Security Now Episode 892 Transcript
Please be advised this transcript is AI-generated and may not be word for word. Time codes refer to the approximate times in the ad-supported version of the show.
... (00:00:00):
It's time for security. Now, Steve Gibson is here. Boy, he has a lot to talk about. A new job offer from the nsa, <laugh>, you won't believe the meme they chose. We'll also talk about Uber's cto. He's been convicted of a heinous crime. You won't believe it when you hear it. And then he's gonna talk about his discovery of a lovely little single board computer I know many of you are gonna wanna buy plus a look at Source Port Randomization. It's a big show and it's all ahead. Next on Security Now podcasts you love from people you trust.
Leo Laporte / Steve Gibson (00:00:43):
This is Security now with Steve Gibson, episode 892 Recorded Tuesday, October 11th, 2022. Source Port Randomization. This episode of Security Now is brought to you by Secure Works. Are you ready for inevitable cyber threats? Secure Works detects evolving adversaries and defends against them with a combination of security, analytics and threat intelligence directly from their own counter threat unit. Visit secureworks.com/twit to get a free trial of contagious extended detection and response, also known as xdr. And by New Relic, use the data platform Made for the Curious. Right now you can get access to the whole New Relic platform and 100 gigabytes of data per month. Free forever, no credit card required. Sign up a newrelic.com/securitynow and buy bit warden. Get the password manager that offers a robust and cost effective solution that can drastically increase your chances of staying safe online. Get started with a free trial of a teams or enterprise plan or get started for free across all devices as an individual user at bitwarden.com/twit.
Leo Laporte / Steve Gibson (00:02:00):
It's time for security. Now with this guy right here, Steve Gibson, the star of our show. Hello Steve <laugh>. Yo, Leo, I've silenced my phone so we won't be interrupted by No Yabadabadoo, no Yabadabadoo. Looking forward to the day when I have to shut those off cuz they're so annoying Every five seconds. Another not there. Yeah, not there yet, but I'm working in that direction. I have some news on that front that I'll share later. So we're episode 8 92 for October 11th and I titled this one Source Port Randomization, which is a subject we've spoken of often, but it came up again as a consequence of a mistake that the authors of the Linux kernel recently fell into. So I think that's gonna be interesting. I know that we have a large Linux following among our listeners, the ticky, most of ours. So we're gonna look at first a massive customer information leak, which arose from a surprising source.
Leo Laporte / Steve Gibson (00:03:11):
Also meta notes that they did some analysis to discover where their users credentials are being most harvested. And in an weird industry, first Uber's ex CTO has been convicted of some interesting misbehavior. Oh, no kidding? Yeah, we talked about that when it happened. I think when you got caught anyway. Yes. Yes. And that was two years ago that the allegations were made and that the indictment happened last week. So we have more, much more. Or I mean he today the outcome of the trial rather he was found guilty. We'll talk about that. We've got more, much more cryptocurrency industry turmoil, <laugh> which just nonstop. Oh my God, Leo. But I mean it's just, it's like it's creative turmoil. It's like what? We also have a new appointee in the UK a month ago who has decided that she wants to drop the UK's use of the gdpr.
Leo Laporte / Steve Gibson (00:04:21):
We oh, also the NSA is looking for next summer interns. I'll provide information for our listeners who might be interested in signing up. IBM has learned that incident responders are feeling quite stressed out and Microsoft continues to fumble their exchange server response to the most recent exchange server problems that we started talking about last week. As I mentioned, I've got news of spin, right? And I'm gonna share my discovery of a lovely little single board computer. Basically Steve's dream sbc. and then after sharing some listener feedback, as I said, we're gonna look at a recent mistake made in the Linux kernel that allowed its users to be tracked online. Oh, I thought you were gonna talk about the recent mistake in the Linux NEL that would fry some users monitors <laugh>, Did you see that? No. Yeah, they were warning people not to download the new kernel.
Leo Laporte / Steve Gibson (00:05:21):
Wow. I think they fixed it. But yeah, because something, I mean that's amazing that you could do something in software that would destroy hardware back in the c RT days. It was possible to mess up the h and v sync in a way that would actually damage the circuitry. But yeah, in an LCD world that's look into it, I'll find out what it is and I'll let you know. But first a word from our sponsor. We love our sponsors. They make security now possible and today we're sponsored by the good folks at Secure Works who are here to help. By the way, for your next incident, I'm gonna give you an 800 number in a second. I want you to write it down. Secure Works is a leader in cyber security. I know you know their name. Building solutions for security experts by security experts.
Leo Laporte / Steve Gibson (00:06:11):
Secure Works offer superior threat detection and rapid incident response all while making sure customers are never locked into a single vendor. This month October is cyber security awareness months perfect. It's spooky. Spooky season and cyber security Awareness month now is a good time to raise awareness about digital security and empower everybody to protect their data from cyber crime. SecureWorks has the perfect solution. In fact, now would be a great time to get contagious X D R in 2022. Cyber crime will cost the world 7 trillion this year by 2025 and three years to figure 10.5 trillion trillion with a T trillion in 2021 last year, ransomware totaled 20 billion in damages and it attacks occurred every 11 seconds that we know of. But by 2031 ransomware is projected to cost 265 billion every year and strike every two seconds. And honestly, I think that's an optimistic prediction. I think it's gonna be far worse.
Leo Laporte / Steve Gibson (00:07:15):
So you need to make sure your organization is not the next victim with SecureWorks Contagious. XDR SecureWorks Contagious provides superior detection, identifying more than 470 billion security events every day and then prioritizing the true positive alerts by scrubbing out the alert noise and allowing organizations to focus on the real threats and they're out there. In addition, Contagious offers unmatched response, automated response actions. That's important because they can eliminate threats before damage is ever done. Now that fast with SecureWorks contagious managed xdr, you can easily leverage Secure Work's experts to respond and investigate threats on your behalf, which means you cut dwell times, decrease operational burden, reduce cost, and with 24 7 by 365 coverage, it doesn't matter whether you experience a Christmas Day security event or half your teams out sick, you know could trust that SecureWorks has your back. Many companies right now are facing in fact a shortage of security talent.
Leo Laporte / Steve Gibson (00:08:22):
Secure Works Act as an extension of your security team on day one, alleviating cybersecurity talent gaps, allowing you to customize the approach and the coverage level you need. And remember I said there's a number to call. If you've already found an intruder in your system, you do not have to worry. Write down this number whether you're a customer or not. 1-800-BREACHED, 1-800-BREACHED. That number will connect you with the Secure Works Emergency Incident Response Team. They're there 24 7 are there to help you, provide you with the assistance you need. They can respond to, they can even remediate a cyber incident or data breach on the spot. So remember that number 1-800-BREACHED at Secure Works. You'll learn more about the ways today's threat environment is evolving and the risks they can present to your organization, including case studies. They've got reports from their very prestigious, very smart counter threat unit and more. Visit secureworks.com/twi, Get a free trial of Tais should tell you stands for Extended Detection and Response and that's what Secure Works does. Secure works.com/twitter secure works defending every corner of cyberspace. secureworks.com/twi. Thank 'em so much for their support and for the very important work they do, not just for their customers, but for all of us. Speak of important work. Steve Gibson has the picture of the week <laugh> this is just kind of crack me up for those who are not seeing the show notes or the video.
