember, we've talked about how, if a router exposes its plug and play port or the plug and place service to the wan interface, it's possible for someone to just set up a proxy and say, you know, send any traffic incoming to that IP and use it to reflect traffic anyway.
Leo Laporte / Steve Gibson (00:40:48):
So we know that attackers were bouncing their botnets traffic through intermediate proxies in order to protect the IPS of their actual bot agents, which they did not want revealed. So I couldn't help. <Laugh> another just random point. I couldn't help, but note that in their redacted report, cuz Google post in, in their, in their posting of this, they had screenshots which were redacted to hide the identity of their customer. They used text blurring oh, to obscure the identity <laugh> whoops. Uhoh we all know, you know, remember we, we covered it here in some beautiful work that we covered a while back. We learned the, that blurring text is not secure. We learned it doesn't work. If someone is interested in learning what original tech lies behind the blurred instance, they can identify the details of the typography from all of the examples of non blurred text.
Leo Laporte / Steve Gibson (00:41:54):
Then iteratively, guess the text that's behind the blur employ the same blurring of their guess text and then compare the result of the two blurring one they control and one, they do not, mm lead. This is an exercise for the listener. Yes. Google's report then switches into marketing mode, bragging about their technology, which anyone would have to agree works. So we're now living in a world where those whose internet web services must remain online in the face of tax will need to bear the added cost of the privilege of doing so by putting themselves behind Google or CloudFlare or one of these big pipe, DDoS protector services. Because otherwise you just <laugh>, you, you, I mean, aiming that much traffic at anyone else. I mean, they, it just like, what's the point, right? This is like, you know, just stomping on, on a Nat using a planet.
Leo Laporte / Steve Gibson (00:43:06):
<Laugh> it just it'd be ridiculous. And Leo, I'm gonna take a sip of water. Let's tell our listeners let's do it. Why they're glad they're here. Yeah. We we use Amazon for DDoS. They, anybody who has a lot of bandwidth can, can do that DDoS production. Cloudflare does a great job. I think this is as much a war of press releases as anything else. Cuz I think CloudFlare just recently had a, almost as big <laugh> Dedos yeah. Inion in, in, in June, right? Yep. Yeah. So it's like, well our DDoS is bigger than yours. <Laugh> our show today. Hey, we always talk about this stuff. It's an important subject security, right? And if you are interested in security, if you're in the business you know the name Barracuda, this episode of security now brought to you by Barracuda in a recent email trends survey, 43% of respondents said they have already been victims of a spear fishing attack almost half, but only 23% say they have dedicated spearing protection.
Leo Laporte / Steve Gibson (00:44:12):
You know, if you're relying on your employees to recognize and ignore spear fishing attacks, good luck. <Laugh> how are you keeping your email secure Barracuda has identified 13 distinct types of email threats and they've documented how they're used every day by cyber criminals, fishing and conversation hacking and ransomware. Plus 10 more tricks, cyber criminals use to steal money from your company or personal information from your employees and customers. Are you protected? Are you protected against all 13 types? Yeah. Email cyber crime is becoming more sophisticated and attacks are more difficult to prevent. They'll use social engineering. And of course, one of the big tricks is to use urgency or fear to get their victims, to respond without thinking social engineering attacks, including spear fishing and business, email compromise cost businesses on average, $130,000 per incident. That's the average could be a lot more as I'll give you an example as demand for COVID 19 tests increased at the start of the year.
Leo Laporte / Steve Gibson (00:45:19):
Barracuda researchers saw a related increase in COVID 19 test related phishing attacks, 521% increase between October and January of last year as public interest rises. Of course, for example, in cryptocurrency, the opportunity for attacks becomes ripe. You know, when last year when the Bitcoin value was going up and up and up and up increased almost 400%, the impersonation attacks to take advantage of it increased 192% in the same period. And I can bet that as crypto's going down, you're gonna see a tax, you know, immediately shift to something that works with that. You know, they're move they're fast. Moving in 2020, the internet crime complaint center, IC three received 19,000 business email compromise and email account compromise complaints, 19,000 with adjusted losses of over 1.8 billion. That was two years ago. I bet it's a lot worse today. And of course, securing email at the gateway, as many of us do is great, but it's not enough anymore.
Leo Laporte / Steve Gibson (00:46:25):
It's still important to leverage gateway security of course, to prevent against a traditional attacks. You know, viruses coming in over the zero day, ransomware of course, spam and other threats. But your gateway is useless against spearing against targeted attacks. Protection has to happen at the inbox level and you're gonna need some sophisticated tools to detect it. AI and machine learning because these threats are, are moving target. You can't just say, well, filter against that. You gotta have something that's smart enough to look and say, yeah, that's that's spear fishing. Look, you listen to this show cuz you want this information. I've got a place you can get lots more. The Barracuda report is available free right now for you. 13 email threat types. You need to know about right now. You'll see how cyber criminals are getting more and more sophisticated every day and how you can build the best protection for your business, your data and your people with Barracuda.
Leo Laporte / Steve Gibson (00:47:19):
Find out about the 13 email threat types you need to know about and how Barracuda can provide complete email protection for your teams, your customers, and your reputation. You get that free ebook at barracuda.com/security. Now Barracuda B a R a C U D a barracuda.com/security. Now thank you Barracuda for supporting the show and you support us when you go to that address. That way they know you saw here barracuda.com/security. Now Barracuda your journey secured. And once again, I, we have a coincidental collision of sponsor and topic for the podcast because the entire entry point for this bumblebee loader is spear fishing. Of course, of course, as we'll see, I wrote, I wrote all this before I knew you didn't know be advertising. Yeah. Yeah. It is ultimately as we we'll see that hapless person in the enterprise who clicks on an email yeah.