Leo Laporte / Steve Gibson (00:10:01):
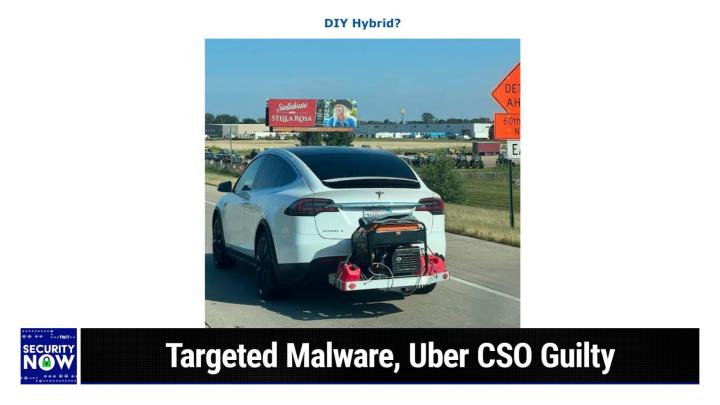
What we have is a Tesla clearly recognizable by everyone that apparently doesn't have much faith in its ability to find the next charging station. And so I titled this DIY hybrid strapped to the back of it in what looks like sort of a permanent installation. It's got a gas electric, a gas powered electric generator, and a bunch of gas cams. So I guess if the battery runs low, this thing being sort of a DIY hybrid, you'd just cruise off to the side of the road gas up the generator, plug your car into itself into this little caboose that it's got and charger back up and then you're ready to go again. So anyway, not specifically anything about security, but I just thought this was kind of humorous. Yeah interesting. The first piece of our show was a tweet that came from our last week topic source ram.
Leo Laporte / Steve Gibson (00:11:16):
Remember Jacopo teddy osi? He was one of the two Italian researchers who discovered the serious Akamai vulnerability. Anyway, he knew about the podcast and he said thanks at SG GRC for talking about my Akamai vulnerability on the Security Now podcast. And he gave a link to it at twit Do tv. I saw that tweet. That was so cool. Yeah, it was very cool. And he said the analysis and explanations you made were very accurate explanation point. So anyway, Jacob Cobo, thank you for he didn't he him up? He didn't call you out on mispronouncing his name though. And I actually, I replied to him politely thanked him for his tweet. I said, I hope I didn't mango the pronunciation of your name too severely <laugh>. So right. He's probably used to it. Oh goodness. So it turns out that there's a non-security breach way, like a means for a user of a cryptocurrency exchange to have their name, their account balance, and all of their transactions exposed to the public.
Leo Laporte / Steve Gibson (00:12:28):
And that's if the currency exchange files for bankruptcy. Whoops. Something known as the Celsius Network cryptocurrency platform deliberately exposed the names and complete transaction histories of hundreds of thousands of its customers. Okay, now timeout as an aside, hundreds of thousands of its customers. Leo, what most mystifies me is how these random also ran startups acquire hundreds of thousands of customers. What are people thinking? Who are these people? And it's just a mystery. Anyway, the company filed a get this 14,532 page document because of course lots of transactions for all of its hundreds of thousands of customers, thus requiring a 14,532 page document as part of its bankruptcy proceedings the week before last that contained the names and recent transactions of every user on its platform. The judge in this case allowed the bankruptcies, Judge allowed the company to redact the document, but only their customer's physical and email addresses were allowed to be removed because the rest of the information was required in their disclosure during their regular bankruptcy procedures and proceedings. So the document for anyone who's interested is available via PACER and other legal document portals. So no, not so private. If the cryptocurrency platform that you're using goes belly up and chooses this means of shutting themselves down. Just something to keep in mind.
Leo Laporte / Steve Gibson (00:14:25):
A posting last Friday by two security focused employees of Meta Facebook's parent disclosed the results of a recent search through the Apple and Google app stores. They explained that they had identified more than 400 malicious Android and iOS apps targeting Facebook's users, which were being used to steal specifically. I mean the reason these apps were created was to steal their Facebook login credentials. They reported their findings to Apple and Google and have asked the users they identified to change their passwords since their credentials have almost certainly been compromised then. Now I thought that the nature of the come ons to entice the downloads of these apps was interesting. So were first of all, majority were photo editors including those that claim to allow you to turn yourself into a cartoon. Those apparently are very popular among Facebook users. Also, we had VPNs claiming to boost browsing speed or grant access to blocked content or websites.
Leo Laporte / Steve Gibson (00:15:40):
In other words like solving a problem that people have. Oh, whether this will make your browsing twice as fast, whatever, probably not true, but it got them to download. Also phone utilities such as flashlight apps, <laugh> that claim to brighten your phone's flashlight, yes, get more light outta your flashlight if you download this phone utility. Then we had mobile games which were falsely promising higher quality 3D graphics, health and lifestyle apps, horoscopes and fitness trackers business or ad management apps claiming to provide hidden or unauthorized features not found in official apps which are being offered by the tech platforms. So interestingly by far the majority at nearly half, 42.6% of those 400 plus apps were all photo editors, very popular. Next, dropping down to 15.4% were the business utilities, then the phone utilities at 14.1% and games at 11.7 and the others making up they the result. So standard advice applies, first of all, try hard. I mean really try to avoid downloading just every tasting tasty looking goody that you see.
Leo Laporte / Steve Gibson (00:17:09):
We've said this before and I think it's still true. There is a very small probability given the vast number of good apps that are out there. The probability is diminishingly small that something next, something more that you download, that you download will be malicious, but the probability's not zero. So if you can and you care about not having malware running in your device, don't do it. And don't be too quick to click the download link, Do as much research about the app and its reputation as possible and I would suggest you do that off the platform that is go elsewhere. Don't rely on that in place reputation because the other thing these guys are known to do is to load themselves up with faked five star ratings and thumbs up and things. So look elsewhere for other sources of reputation. So again, be careful, be cautious, but just know as we've noted before, that some percentage of these things in the app stores, much as Apple and Google, both are trying diligently to keep these things clean and scrubbed.
Leo Laporte / Steve Gibson (00:18:34):
They exist for a while on this app platform. Okay, Uber's former cso, their chief security officer by the name of Joe Sullivan, was found guilty at trial due to his actions following a 2016 data breach at Uber. And I'm wording this carefully because there was actually some misreporting about this in the press. It's like the implication was for reporters who are not being careful that Joe was responsible for the breach. Not at all the case, right? I mean he's a C-suite guy, those guys don't get their hands dirty. Anyway, we'll get to that in a second. Reading from a statement made on August 20th, 2020. So as I said two years ago when these charges were filed in the northern district of California, they put out a statement about the fact that this was being done. They said the complaint describes how Sullivan played a pivotal role in responding to Federal Trade Commission.
Leo Laporte / Steve Gibson (00:19:47):
FTC inquiries about Uber's cyber security. Uber had been hacked in September, 2014. Okay, so that's a different, that's two years before a different instance had been hacked in September, 2014 and the FTC was gathering information about that 2014 breach. The FTC demanded responses to written questions and required Uber to designate an officer to provide testimony under oath on a variety of topics. Sullivan assisted in the preparation of Uber's responses to the written questions and was designated to provide sworn testimony on a variety of issues On November 14th, 2016. So near the end of 2016, approximately 10 days after providing his testimony to the ftc, Sullivan received an email from a hacker informing him that Uber had been breached. Again, Sullivan's team was able to confirm the breach within 24 hours of his receipt of the email. Rather than report the 2016 breach, Sullivan allegedly took deliberate steps to prevent.
Leo Laporte / Steve Gibson (00:21:04):
Now this is allegedly cuz it's two years ago now. It's been found to be true at trial, allegedly took deliberate steps to prevent knowledge of the breach from reaching the ftc. So he tried to bury this. For example, they said Sullivan sought to pay the hackers off by funneling the payoff through a bug bounty program. Uber paid the hackers $100,000 in Bitcoin in December of 2016 despite the fact that the hackers refused to provide their true names. In addition, Sullivan sought to have the hackers sign non-disclosure agreements. The agreements contained a false representation that the hackers did not take or store any data when in fact they had, When an Uber employee asked Sullivan about this false promise, which was in the non-disclosure, Sullivan insisted that the language stay in the non-disclosure agreements. Moreover, after Uber personnel were able to identify two of the individuals responsible for the breach, Sullivan arranged for the hackers to sign fresh copies of the non-disclosure agreements.
Leo Laporte / Steve Gibson (00:22:22):
That piece now, yeah, don't tell anybody what happened and oh by the way, now that we know who you are, we want you to actually execute the non-disclosure agreements, which will be binding under your true names when they gave him a bug bounty. Yes, Yes. Yeah. We're just gonna say that you found a problem, not that you actually attacked us using it. Appalling Yes though. So the new agreements retained the false condition that no data had been obtained. Uber's new management ultimately discovered the truth and disclosed the breach publicly and to the FTC nearly a year later in November of 2017. Since that time, Uber has responded to additional government inquiries. So all of that was proper. The criminal complaint against Sullivan alleges Sullivan deceived Uber's new management team about the 2016 breach. Specifically Sullivan failed to provide the new management team with critical details about the breach.
Leo Laporte / Steve Gibson (00:23:31):
In August of 2017, Uber named a new chief executive officer, a new ceo. In September of 2017, Sullivan briefed Uber's new CEO about the 2016 incident by email. Sullivan asked his team to prepare a summary of the incident, but after he received their draft summary, he edited it. His edits removed details about the data that the hackers had taken and falsely stated that payment had been made only after the hackers had been identified. That wasn't the case. The two hackers identified by Uber were prosecuted in the northern district of California. Both pleaded guilty on October 30th, 2019, took computer fo fraud conspiracy charges, and now a await sentencing. The criminal complaint makes clear that both hackers chose to target and successfully hack other technology companies and their users'. Data after Sullivan failed to bring the Uber breach to the attention of law enforcement. In other words, by not dealing with law enforcement forthrightly, the hackers who'd been identified continued to roam free to hack and damage other companies as a direct consequence of Sullivan's actions of covering all this up.
Leo Laporte / Steve Gibson (00:24:59):
So at trial, Sullivan was found guilty of lying to authorities and obstruction of justice. Those were the charges lying to authorities and obstruction of justice. Nothing to do directly with Uber being hacked. It's like we know that kind of thing happens. The trial, however, was a landmark case being the first time a chief security officer faced criminal charges indirectly at least relating to a security breach. Though it was only obviously indirectly about the breach itself. Joe's big mistake was his attempt to cover up and mislead investigators and ultimately landed him as we know now in some very hot water. Interestingly, Joe was once a prosecutor in the same office that had charged him. I didn't know that. <laugh>. Yeah, he should have known better. Well, I was thinking that maybe he thought he knew how to finesse the system, right? Having once worked there, he figured, Hey, I know how to get around this.
Leo Laporte / Steve Gibson (00:26:06):
Gee. So he now faces up to eight years in prison and up to half a million dollars in fines, which will be determined at his upcoming sentencing hearing. What has never been made clear in the reporting that I've seen is why he did this. He was a C level executive for a major corporation. Uber guys at that level aren't pulling wires and getting their hands dirty. They attend meetings and golf. So it was almost certainly not directly Joe's fault that somewhere in a back room to attackers somehow crawled into Uber's network. What I wonder is whether he had a big hunk of Uber's stock that he worried would collapse in value if the news of this got out. Yes, if so, perhaps he believed that he could cover the whole thing up from the top to protect Uber's market value. In any event, I imagine he regrets that decision now can't spend that stock in prison.
Leo Laporte / Steve Gibson (00:27:10):
No, you can't <laugh> No. So more cryptocurrency, chaos. I believe that this podcast listeners would be well served for me to periodically note the ongoing chaos that exists within the cryptocurrency world. It's not my position to advise anyone of anything, but being armed with realistic viewpoints can only be valuable. To that end, the news is that the multi cryptocurrency exchange platform, Binance was hacked. Binance has paused. Its Binance smart chain, bsc, as they call it, blockchain bridge after a threat actor used an exploit there to generate and steal 2 million bin coins that the abbreviation for that currency is B and b, that they're currently worth around 560 million. Now the thieves we're unable to make off with all 560 million because B Binance reacted quickly to what they discovered. But the bad guys still absconded with 20% of the 560 million in illegitimately created funds. So 112 million worth of the Binance coins.