Leo Laporte / Steve Gibson (00:48:25):
And, and, and takes some actions, which will clearly specify that begins this entire thing. And it just must be keeping it people oh. Up at night and owners. I mean it's terrifying. Yeah. Yeah. Okay. So last Tuesday, Google updated our Chrome browser for desktops to squash an actively exploited high severity. Zero day flaw in the wild is tracked as CVE 2022 28, 56. That's only four digits. Interesting. you know, as we know, CVEs are allocated now in blocks and so various people, you know, allocate them as they choose. So the fact that it's four digits and, or, and a low number, doesn't really tell us anything. Anyway, the issue is a case of what they termed insufficient validation of untrusted input, which you know, is like Microsoft saying, yeah, that was a security.
Leo Laporte / Steve Gibson (00:49:30):
Okay. Right. Security researchers Ashley, she and Christian resell both on Google's tag team. Remember that, you know, their threat analysis group are credited with reporting the flaw last month on the, on the 19th of July as usual. There's no upside for Google to sharing anything more with us beyond, please be sure that your version of Chrome now ends in.one zero two. They did add the quote. Google is aware that an exploit for a CVE 20 22, 28, 56 exists in the wild. In addition to stomping on that fifth of the year actively exploited flaw that update to blah, blah, blah.one zero, two addressed 10 other security flaws. Most of which relate to the, the most common use after free bugs, that would just keep encountering in this code at which appear in various Chrome components. They also fixed a heat buffer overflow in the downloads portion of Chrome.
Leo Laporte / Steve Gibson (00:50:43):
So this is number five this year previously we had a, a, the, the first of the year was a use after free in animation. We had two type confusion bugs in V8 and a heat buffer overflow in web RTC. So, and now with number five, being a rather vague insufficient validation of untrusted input okay. In area. So if you're using one of the non Chrome chromium siblings, you know, edge brave opera or Vivaldi, just be sure to keep yourself updated there too, because they would all be susceptible until they're updated with the latest update to chromium, you know, they're common core or, and not to be left behind last Wednesday, apple released high priority security updates for iOS iPad OS and Mac OS platforms that this was to remediate a pair to zero day vulnerabilities, which were being exploited by threat actors to comprise, to compromise Apple's devices.
Leo Laporte / Steve Gibson (00:51:49):
There was the CVE ending in 32,893, which was an out of bounds bug in web kit, which could lead to the execution of arbitrary code by processing, especially crafted web content and 32, 8 94, an out of bounds bug in the OS kernel that could be abused by a malicious application to execute AR arbitrary code with the highest privileges. So again, these are not theoretical. These were found being used to, you know, perpetrate malicious ends. So that was pushed quickly. And all of our devices, I got little notices everywhere. So apple clearly felt that this was worth, you know, getting out into the world. They said that they had addressed the issues with improved bounds checking. So that's good. Cuz those were out of bounds bugs. So <laugh>, you wanna do a little more bounds checking to keep them from going out of bounds. And they said also that they were aware that the vulnerabilities may have been actively exploited Uhhuh, and please update immediately before you do anything else.
Leo Laporte / Steve Gibson (00:53:05):
So as usual, they didn't disclose anything additional either regarding these attacks or the identities of the bad guys who, you know, may have been using them. Although as usual, it's almost certain that they were, you know, involved in targeted intrusions. Again, you're not gonna spray this around cuz you want to keep it quiet and get as much use out of it as you can. And since we're counting zero days so far this year, this latest update brings Apple's total of actively exploited zero days to six for the year as with Chrome. We had four below before, before these latest pair and we've covered them all in the podcast in the past. So anyway, two more added to the list and iOS iPad OS and Mac OS Monterey all need to be updated.
Leo Laporte / Steve Gibson (00:54:01):
As we know, Ruby gems is the official package manager for the Ruby programming language and in a welcome response to the increasing threat and prevalence of supply chain attacks, the Ruby Gem's repository has become the latest platform following N PM and PII pipeline to require multifactor authentication for its more popular package maintainers, specifically owners of gems, as they're referred to having more than 180 million total downloads are now as of last Monday, August 15th required to enable multifactor authentication. The Ruby gems management said quote users in this category who do not have MFA enabled on the UI and API or, and gem sign in level will not be able to edit their profile on the web perform privileged actions, for example, push and yank gems or add and remove gem owners or sign in on the command line until they configure MFA. In other words, you know, they'll log in, try to do anything and they're gonna get a Nope, sorry you're too popular.
Leo Laporte / Steve Gibson (00:55:34):
You've you've got more than 180 million downloads. Okay. You should be proud of that, but just, you know, come on, let's do multifactor authentication here and as gem downloads approach that magic mandatory 180 million count. As soon as downloads pass one 65 million cumulative, their maintainers will receive reminders to turn on multifactor authentication before the download count hits the magic 180 million at which point, if they, they no longer have a choice. So this is further welcome. Of course in the, you know, packaging ecosystem to improve the past's casual approach to software supply chain security, which, you know, no one took that seriously until we started discovering lots of malicious packages in our repositories. So as we know, adversaries are increasingly setting their sites on open source code repositories with attacks on NP and PII having snowballed by a combined 289% since 2018 researchers from check marks, Casper ski and sync have all uncovered a large number of malicious packages in PII that could be abused to conduct DDoS attacks and harvest browser passwords as well as discord and Rob lock's credential and payment information.