Leo Laporte / Steve Gibson (00:28:43):
So not bad for day's work. We were talking about this on Sunday on TWI and apparently the bridge software which is what allows you to move crypto from one place to another right is a very common source of hacks. And this is the fourth of fifth massive hack of a crypto bridge of some kind in the last couple of years. It's a huge vulnerability and of course that's where the money is. It's like you could tap into the oil pipeline and just say, yeah, gimme some of that <laugh>. Yeah. Wow. Okay. And so while we're on this subject of bad ideas, I'll also note that the Z cash blockchain has been subjected to a spam attack. Yes. Spam isn't just for email anymore, <laugh>. This was done by creating bloated but inexpensive shielded transactions on the Z Cash blockchain. And as a consequence of this attack, which has been underway since June, the size of the Zcash blockchain has more than tripled to over 100 gig as the Z cash blockchain has grown huge, purely as a function, as a result of bogus transactions. You have to store every one of these tiny transactions. Yes, the crypto cryptocurrency experts now expect Z cash node servers, which must retain a full local copy of the entire blockchain to start failing due to memory shortage.
Leo Laporte / Steve Gibson (00:30:29):
All of this points, the only way that you can regard this is to an extremely immature technology coupled with a gold rush attitude. Recall then the actual California gold rush between NI 1848 and 1855 with very few exceptions. The only people who made money were those who were selling the gold digging, panning and sling supplies to the hopeful mins. It wasn't those who were panning for gold, it was the people who sold them their pans. No, in fact, I saw it just the other day at auction, a pair of Levis fan and old coal mine from the 1880s sold for $76,000. So they're still making money, Still making money and you know, can't get graphics cards anymore, right? Because all of the mining rigged, that's sucked up all the gps you can because there there's no more money to be made because of proof of work, proof of stakes.
Leo Laporte / Steve Gibson (00:31:41):
So now you can get a lot of highly used <laugh>, GPUs, <laugh> flooding the market. I think this would be a good time to take a break. And then we're gonna talk about the UK's plans to drop out of the gdpr. And actually I've in conjunction with NFTs, I've been saying this for a while, the companies that make money in NFTs are the people, minting them. They're collecting, yeah, they're collecting the gas fees. Well Kevin made 50 million his proof collective and then he raised another 50 million <laugh> because it's such a good, where is this money? Who are these people? They're this there something I hope I something I sincerely hope that for the most part they're Bitcoin bros. They're crypto millionaires and billionaires who are really like the win the win. The Winkle dinghies are the Winkle dings down and I pray it's them and not some poor work and stiff who says, Yeah, my stocks aren't doing so well, maybe I'll get into this crypto thing.
Leo Laporte / Steve Gibson (00:32:43):
But unfortunately because Robin Hood and all these other easy trading apps sell crypto now I suspect that a lot of this is coming from people who can't afford the losses and it's very sad. Of course my stock market portfolio is stumbled even more so maybe <laugh>, I should buy some Bitcoin, a little doe who knows our show today. Product to you by New Relic. I am as a big fan of developers, Engineers are smart, they're curious, they first is try new technology. They actually wanna know how things work and why they work. They're the ones that read the documentation. Why so many engineers? So one of my favorite people turn to New Relic because New Relic gives you the information, the data you need to know about what you build. It shows what's happening in your software life cycle and your entire software stack. One place.
Leo Laporte / Steve Gibson (00:33:41):
You don't have to look into a bunch of different tools and then kind of correlate them. Somehow make the connections in your brain or manually the tools you need all in one place. A single pane of glass as they say. So you could see exactly what's happening. You could pinpoint issues in your software stack down to the line of code. You know exactly what's going on, why there's a problem and you can fix it quickly. That's why dev and ops teams at Dash and GitHub, Epic games more than 14,000 other companies use New Relic to debug and improve their software. When teams come together around data, real data lets you triage problems and be confident decisions reduce the time needed to implement resolutions because you're using data not opinions. Use the data platform made for you, made for the curious right now you get access to the whole New Relic platform and a hundred gigabytes of data per month.
Leo Laporte / Steve Gibson (00:34:38):
Free forever, a hundred gigabytes of data a month, the entire New Relic platform all their tools free forever. Sign up at newrelic.com/securitynow New relic.com/security. Now I don't know why you wouldn't do this. Go right now. Get that free. I wanna say trial, it's not free trial. Get that free service forever. No credit card required. New Relic, r e l i c.com/security. No, I figured I was probably an old Relic <laugh>. So I just looked up the definition. It says an object surviving from an earlier time. <affirmative> especially one of historical or sentimental interest and bingo think that works. Bingo, I'm doing, I'm old rather I'm getting ready for my, I love the advent of code coding competition in December. I'm getting ready for it and I'm trying to do in LI and I'm sitting there and wait, I thought you were gonna do a new language.
Leo Laporte / Steve Gibson (00:35:38):
I was looking at Julia and then, but you convinced me anything that starts indexes raises at one oh as no. Mm-hmm I know. I really love Li. So I'm on day seven of the first year 2015 and I need to do bit wise operations and I'm thinking if I were Steve <laugh>, this would be easy. <laugh>, he lives in the bits, but now I got integers and I gotta figure out and actually it's not a problem except when I get to the twos compliment representation, I'm getting numbers going negative and I've gotta figure out a way to just ignore that you didn't have to think about it. Yeah, of course There are an amazing number of really cool bit wise hacks that I know. In fact, I have a book that's almost entirely bit wise. Hacks. I was gonna ask you this cuz I wanna give it to you.
Leo Laporte / Steve Gibson (00:36:26):
Have you ever read Hacker's Delight? No. Okay, don't buy it <laugh>. I am gonna send it to you. It is the classic and it is almost entirely weird bit wise hacks and sort of edge cases that turn out to be useful. That yeah, that's the whole idea is once you know this, yeah, idiom, you'll use it all the time and you of all people cuz you work in Assembler, this is gonna be like, oh yeah, you probably know 90% of them, but it's a good book. I'll send it to you. That's fun. Cool. Thank you. You're welcome. Okay, so I'm not sure whether this is good or bad though. I'm leaning heavily toward bad for a reason. I'll explain. Last Monday, Michelle Donlan, the UK Secretary of State for digital culture, media and Sport. That's literally her title. The UK Secretary of State for Digital Culture, Media and Sport.
Leo Laporte / Steve Gibson (00:37:25):
Luckily Leo, for your sake, they didn't say cyber <laugh> sports bad enough. <laugh> sports bad enough. I agree that one I like I said wait a minute, I is that we don't have in this country, we don't have a minister of sport, but surprisingly a large number of countries do. And I watch. Reason I know is I watch the Formula one race but don't understand it's plural Sports'. Sports, it's supposed to be sports and they call, there's only one math and sport. It's not like it's I'm playing card, I'm playing cards <laugh>, but it's maths plural. So go figure. What is it? Winston Church Winston Churchill said, is American England two countries separated by the same language. <laugh> <laugh>. So she was appointed to her position of digital culture, media and sport. About a month, about a month ago, on this last Monday, she announced plans for the UK to drop the EU GDPR in favor of designing their own, I know their own new data protection system.
Leo Laporte / Steve Gibson (00:38:39):
And this is the point where I've grown Michelle has, she was speaking at the conservative party conference in Birmingham where she said that the UK government will look to pass new legislation inspired by data protection laws used in Israel, Japan, South Korea, Canada, and New Zealand. Now on the one hand that sounds maybe better than the gdpr, but the concern is that we only have the one single global internet and that was the whole point of the internet in the first place. That's what makes it so useful and amazing. But now governments are getting into the act of deciding how the internet should uniquely treat each of their own precious citizens. Even if that differs from how the internet treats everyone else. Governments want to have borders, but the internet was designed to ignore them. And so basically we have a clash of fundamental principles here and it's gonna be a mess, Leo.
Leo Laporte / Steve Gibson (00:39:50):
And so my concern about the UK leaving the GDPR is, okay, now we're gonna have the UK PR or UK gdpr, who knows what, but wow, one more mess to deal with. Okay this seems cool. Rob Joyce is the director of cyber security at his Twitter handle is at nsa gov. He recently tweeted that the NSA is looking now looking for next summer interns. He wrote, It's never too early to make summer plans. Exclamation point at NSA cyber 2023 summer internships are open compsci and that's he's got a number for it. COMPSCI 1 9 1 8 1 3. Cyber security 1 1 9, 1 8 1 6 and engineering 1 9 1 8, 1 7. He says apply@intelligencecareers.gov slash nsa. Use the numbers above, find your passion. Hurry. Applications close on Halloween. So appropriate where? Yeah, we're in the Halloween month so the rest of this month applications are open to apply to the NSA for a summer insured internship. And you don't think this is a joke?
Leo Laporte / Steve Gibson (00:41:32):
No, I checked. It's at, I mean the picture is weird. Maybe they're try This is how somebody who is not at all cool tries to look like they're cool. I think it's a little creepy. <laugh>. It's a little weird. It is right from the Twitter feed. If you go to Twitter and do put in what's his handle again? It's Rob at nsa Cyber nsa. No, I'm sorry, NSA underscore gove. Nsa underscore CS director is the Twitter handle. But you could search for Rob Joyce probably, right, right. Rob Joyce, right nsa. And actually I did that and it came right up. So it's like that's actually what he tweeted. Wow. It reminds me, you nailed it. It's somebody who is not cool thinking what would the kids do? <laugh>? What's the meme exactly? What's the meme I could post? And then it does remind me a little bit of goodwill hunting and the very famous scene where they ask Matt Damon to apply.
Leo Laporte / Steve Gibson (00:42:41):
I can't remember if it's, I think it is the nsa. If you haven't watched that, that would be a good response. Oh, he's one of my favorite movies. And that's a great movie where he goes, he does a great monologue about, Well I'll tell you why I am not gonna work for the NSA <laugh>. It's really good. I'm sure. I'll tell you what, if you read the thread, the responses to this tweet, it will be in it. I almost am certain. Anyway. That's great. Okay, so IBM did a survey. We've talked a lot about the job opportunities available across the security industry. There are many, they are plentiful and they show no sign of diminishing. I think the stuff we talk about, the needs of the industries we describe are only growing greater, but they can be demanding and it can interfere with other life priorities.
Leo Laporte / Steve Gibson (00:43:38):
IBM recently conducted a survey of 1100 professional cyber incident responders. Here are the seven takeaways from the survey. First, cyber security incident responders said that the sense of duty to help and protect others and the businesses was by far the most influential factor. Attracting them to their profession. Continuous opportunity to learn and being rooted in problem solving, followed as the most influential factors. So people who want to help, that's cool. At the same time, number two, sense of responsibility toward their team slash client and managing stakeholder expectations were ranked as the most stressful aspects of responding to cyber incidents. Around half of the 1100 selected these among their top three stressors. So they were stressed by the sense of responsibility toward their team or client and managing stakeholder expectations, solving the problem for their bosses. Third takeaway, according to 48% of responders, the average incident response engagement is two to four weeks and nearly 30% say an incident response engagement lasts more than four weeks on average.
Leo Laporte / Steve Gibson (00:45:10):
The overwhelming majority states that it's not uncommon to be assigned to respond to two or more incidents that overlap. Fourth takeaway is that the first three days of responding to an attack are seen as the most stressful. Additionally, more than a third say are they're working more than 12 hours a day during the most stressful period of the engagement. The fifth takeaway is that 81%, so four out of five, a little over four outta five of cybersecurity incident responders think the rise of ransomware, no surprise has exacerbated the stress, psychological demands required during a cybersecurity incident response. Right? Cuz their enterprise is frozen and is under threat. Sixth takeaway two thirds, 67% of cybersecurity incident responders said they experienced stress and anxiety in their daily lives as a result of responding to an incident. And finally, nearly 65%, again, two thirds of cybersecurity incident responders have sought mental health assistance as a result of responding to cybersecurity incidents. Holy cow. Wow. To that end, the majority of respondents 84% did also say that they do have access to adequate mental health support resources. So they're able to get help, but I mean they're under tremendous pressure.
Leo Laporte / Steve Gibson (00:46:55):
Probably not chronically but acutely when something happens. So I think this suggests two things. First, cybersecurity incident response may not be for everyone. It's probably think about your personality type. Do you like adrenaline? <laugh> Are your adrenals in good shape and providing you with what you need? I think seriously, that should be consideration. It must be high pressure. I mean very intense when it happened. Probably a lot of times sitting around and then all of a sudden boom. Yes. Yeah. Yes. Imagine something gets into your network and it's doing bad stuff and it's up to you. I mean, it's not, not anybody else and alarms are going off and people's computers are crashing and it's like, yeah, that's not when you wanna slip the blood pressure cuff on your arm to see how you're doing. The other thought I had was that although you'll certainly want to be a salaried employee, if there's any way to work in bonuses to your contract for when the job does disrupt your life, that should be a consideration too.
Leo Laporte / Steve Gibson (00:48:16):
Being the only one left at work working all night while everyone else's home laughing and sleeping is much easier if you know that your special contribution is being valued with some additional compensation and if you have a significant other in your life, it could make it easier to explain to them, Honey, I'm sorry but I I'm come home anyway. I thought that was interesting. It is. We've, we've only talked about all the opportunities so far and this survey of 1100 people says, yeah, there's lots of opportunity but it's not a cakewalk all the time. If something nasty crawls into your enterprise that you're responsible for, it's probably a lot like being a first responder, a firefighter, an emt. Yep. A police officer. When things go haywire, they go and you have to be there and you probably need a certain kind of constitution. I think that's the case.