Leo Laporte / Steve Gibson (00:57:11):
So now Ruby gems joins the ranks of NPM and Pipi, which are all tightening their security and, you know, yay. The, I mean, it's, it's nice to see this happening. It's clearly something that is easily done. We, as I said before, we still don't have an answer to the O T problem to the, this problem that we've got very sophisticated devices packaged in $5, light switches and plugs with no one standing behind them where vulnerabilities are being found by researchers. And there's just no infrastructure in place to fix them. And it's not like this is like slowing down the rate at which this stuff's being created is accelerating. And there's nothing on the horizon that suggests a way to fix this. And even if there were, or once there is, it will still take decades for it to work its way through. So bad.
Leo Laporte / Steve Gibson (00:58:19):
Okay. We have some very neat closing the loop bits Thomas, Tom, Jack tweeted, he said, Hey Steve, when you register a domain, you do have the option to register a technical contact, as well as the owner. He said, when I have registered domains in the past for friends, I always make sure they are listed as the domain owner and myself only as the technical contact, he says, yes, it's still under my registrar account, but at least that shows proof of ownership and they could probably transfer it to a new account at the same or different registrar. Should I get hit by a bus <laugh> unexpectedly? So I I'm so glad that Thomas thought to remind me and us of that. And I wanna acknowledge that several other of our listeners sent notes to the same effect which I saw and thanked them. Of course that's the case and it had completely slipped.
Leo Laporte / Steve Gibson (00:59:26):
My mind domain registration records provide for completely separate owner administrative and technical contacts. I'm so used to always pointing all three of those at myself that I completely forgot the power of the flexibility that they could provide. Now this of course begs the question. What would a domain registrar do if the assigned owner of a domain, which is after all just a name and email address wished to take control of the domain in the event that the admin or technical contact was unresponsive, would that provide the degree of safety that we're looking for? I don't know, in an attempt to answer that question definitively, I found an, I can fact, you know, an FAQ question, 12 that they asked themselves read, I can't access my domain name or my domain name management account because the domain name was registered by someone else such as my web developer or administrative contact.
Leo Laporte / Steve Gibson (01:00:41):
What now? And their answer, I can's answer is quote, you may not be able to access the domain name. If you are not the administrative contact slash registrant of record of the domain name, you should contact the individual or entity who registered the domain name to obtain access credentials slash details or update the domain names, administrative contact slash registrant of record. Then they said in the second paragraph, you should contact your registrar right away. If your domain name manager slash administrative contact is unreachable has gone out of business, et cetera, to update your information. Once you're able to become the administrative contact slash registrant of record, this will ensure that you have full control of managing your domain name and allow you to find someone else to help you manage your domain name. If you so choose. It's a good idea to keep a record of your domain name management credentials at all times, even if you choose to outsource some administrative slash management duties to a third party.
Leo Laporte / Steve Gibson (01:01:59):
Okay. So the formal names of the, of the thing of the three things you can register is there's the owner there's administrative and there's technical contact. And you know, in I can's response, they keep referring to administrative contact. Well, okay. That there's, that's one of the three right. Administrative, but there's also owner. So I, I dug around some more and I couldn't find anything formal or official, but anyway, I just wanted to put on the record that a bunch of our listeners said, Hey, Gibson, did you forget about that? It's like, yeah, I did. So thank you. I don't think it solves anything. It's the same issue issue. I don't cause in effect I can saying, well, if you could prove to your registrar that you're you, which is what it would require to change the administrative owner. Well, then I guess we'll give you, I mean, it's, it's putting it back on the registrar.
Leo Laporte / Steve Gibson (01:02:58):
I don't think it solves anything, but so I, well, so what I was suggesting last week was that, that we needed like that the system needed to be upgraded to provide something like a, you know, a next in kin sort of effect so that there would be some means for dealing with a sudden lack of management. So, so, so our listeners said, Hey, you know, you do have three things in a domain name, registration record, but, and so it would be possible for you to ask the person who's managing your domain name to 0.1 or more of those at you, rather than all at him. So, you know, it's something, but it's again, you still don't have like, won't be access to the registration, to the registration record itself. Plus you need the cooperation of this person who is presumptively not cooperating, right? <Laugh>, that's the problem.
Leo Laporte / Steve Gibson (01:04:03):
If they're cooperating, this is why you should register it yourself. I think. But you know, that's what I always say. So I'll do it yourself. Don't trust him. Okay. So a listener day again he said, well, I, I should preface this. Well, I am truly flattered, honored and humbled that this podcast has had as much impact on people's lives through the years as it has. You know, I, I suppose that my true love for technology and Leo, you share that love with me. You always have and computing can be a bit infectious. So in that sense, I'm gratified that we've had the opportunity to infect so many of our listeners with this bug in fact. Okay. Yeah. Okay. <laugh> yeah. Alright. And it's a bug that, that I've been in, in its grip throughout my entire life. So this tweet from day, again, really hit home.