Leo Laporte / Steve Gibson (00:49:17):
Yeah, I think that's the case. Just pressure. Right? And I'm sure there are people who thrive on the idea of that much need being piled on them when their shoulders are able to handle the burden. We have a picture of that person here from there. <laugh>, NSA directors tweet. Yeah, <affirmative> <laugh>. Yeah. Okay, so speaking of being stressed out, something's going on over at Microsoft and it's not good. The topic is the status of Microsoft's mitigations for that pair of zero day exchange server vulnerabilities we discussed last week. Those were the new pair discovered while being used in the wild exploited in the wild in the networks of clients of that Vietnamese cybersecurity firm, GTS C first, in updating myself for today's podcast, I checked to see whether patches for these two new bad problems were available. That would be the optimal answer, right? Get it fixed, but after at least a week and a half and it turns out a lot more than that as we'll see in a second.
Leo Laporte / Steve Gibson (00:50:33):
The answer to that is no emergency patch for exchange server so far. Then says there was news last week that the initial mitigations proposed by Microsoft had immediately been bypassed. As I noted last week, I wasn't quite sure of some of the language, but bleeping computers said they confirmed those that original mitigation posed proposed by Microsoft has been bypassed. I went to see what Microsoft had done since then and they really appear to be chasing their tail. They updated their guidance for scripts for IIS mitigation on October 4th, fifth, sixth, seventh, and eighth. Each time their correcting typos or making small tweaks to the script, apparently trying to get it right. It's like what one of the comments has removed a space that was unnecessary. We can do <laugh> so bad. Oh God. So nothing about this response feels like the A team has been brought in.
Leo Laporte / Steve Gibson (00:51:47):
And then we learn that Microsoft has been aware of this problem for much longer than was previously known. They were in air quotes investigating it after become aware of it back in August in their posting titled Analyzing Attacks using the Exchange Vulnerabilities, CVE 20 22 41, 0 40 and 41 0 82. Microsoft wrote, S T I C, observed activity related to a single activity group in August, 2022 that achieved initial access and compromised exchange servers by chaining 20 22 41 0 40 and 20 22 41 0 82 in a small number of targeted attacks. This is in August. These attacks they wrote installed the chopper web shell to facilitate hands on keyboard access, which the attackers use to perform active directory reconnaissance and data exfiltration.
Leo Laporte / Steve Gibson (00:53:07):
So apparently nothing to worry about. It's like what in August they said Microsoft observed these attacks in fewer than 10 organizations globally. MS T I C assesses with medium confidence that the single activity group is likely to be a state sponsored organization. Then they said Microsoft researchers were investigating these attacks to determine if there was a new exploitation vector in exchange involved. Okay, make that yes. When they said the zero day initiative, ZDI disclosed CVE 20 22 41 0 40 and 20 22 0 1, 41 0 82 to Microsoft Security Response Center RC in September of 2022. So gee, look at that. Exchange server is being attacked. What's for lunch?
Leo Laporte / Steve Gibson (00:54:19):
Unbelievable. They were investigating while attacks were underway, 10 organizations they had identified and now we're what we don't know when in August. So somewhere between one and a half and two and a half months downstream of this of them seeing that exchange server is being exploited by a remote execution exploit, which is taking companies over and allowing bad guys to perform reconnaissance on enterprises active directory servers and Microsoft is updating their advice after this became public every day, removing extraneous spaces from their scripts. Not impressive in spin. Right News I have finished all of the redesign and spin right is working as far as I know. But that knowledge doesn't yet go very far. So now I start the final work of inducing known data errors and watching spin, right? Perform its sector by sector data recovery. That's what I'll be working on tonight. And subsequently until I've demonstrated to myself that spin right is in fact ready.
Leo Laporte / Steve Gibson (00:55:44):
That's interesting that point. How do you make data errors happen? It turns out in older drives and I've got, I have a two terabytes, I have three actually two terabytes, Seagate and a bunch of older Mac stores. You had the ability, there was a command called Read Long where you told the drive don't bother with error correction, just give me the raw data. It's called a long read because it's the data plus the error correction code which is tagged on at the end. And the ability that facility is one of the ways that spin right is able to perform data recovery even on sectors that the drive says are not good. Well, even though they're not good, there's still something there. Spin right is able to say, give me what you've got and let me worry about it. And that's where this the the dynamic statistics comes in.
Leo Laporte / Steve Gibson (00:56:46):
So do go to a known bad sector and then ask, do a long read or no because there's the compliment command, right? Long where I'm able to screw it up. Yes, exactly. I'm able to induce varying length bit errors and cause the drive to do what it's going to do when it encounters it for the first time. And so that allows me to deliberately poison sectors in various ways and then as if that hadn't happened, have spin, right? Come along and watch what it does in order to recover the data. So it's very cool. Unfortunately it's been, those things have been removed from newer drives, but I've got plenty of older drives where it's still feasible and even a two terabyte drive. So interest, I've got lots of ability to do that. That's really interesting. I didn't know that. Yeah, it's really neat. Okay, so once I know that it is doing what I wanted to do, I'll release that to GRCs News group gang and we'll find I'm sure the various things that I've missed.
Leo Laporte / Steve Gibson (00:57:55):
Cosmetic things, logging things, who knows what. I'll get those fixed and then we'll move the spin right from alpha to beta when we're there. Anyone who owns spin right will be able to download the DOS executable that I've been developing in which everyone's been testing since I won't yet have it packaged as a turnkey Windows app. You'll need to use GRCs a knit disc or read speed or arrange to boot your own dos however you want to. And then you'll be able to run that DOS executable and it be the real spin, right? Six one just as it's finally gonna be something else happened last week that was interesting. Although we won't get to high speed native USB support for spin right until somewhere in version seven. I'm thinking 7.1 only because I don't wanna delay 7.0 which will be the first spin right ever to be butable over U efi.
Leo Laporte / Steve Gibson (00:59:02):
I wanna get that out as quickly as possible and there's no reason to hold it because 7.1 will be free for everybody anyway. So I designed spin right six one. Today's a forthcoming spin right to work with any size USB drive through the mother board's bio as it always has. But now with no size limitations if the motherboard supports it and many do, but it occurred to me that I had never explicitly asked any of our testers to try attaching a huge drive larger than 2.2 terabytes, which is the largest drive that's addressable with 32 bits. You gotta have more than 32 bits to go beyond 2.2 terabytes. That's why the old style master boot record the nbr that only has 32 bit size fields in its definition, which is why you can't use an NBR on a drive greater than 2.2 terabytes. Anyway, I had never asked them to try putting, to attach a huge external drive to a USB port to confirm where their spin rights sees the large drive and can indeed work with it.
Leo Laporte / Steve Gibson (01:00:18):
That is today the spin, right? Six one we're gonna be getting and it turns out we learned that it does and it can in the show notes for any prospective spin, right? Six one owners, I've got some screenshots which our testers which two of our testers provided and I'm looking at them and thank you Leo, for them being on screen now highlighted at the bottom of a list of different drives on this one person system we see a 4.0 terabyte drive, which will be interfaced through the bios. You notice the first five drives are a hci. So that spin rights, direct hardware access to the A HCI chip itself, which it now knows how to talk to. But then the lower four drives have been connected to USB ports through the bios. So we have a four terabyte drive and spin right through the bios.
Leo Laporte / Steve Gibson (01:01:15):
We'll be able to scan that drive in 30.1 hours. Then in the next slide he's run the benchmark, the full benchmark on that drive, which allows it to perform a finer grained performance analysis. And so spin rights estimation was revised to 29.45 hours and we can see the various speeds at which spin can talk to that for terabyte drive. So while 30 hours is not fast it used to be 30 months for a drive this size. So it's a lot faster. We're doing way better, way better than we used to. And in fact on the next screen on page is somebody else who provided a snapshot they show a three terabyte drive that spin, right? Estimates it will scan in 10.1 hours. So that's way faster. So the lesson there is it is a function of the bios. Both bios allow spin, right to see a drive larger than 2.2 terabytes in one case, four terabytes in the other three terabytes.
Leo Laporte / Steve Gibson (01:02:43):
But this second one can do it a three terabyte drive in 10 hours, which is a lot faster than a four terabyte drive in 30 hours. So your speed will vary. And in fact we do see on that second that second slide, he had a one terabyte drive attached through a hci. So it was a SATA drive where we see it doing one terabyte in 30 minutes. And that exactly corresponds to my estimate, remember that I expected that. My newer estimation was that we would spin would probably be able to do two terabytes per hour and that's what we're seeing consistently two terabytes per hour or in this case here it is showing one terabyte in half an hour. So spin right six one will finally be easy and practical to use. Again on today's very large drives. And even before we get to seven, spin seven and 7.1 where we've got hardware support for usb, that's where we'll be able to run USB three at the same speed as sat. Cuz it is as fast that at that point external dries will be able to run as fast as internal drives. Anyway, I'm having a ball. Yeah, that's a huge improvement and it was a disadvantage using spin drive. Spin ride on a giant drive as it would take forever. Oh yeah. It was a practical, It just not, is not, I mean that's a day and a half. Totally doable. Totally. Yeah. And you could certainly run it over the weekend if you had to. Yeah, yeah, yeah.
Leo Laporte / Steve Gibson (01:04:24):
Yep. We're getting there. Yay. Okay, now I want to take a moment to talk about a beautiful little affordable $120 plus shipping single board computer that I, I'm starting to use as a Sunday LA last Sunday, which I'll be using for spin rights development going forward. It's called Zima Board Z I M A B O A R D. And in many ways it's the perfect little platform for spin, right? I'll get to that in a second. To get spin right to the point where it is today, which is its ability to talk directly to any and all PC hardware owned by every single one of our hundreds of spin right development testers. And I should note we currently have 367 registered testers in GRCs GitLab instance. So that's the population of people who have been testing spin right? So far I have been gladly purchasing innumerable old motherboards and drives from eBay.
Leo Laporte / Steve Gibson (01:05:30):
This has been going on for the last year when I've been unable to duplicate some obscure problem that any of our hundreds of testers were experiencing out in the field. Buying what they had was often the only way to get to the bottom of some really bizarre behavior. So that's what I would do. But that's all now behind us at least until spin right starts being used by its entire owner base I do fully expect that I will encounter of some new mysteries and I will deal with those as they come along. But that's the nature of bypassing the bios. Now that we're talking to the hardware, there's obscure hardware out there, but boy I've seen a lot of it. I think it's clear that we've reached the 99.999% point, so it's time for the next stage. What I wanted going forward was a completely silent testing platform and this little Zima board looks perfect for that.
Leo Laporte / Steve Gibson (01:06:29):
No more incessant wearing fan noise while I'm trying to focus. The Zima board is fan with a custom heat sink, fin design and just the right number of ports and expandability. It started out on Kickstarter where it was 4905% overfunded. In other words, more's a market more than 49. Yes, more than 49 times the number of project backers that they were hoping for people went nuts over it and it's now a going commercial concern through the years. The recurring question that we've been asked over and over is what GRC would recommend as a perfect PC platform for running spin, right On a drive in lieu. In lieu of dedicating someone's main machine, a desktop to that tech. Yeah, and I found a few desktops, the ones I own, which won't work at all with spin. Right? So their U E F I guess and you.
Leo Laporte / Steve Gibson (01:07:36):
Yes. And it won't be until seven that were able to run there. So this is an answer to the question I've been meaning to ask you. This is great if you were gonna run spin right and you know, do it enough, it's worth spending 119 bucks to get a little machine. Do it. Yes. And many people also have inventories of drives, drives that they've taken out of service and so this allows you to run spin right at absolute full on speed without tying up any of your other resources. As you said, for $119. Do you put Windows on it or you just run free to us on it? So I will get there. Okay. So years ago when I was writing the tech talk column for Info World Magazine, I stumbled upon a wonderful motherboard, the ultimate keyboard, an rll controller and MFM drives that worked perfectly under rll and coding.
Leo Laporte / Steve Gibson (01:08:35):
So I conceived of something I called Steve's Dream machine. It was a hit with my columns readers a PC supplier, Northgate computer Systems, took up the idea of purchasing and bundling all the components and offering them as Steve's dream machine. What I think I found here with is Zima board is Steve's Dream SBC single board computer. It is 100% Intel chip set with the exception of its dual gig network adapter, which is a real tech 81 68 chip. Now it turns out that's perfect for my development needs since I have DOS network drivers for that chip. It has a pair of six gigabit sata, three connectors with a cable to provide power for one drive. But you can, for $4 you can get a dual power cable. It has a pair of USB 3.0 ports, so spin right will be able to run drives attached to either SATA or USB three.
Leo Laporte / Steve Gibson (01:09:41):
And it has a single P C I E times four connector for the expansion of anything else. That could be A P C I E to IDE adapter if spin right needed to repair any older IDE drives or an N VME adapter if spin right needed to be run on N VME drives once they are supported and they will be under version seven. It has built in video through a mini display port, which can do 4K video at 60 hertz and critically the Zima board offers both U E F I and traditional bio support. It has a very comfortable award bios with all the bells and whistles, drive boot order and so forth. Everything that old Doss hands are hoping to see. So that spin right will be able to boot free dos and run without trouble. It could boot from an attached USB thumb drive and I've done that.
Leo Laporte / Steve Gibson (01:10:42):
If you wanted to leave the Debian derived Casa Os Linux that shipped with the board in place or Free Dos and spin right could be installed onto the boards built in 16 gig M M C Drive. That's what I'll be doing either way, I'll be able to use the same platform for spin right's future development under EF U, under U e I. So it's perfect for, for both now and for what's next, there are three Zema board models which vary in speed and size, but the smallest of the three is what I purchased cuz it's enough for doing stuff with dos. I have two of them now, one for each of my locations. As I mentioned, the smallest of the three contains a 16 gig E M M C drive, which is preloaded with a Debian Linux variant, which they call Casa Os. The board is broadly compatible, able to run any Intel os, Linux, Windows, pf Sense open W R T NAS software and anything else.