Leo Laporte / Steve Gibson (01:05:06):
So I asked its author if I could share it and I received his permission. So he wrote just to me by DM, he said, Steve, I wanted to privately drop you a brief personal note of thanks. I've been listening to security now religiously since 2011. And I truly believe your weekly show has had a significant impact on my career. And as such my life, when I started listening, I was a happy nerd that loved the idea of security nine years in I discovered and was credited for identifying two CVEs in a red hat product. Last year, I was credited for two more. Cves in a sushi product and this year yet another vulnerability in a second sushi product. And finally, just last weekend, I was fortunate enough to have the opportunity to present at Def con where I demonstrated chaining three of five vulnerabilities together to fully compromise a Kubernetes cluster from the outside.
Leo Laporte / Steve Gibson (01:06:17):
I will also be speaking at Coon this year where I will talk about securing clusters from risks introduced by third party applications. He said, I'd happily buy you a nice bottle of wine to express my most sincere gratitude. Oh, but I'll settle for a spin right license instead. Oh, that's nice. He said your show has changed my life, Steve. Thanks. Now just this morning. You Leo. Ah, I was wondering if you got that. Okay. Yes. <Laugh> forwarded a very heartwarming story from someone who said his career was catalyzed by this podcast. So as we start into year 18, I wanna share what he wrote as an example of what is possible. If anyone else out out there might be a need of a bit of a nudge. So this person wrote Leo. I must say I'm quite honored to have received a reply directly from you.
Leo Laporte / Steve Gibson (01:07:19):
I would like to share a brief story. You and Steve might like to hear in 2015, I recognized Steve's name on a list of podcasts. I knew it from back in the mid, late nineties, when I used shields up frequently, I left it after the.com bubble around 2002 ish. I followed a path in science, but ultimately I couldn't find a good job in that field. I was in poverty on Medicaid and in significant debt. It wasn't just me. I met my wife and our son was just born during this time. It was rough. I listened to security now and the ad for it, pro TV, I signed up, studied and passed the CCNA. In a matter of days, I had a good paying job as a network engineer. I have since moved on into cybersecurity, getting a C I S S P I now work at a job I love.
Leo Laporte / Steve Gibson (01:08:27):
And my family is able to live debt free with good healthcare and everything else that goes with this terrific career. Yay. I, I have you and Steve to thank for this well, and of course his own initiative too. He says your show made this field approachable and fun words cannot begin to express my gratitude and appreciation you guys change lives. Please keep up the great work, Michael. Thank you. Thank you. Yeah. Thank you, Michael. Yeah, for sharing your story, you know, the field of cybersecurity truly is a growth industry. There is a crying need for trained cybersecurity professionals. And boy, is it interesting and fun? Yeah. So you know, anybody else who's looking for something to do you can follow in the footsteps of these guys. Okay. I'm not crying. You're crying. Okay. I know I choke the first time I read. I know.
Leo Laporte / Steve Gibson (01:09:28):
So it's really, it was a beautiful, but you know, I have to say every time and I know you know this too, but every time we go out, we meet people. I hear these stories again and again. And so thank you for the job you do, Steve. And I always tell them, it's not us, it's you, but thank you for, you know, letting us be part of your life. And I'm glad we could help. Wouldn't be happening Leo, if it weren't for you. So no. Okay. Let's what do you wanna do now? <Laugh>, let's tell our listeners about our last sponsor. See whether it see whether it also another inspiration. Oh my goodness. Alright. <Laugh>, you know, I tell you what we don't do this for the money particularly. We do it because it is it's a privilege and an honor, and it's something we really enjoy.
Leo Laporte / Steve Gibson (01:10:18):
I know that I'm not saying anything you don't feel, but it is always nice. It is always nice to, to hear from people and know that we've made somewhat of a difference. So thank you very much for those kind words. Now I will mention another fine sponsor. Soon as I find the ad here we <laugh> here we are our show today brought to you by oh yeah. Yep, yep. Another one, Melissa, Melissa, poor data. Quality I'll tell you what poor data quality can bite any business in the behind. It can cost you money. In fact, organizations on average, 15 million a year due to poor data quality it can cost them customer appreciation and ultimately cost you customers. I mean, imagine you're on a customer service call and you address somebody by the wrong title, or you say, oh yeah you live in Florida, right?
Leo Laporte / Steve Gibson (01:11:19):
No, I live in Minnesota, dude. <Laugh> you're gonna lose the customer's trust. And of course the longer poor quality data stays in your system. The more losses you could accumulate to ensure your business is successful, your customer information has to be accurate. That's what Melissa does. They're the leading provider of global data quality and address management solutions. You need Melissa's identity solutions, their real time, identity verification service for all kinds of things, identity ID and document verification, age authentication, global watch list screening. You, this may be a compliance issue for you, AML KYC. Yes, you can easily tie tailor Melissa's service to your specific signup process, to your risk management requirements to ensure fast onboarding or e-commerce checkout while still protecting your organization against fraud with Melissa, you not only reduce risk and ensure compliance. You keep customers happy. 2.1 billion clean validated records. That's a lot ensure compliance in AML.
Leo Laporte / Steve Gibson (01:12:26):
Any money laundering, politically exposed persons P E P bank secrecy act BSA, and all those other regulations your business might have to adhere to score and target customers with detailed demographic and firmographic data. Appends complete customer records, add missing names or addresses or phone numbers and email addresses. And of course, Melissa treats your data as, as is important, as I'm sure you treat it. They undergo continuous security audits, their SOC two compliant, HIPAA compliant, GDPR compliant address verification services can verify addresses for 240 plus countries and territories at the point of entry in real time, addresses, email, phone numbers, names, also data D duping. Their Melissa's data matching system will eliminate clutter. Eliminate duplicates, increase the accuracy of their database and reduce postage and mailing costs. Melissa can be OnPrem. It could be in the cloud, it could be SAS. It could be a secure FTP upload and download.
Leo Laporte / Steve Gibson (01:13:31):
They have an API, so you can add it to your own customer service software or your e-commerce software. They can do batch address, cleaning process, an entire address list for accuracy and completeness. They can do identity verification, which not only helps you with compliance. It keeps customers happy and reduces your risk. They do geocoding. You can convert addresses into longitude longit and latitude. They can verify emails, remove 95% of bad email addresses from your database. You can even use 'em on iOS and Android. They have an app lookups it's called. Look for it. The lookups app will let you search addresses names and more write at your fingertips on your device. Make sure sure. Your customer contact data is up to date. Try Melissa's APIs in the developer portal. It's easy to log on, sign up and start playing in the API sandbox. 24 7 get started today with 1000 records cleaned for free at melissa.com/twit Melissa dot slash TWiT.
Leo Laporte / Steve Gibson (01:14:31):
That way, by the way, Steve was another thing Michael said, he says, I like listening to the ads while I'm at work. I like hearing that geeky stuff in the background. Okay. But we do have ad free versions of the show. If you want 'em you can buy the individual security now episodes for 2 99 a month or you could pay 7 99 and then get everything ad free and club TWiT go to TWiT TV slash club TWiT. There's also a discord server. We do have a book club. I'm gonna promote this this new book from David the Dennis Taylor, Dennis Taylor. That's it. Yeah, we, we were, we, we, we should mention that. Cuz we were talking about it before we for the club recording. Yeah. Yeah. Oh, you didn't mention it in the show. No. Oh, it was before. Yeah.
Leo Laporte / Steve Gibson (01:15:13):
Yeah. This is the guy who did the Bobba verse, Mr. Bobba verse trilogy. Yes. Of four books. And I was planning to be reading something else, but one of our listeners said you know how much you like the Bobba verse? He wrote something else called the singularity trap. And I was talking to Leo before the show. I, I have not been able to put it down. I've been reading it during the ad reads. No. Oh, you you're gonna finish it before the show's over. <Laugh> well, I'm gonna finish it tonight. Unfortunately. It is so fun. Fantastic. So it, it, it is go, you know, it's kind unlimited. So if you are a or a, a reader it won't cost you anything in, in the same way that the Bobba verse. Oh, good. Didn't oh, nice. Okay, good. And, and you learned that it's got the same guy reading it as who read the Bobba verse rape porters for audible.
Leo Laporte / Steve Gibson (01:16:08):
Yeah. And everyone was raving about, about the, the, the audible side yes. Of the Bobba verse. Yes. So anyway, it's called the singularity trap. It is the same style, the same wit it's like really fun. And I, and it is a book where you have no idea what is gonna happen next. It's a whole new concept that we've not, it's not a rehash of let let's go, you know, attack the aliens thing. It's a new idea. And really cool. So I, this one I can, I mean, I'm at sadly at 93% or something of the book, and I'm gonna be sad to have it end. Then I went looking for more stuff, but he's not written anything else. He's gonna do some more bender books on the Baba verse side. So I guess next. So anyway okay. The bumblebee loader it's recently become a big deal on the malware front Symantec in June wrote bumblebee a recently developed malware loader has quickly become a key component in a wide range of cyber crime attacks and appears to have replaced a number of older loaders, which suggests that it's the work of established actors.
Leo Laporte / Steve Gibson (01:17:24):
And that the transition to bumblebee was pre-planned by analysis of three other tools used in recent attacks involving bumblebee Symantec's threat hunter team has linked this tool to a number of ransomware operations, including KTI, quantum, and Mount locker, the tactics, techniques, and procedures used in these older attacks support the hypothesis that bumblebee may have been introduced as a replacement loader for a trick bot and bizarre loader. Since there is some overlap between recent activity involving bumblebee and older attacks linked to these loaders. And even earlier than that on the 7th of June, CBLE the security frame we were just talking about last week wrote in March, 2022, a new malware named bumblebee was discovered and reportedly distributed via spam campaigns. Researchers identified that bumblebee is a replacement for bizarre loader malware, which was delivered, which has delivered KTI ransomware in the past bumblebee acts as a downloader and delivers known attack frameworks and open source tools such as cobalt strike shell code silver met interpreter cetera. It also downloads other types of malware, such as ransomware Trojans and more, and last Wednesday, the global security firm, cyber reason based in Boston, Massachusetts with offices in London, Tel Aviv, Tokyo, France, Germany, South Africa, and Singapore published in their malicious life blog, a detailed technical description of the operation of this extremely dangerous new entry onto the malware scene. They titled their report Bumble B loader the high road to enterprise domain control.
Leo Laporte / Steve Gibson (01:19:32):
And this podcast will be remiss if we didn't take some time to bring our listening audience up to speed about this emergent threat. So cyber reasons report explains that they analyzed a case that involved a bumblebee loader infection, which allowed them to describe in detail, the attack chain from the initial bumblebee infection to the compromise of the entire enterprise network. Okay. So let's begin with a couple bullet points to set the stage. The majority of the infections with bumblebee, they said we have observed started by end users, executing link, you know, dot L K files still hasn't gone away, which use a system binary to load the malware distribution of the malware is done by fishing emails, with an attachment or a link to the malicious archive containing bumblebee. And I'll be expanding on all of this here in a minute. They said bumblebee operators conduct intensive reconnaissance activities and redirect the output of executed commands to files for exfiltration.
Leo Laporte / Steve Gibson (01:20:56):
The attackers compromised active directory and leveraged confidential data such as users, logins, and passwords for lateral movement. The time it took between initial access and active directory compromise was less than two days. And I'll be sharing a timeline breakdown in a minute. Cyber reason, GS O that's, their global security operations center has observed threat actors transitioning from bizarre loader trick bot and iced ID to bumblebee, which seems to be an active development. And generally the loader of choice for many threat actors, a tax involving bumblebee must be treated as critical based on GS O findings. The next step for the threat actors is ransomware deployment, and this loader is known for ransomware delivery. Okay, so let's take this step by step. A spearing email is received containing an archive or a link to a, a URL link to an external source to download the archive. As we know, the malware is encapsulated in an archive to prevent the archive's contents from being tagged with the mark of the web, you know, M OT w which would complicate its execution, the user extracts the archive and mounts, the resulting ISO, you know, dot ISO image, newer releases of windows will happily Mount ISO images thus exposing the ISO's file system files. The content of the mounted ISO image is a dot L N K file, which executes the bumblebee payload upon user interaction.
Leo Laporte / Steve Gibson (01:22:58):
So the operators behind an instance of bumblebee host malicious websites that implement a drive by download to infect the system an end user has to first manually decompress the archive containing the ISO file. On the other hand, if it's, you know, a zip windows will do that for you now, too, Mount the file and then execute the window shortcut L N K, this is all done as part of a phishing email where the user fully believes that they are doing the right thing that installing this or that is needed or updating something that's needed before they can proceed. So the user is without question unwittingly complicit in the success of this entire penetration and intrusion. All of the other mechanics is about avoiding everything. The users, enterprise security people have done to keep bad stuff out, despite what dumb stuff their users may do. So the LNK file has an embedded command to load and execute the bumblebee dynamic link library, the bumblebee DLL using the already and always present O D B C conf O D B C C O NF dot XE in what has become the increasingly popular living off the land approach of using what's already available in the system.
Leo Laporte / Steve Gibson (01:24:40):
And these days plenty is on in modern systems. So in this context, ODBC conf dot exc is called a LOL bin, a response, which is, has the extension dot RSP. A response file is also used where the, the, some Bumble B specific name do RSP has the reference contains the reference to the Bumble B DLL. So specifically the link files target property contains the string ODBC co N F dot exc space, hyphen F space. And then this, this bumblebee specific name ending and dot RSP, the response file and the dot RSP file contains a reference to the, the, again, the bumblebee specific name dot DLL, which is the bumblebee payload. Now, if anyone's curious, you can see this for yourself in any version of windows, open, a command prompt and type O D B C C O N F space forward slash question mark.
Leo Laporte / Steve Gibson (01:26:02):
And you'll receive a popup from O D B C C O N F showing a list of its command line options. And sure enough, among them is slash F which takes a response file as its argument. Basically, it's a command stream, which is fed into O D B C C N F. So in this case, this loads and runs the bumblebee dot DLL at which point, all is lost because a hostile executable has made it into the user's system and has been started the bumblebee DLL injects code into multiple running processes in order to establish a strong foothold on infected endpoints and the newly launched OD B C O NF dot XE process creates windows management instrumentation calls to spawn two new processes from the WMI P I VSE dot XE, which is the windows management instrumentation provider service. Once again, both of these newly spawn processes are existing windows executables, where malicious code is dynamically injected into their process space once they've been started.
Leo Laporte / Steve Gibson (01:27:30):
So the first of the two is w a BM I dot XE. That's the Microsoft contacts import tool it's injected with met interpreter. Agent code met interpreter is a Melo attack payload that provides an interactive shell from which an attacker can explore the target machine and execute code it's deployed using in memory DLL injection. As a result met interpreter resides entirely in memory and writes nothing to disk. The second windows, the second existing windows XE that is spawned and then injected into is w a B dot XE that's Microsoft's address book app after being launched, it receives an injection of the cobalt strike beacon, which we've covered. We did a podcast on it a while ago. Bumblebee performs privilege escalation by loading an exploit for CVE 20 20 14 72 0 log on which we talked about at the time into run DLL 32 dot XE, Bumble B uses a user account control, you know, UAC bypass technique to deploy postex exploitation tools with elevated privileges on, on infected machines specifically, it uses an existing trusted binary.
Leo Laporte / Steve Gibson (01:29:07):
Again, parta windows F OD helper dot exc. This prevents windows from showing a UAC window when it's launched F O D helper is the executable used by windows to manage features in windows settings, again, living off the land, and it uses this to bypass any appearance of what's going on. This F OD helper is exploited to run CMD dot XE slash C space, and then run DLL 32 dot XE. Then we give it the DL, which is the, a path to the cobalt strike DLL, and then main pro where the cobalt strike DLL is the cobalt strike framework. Beacon and main proc is the exported is the, is the exported function, which cobalt strike exports in its DLL in order to run. As we know, cobalt strike is an adversary simulation framework used to assist in red team attack operations. Unfortunately, bad guys use it to conduct actual post intrusion, malicious activities.
Leo Laporte / Steve Gibson (01:30:27):
It's a powerful modular framework with an extensive set of features that are used to, you know, to you can do command execution process, injection, credential theft, and more. And speaking of credential theft after obtaining its foothold and elevating itself to system privilege without any further user interaction or UAC permission, Bumble meet performs credential theft through two methods. The first method is to trigger a memory dump of windows LS, a SS process LS. A SS is windows, local security authority, subsystem service with within LS, a S S's memory footprint are the keys to the kingdom, including both domain and local usernames and passwords. They're all sitting in the memory space of the LS, a SS process. So bumblebee dumps the memory of this process using proc dump 64, do XE, also living off the land to obtain access to this sensitive information. The second method of credential theft used by bumblebee is registry hive extraction using good old reg dot XE.
Leo Laporte / Steve Gibson (01:31:51):
The H key local machine Sams, a M, which is the security account manager database is where windows stores information about user accounts. That's dumped H key local machine security, which is the local security authority, the LSA stores, user logins, and their LSA secrets and HK local machine system contains keys that could be used to decrypt and crypt, the LSA secret and Sam database bumblebee issues, three commands of the form, reg do XE space, save space, HK LM slash Sam, and then a path to the program where that registry hive should be saved. In this case, they give the example C colon slash program data slash M dot SAV, then the same command for slash system and for slash security, saving their dumps into system.save and security.save. So that creates a trio of files containing the dump of those three system, critical registry hives. Then the LS, a SS dump, and those three registry hives are all compressed using seven Z.
Leo Laporte / Steve Gibson (01:33:14):
And exfiltrated back to command central at that point, the human operators behind bumblebee process, the retrieved credentials offline attempting to extract clear text passwords, the observed time between credential theft and the next activity is about three hours. So, so this stuff all goes back to wherever somebody ruminates on it, figures out what the username and passwords are. Basically reverse engineers, clear text, and then comes back three hours later after the attackers have gained a foothold within the organization's network, they gather information using tools such as NL test ping net view, task list, and ad find to collect a wide range of information related to the organization. They collect information such as the domain names, users hosts and domain controllers. We talked about ad find in episodes 7 89 and 90 back in October of 2020. It is a powerful, active directory exploration tool meant to aid in the administration of active D active directory systems by regular active directory admins.
Leo Laporte / Steve Gibson (01:34:39):
Unfortunately, it's been turned against those administrators, Bumble B uses cobalt strike agent for lateral movement, their analysis that is the the cyber reasons analysis observed multiple connections from the cobalt strike process to internal addresses on RDP, you know, remote desktop protocol over TCP port 3, 3 89. And of course now they've got credentials for all that stuff. So they're able to log in after lateral movement, the attacker persists on the organization's network using the commercial remote management software. Any desk after the attacker has obtained a highly privileged username and password, they access the volume shadow service shadow copy, which is again, built in windows, built in facility to create backup copies and snapshots of computer files or volumes while they are in use. So Bumble B accesses the remote active directory machines using the windows management instrumentation command line, w M I C, and creates a shadow copy using the VSS admin command.
Leo Laporte / Steve Gibson (01:36:03):
In addition, the attacker steals the NTDs dot DT file from the domain controller, NTDs dot D I T is a database that stores active directory data, including information about user objects, groups, and group membership. And the file also stores the password hashes for all users in the domain, in order to AB to obtain maximum privileges on the active domain on the active directory domain, the threat actor executes the following four steps creates a shadow copy of the machine files volume lists all available shadow copies, storing the result in a file copies, the active directory database, that NTDs dot di file as well as registry hives containing credentials and sensitive data from the shadow copy compresses the output directory for exfiltration. And finally, the threat actor uses a domain administrator account obtained previously to move laterally across multiple systems. After initial connection, they create a local user, an exfiltrate data using the open source R clone software Wikipedia.
Leo Laporte / Steve Gibson (01:37:29):
It describes our clone. A clone is an open source multithreaded command line computer program to manage or MI or migrate content on cloud and other high latency storage its capabilities include sync transfer, crypto cash, union compress, and Mount the R clone website lists supported backends, including S3 and Google drive in the instance observed and monitored by cyber reason, the Arone XE process transferred approximately 50 gigabytes of data to an end point with an IP address over TCP port 22, SSH located somewhere in the us. So what does all this tell us the first and most obvious thing we've learned is that you do, you do not want to have your enterprise stung by the bumblebee loader. It's definitely, it'll definitely ruin your whole day, but speaking of day, cyber reason compiled the entire event into a timeline, taking everything we've just stepped through. Here's how it stretches out in time.
Leo Laporte / Steve Gibson (01:38:50):
So we have T zero at initial access, you know, when the unwitting user clicks, the link thinks they're doing the right thing, opens the archive mounts. The ISO runs the, the, the, the program inside. Actually it's a link file. They'll be contained in the ISO reconnaissance using NL test net. And who am I commands at T at, at T zero plus 30 minutes. When we get to four hours, we're at command and control loading. The met interpreter agent also at four hours is privilege escalation using the zero login exploit two hours later at T zero plus six. We have command and control with cobalt strike beacon execution. Also at the same time, credential theft through the registry hive reconnaissance 30 minutes later at six hours plus 30 using ad find the active, direct, refined, ping, and curl at. Okay. Now we have a big jump at T zero plus 19 hours is the credential theft and privilege escalation that's when we get the LS, a SS memory dump with proc dump 64 dot XE that was at to plus 19 hours at 22 hours.
Leo Laporte / Steve Gibson (01:40:23):
So three hours later, credential theft using that. That's where NTDs dot did exfiltration occurs with active directory, full privilege, two hours later. Now we're at one day later, 24 hours later than the initial T zero is lateral movement using cobalt strike Sox tunnel over RDP and data exfiltration using R clone, presumably finished at T zero plus three days. So a full 72 hours from start to finish. So this thing, as I said, isn't over before it starts, it does take some time. There either is a human in the loop at that point where the registry hives and the LS a S S dump have been, have been compressed with seven Z and sent back to headquarters. Three hours goes by before they've got that figured out. And then they come back to do some real damage using all of the, the, the credentials that they've been able to obtain.
Leo Laporte / Steve Gibson (01:41:33):
So, one lesson we learn from all of this is why local privilege, escalation vulnerabilities form such a crucial part of this. And so many attack chains. Remote code execution sounds like the worst possible nightmare. And indeed, it's not good, but none of that was needed here. If malware were truly constrained within a user's low privilege account, much less damage could be done. But the old saying if wishes were horses, Biggers would ride reminds us that wishing won't make it. So with everything we've seen of the continuing and apparently worsening trouble, Microsoft is having securing windows, which they refuse to just leave as is you know, and fix because it's obvious, you know, they can't do both. There is virtually zero chance that once a single piece of malicious software gets loose inside a user's machine, that the rest of the organization will not fall.
Leo Laporte / Steve Gibson (01:42:49):
And this brings us back to that first fatal click, that innocent action taken by a user on the inside that initiated the collapse of even the most carefully constructed enterprises, security, those in charge of their organization's security must be living in a state of constant terror over what any one of their employees might do next. Right. Let and what we see here <laugh> yes, yes. And what we see here with bumblebee loader is exactly what transpires it's interesting. It's educational once in a while to go through the step by step of, of how these things work. It's fascinating. I think it's important cuz it helps make it real for people. Yeah. It's like, you know, oh, that happened to somebody else. It's like, here's exactly how this could happen to you.
Leo Laporte / Steve Gibson (01:43:45):
Yeah. Well, there you go. If you haven't seen the show notes, this would be a good time to get 'em and look at that step by step and really understand what, what the thread is. The show notes are@grc.com that's Steve's website. You also can get, of course copy the audio. He's got 16 kilobit audio, 64 kilobit audio and very nice transcripts as well. Plus the show notes. I think the transcripts and show notes are gonna give you all the additional detail you need while you're at GRC, pick up a copy of spin, right? Steve's bread and butter. The world's best mass storage, maintenance and recovery utility version six is current. But if you buy six today, you get six one when it comes out and Steve's working hard on that all the time. I know, except when he is reading this book and then, you know, all bets are off <laugh> he's almost done.
Leo Laporte / Steve Gibson (01:44:34):
Yeah, <laugh> he's a fast reader. Don't worry. <Laugh> I am actually after the fact you can also get on demand versions at our site, TWiT the TV slash SN we've got audio and video for you. I don't know why you'd want video, but you could get it. Well I know why, so you could see the video of our our image of the week. That's why. Yeah. The satellites movie, it's a video spooky. It's spooky. Yeah. You also let's see what else? Oh, there's a YouTube channel. You can watch. In fact, a good way to share clips is on the YouTube channel. Cause they have the feature to do the little clip thing. And of course you can also subscribe in your favorite podcast player and get it automatically. The minute it's available, just search for security. Now it's been around as you know, 18 years now everybody should have a copy of it somewhere.
Leo Laporte / Steve Gibson (01:45:26):
<Laugh> keep it up. That's actually how Michael first wrote to us, he wrote me note saying, come, I only see the last 10 episodes in the, in the feed. And we just do that to keep the feed from getting big. If we all had 885 episodes in there, it'd be hundreds and hundreds of megabytes. And we don't want you to have to download that on a regular basis. That's kind of how feed feeds work. You know, you download it each time, so we keep it to 10 titles, but all the titles are available at Steve site and our site, you wanna watch us do it live, get the first edition, the very first edition while the ink is still wet, just go it's it's easy to do. Just go to live.twi.tv of a Tuesday, a round about one 30 Pacific, four 30 Eastern, 2030 UTC, right after Mac break weekly people who are watching live often chat with us live@ircdottwi.tv or in the club twit discord.
Leo Laporte / Steve Gibson (01:46:19):
After the fact you can chat and people often do in our community forums, Steve's got his own forums, grc.com. We also have ours@twi.community for all of the shows. And we also have a master on instance, which is a federated Twitter without all the security flaws that is at twit social, both are free to join. But I do approve everybody to keep the spammers out. So it might take a day or two for me to, to let you in, but please do do knock twi.community or twi.social. Steve, have a great week. Go finish your book. Thank you, my friend, that will, it will, unfortunately it will not live out the night because I'm not gonna be able to put it down and I'm close enough to the end. Although even at this point I I'm on pins and needles. I have no idea what's gonna happen.
Leo Laporte / Steve Gibson (01:47:09):
You're almost done done. You still don't know what's gonna happen. That's a good sign. It's really, it's really good. Yeah, you're good. Well, I just fought it and downloaded it. So I'll be listening as soon, actually, soon as I finish Stacy's book club, Claire on the sun, which is also excellent. It's about an artificial intelligence and artificial friend that you bring into your house to be your companion. And it's told from her point of view. So it's really fascinating. And that's our book club Thursday 9:00 AM Pacific for the club trip members. Thank you, Steve. Have a great week. See you next, everybody. Bye.