Leo Laporte / Steve Gibson (01:11:52):
And they sort of have it targeted at your own cloud or multi drive NAES and so forth. If you go to zima board.com, if you click on the order now button on the homepage and then again on the page that comes up, you'll get to the place where you set the quantity and the model number you want. If you scroll down that third page to the bottom, you'll find a buy one get one free offer. Oh that, Explain that, explain. Well it, it's not another free ZMA board, but it's a free power adapter. They say buy ZMA board and get a free 12 volt free power adapter. Oh, need that, right? Yeah. Which you need that anyway and that saves you 12 or $15 or something. So that's what I would recommend. There's a 10% off discount coupon available, but you probably can't use both.
Leo Laporte / Steve Gibson (01:12:45):
As I mentioned, the Zima board comes with cabling to supply power to a single SAT drive, but there's an optional dual sat power cabling for $4. Actually it's $3 and 90 cents that you may want if you intend to power two set drives from the sbc. And that's also what I'm doing. So anyway, I now have a terrific answer to the often asked question, What does GRC recommend for running spin, Right? Standalone. I don't think you can do better than that. Just a nice, and I mean I've been using it, it's just beautiful. You, you'll need a mini display board cable to a display port mon monitor and then the way they have it, the way they suggest you set it up is you plug it into your router and then you use a browser to talk to it. So I guess it boots up with a, it boots up this Debbie and Linux variant with a web server running and waiting to be connected and then brings up some sort of a ui.
Leo Laporte / Steve Gibson (01:13:47):
I didn't do any of that. I just blew it off and used F disk to zero the partition and made a bootable dos cuz that's what I'll be using. But there is much more for anybody who's interested. So it's just a beautiful solution for spin. Right? And other things that I thought our listeners would find interesting. And Leo, I'm gonna, I'm outta breath so let's take our last break then we'll do closing the loop and we'll talk about source randomization and a mistake that the Linux colonel made. Okay. Took my breath away with that thing. That's so really cool. I can see why that's, You can't get a raspberry pie right now. So if you get any single board thing for your projects, this looks like a great choice.
Leo Laporte / Steve Gibson (01:14:33):
Let us talk about our fine sponsor bit warden. We know, you know <laugh> should be using a password manager, right? Yes you should. The question is, which one should you use? There's lots of choices out there. I will tell you why I use Bit Warden and happily and love it and maybe even why your business should use Bit Warden. Okay I love it because it's open source. I think that's really kind of table stakes for a password manager. You gotta be able to look at the source code. Not everybody's Steve Gibson who can go to Joe ris to say, Show me what you're up to if you've got an open source project, even if you can't examine the source code that others are. So that's really important. It's cross platform. Gotta be Windows, Mac, Linux, iOS, Android works with everything you've got. It can be used at home but it also can be used at work.
Leo Laporte / Steve Gibson (01:15:30):
They have an enterprise plan and of course it could be used on your phone on the go and is trusted by millions. I think Bit Warden is the only one that satisfies all of these criteria With Bit Warden. You can securely store credentials. And by the way, not just credentials, not just passwords. I put serial numbers in there, social security numbers, images of my driver's license and my passport. Anything that I want to keep at all times on my device, but I don't want to be available to any Tom Dicker Harry, that's when I put it in bid bit Warden October is cyber security awareness month. I think we've mentioned that before. Bit Warden would like to remind everyone that I, in the interest of protecting yourself and the internet, you should use strong passwords. Ideally passwords so strong, so random that you could never remember them in a million years.
Leo Laporte / Steve Gibson (01:16:25):
Bit Warden generates those for you. Random, absolutely lengthy. As long as you want passwords that are completely random. Combination of numbers, upper and lowercase letters punctuation, of course you can, I hate to say it, there's still some sites to say, well you'll be more than eight characters and you can narrow it down if you need to, but use the max you can on any site. It also is important and I think we all agree to enable multifactor authentication on everything that will let it. I still get calls every week from somebody who's Facebook or Instagram or Twitter has been hacked. I said, why aren't you using two factor and most importantly use it on Bill Wharton, right? Use two factor preferably not SMS messaging but an authentic time based one time password system like Google's Authenticator or Microsoft Authenticator. So that or offy so that you know, you've gotta doubly locked down so you gotta keep your software up to date.
Leo Laporte / Steve Gibson (01:17:27):
We talk about that all the time. You wanna make sure you have trained your staff and your brain to recognize fishing attempts. Every one of us, however, no matter how sophisticated from time to time goes, Oh yeah, I'll click oh hold on. That's okay as long as you do that. Oh hold on <laugh>. Cause if you click it then you're in trouble. Weaker stolen passwords are actually the majority of successful hacking attempts. So use strong, unique passwords for every account that protects you, that protects your business. And Bit Warden will do this all for you. It will not fill, we were talking last week about how a password manager will save you from fishing attacks cause it will not auto fill on sites that aren't look the same but aren't the same. Enabling two step logins on Bit Ward improves the security of your password vault with options like verification through email or an authenticator app available for all accounts or as I do and I have it right here on my, I have it hanging around my neck.
Leo Laporte / Steve Gibson (01:18:28):
I use a Fido two or a UBI key. This is a UBI key and by the way, premium subscriptions use this. This is what I use for Bit Warden, it's one of the reasons I pay $10 a year <laugh> one because I wanna support Bit Warden but two because I want to use my UBI key so you know, can't get into my bit Warden Vault without this UBI key and it's hanging around my neck. So good luck. Premium subscribers also can have Bit Warden generate T OTP authentication codes for your account, adding strength to your passwords so you can also do that right within Bit Warden, Bit warden Support security for all with full featured free accounts, free for everyone every time, everywhere forever. That's really important. They're never gonna pull back on that. I asked them because another very well known password manager backed off on its free accounts and it really peeved people.
Leo Laporte / Steve Gibson (01:19:24):
I said, are you gonna ever could that They said no, no because we're open source. That's our business model free. We couldn't stop it if we wanted to, people would just fork it and go on. So we Free is important to bit warden's business model because they wanna get you into the bit warden ecosystem. Cause I'll tell you why your business can use Bit Warden and it always starts with that free personal account. Let's say I wanted to add Bit Warden to my office. I say everybody get your free bit warden account. Okay now you've got your personal account. Now join the organization account. So you get the best of both worlds. You get the personal password protection completely separate but you get your business password protection. And by the way, Bit Warden for a business is so great. You've get Bit Warden Send, which is a fully encrypted method of transmit sensitive information, whether text or files, how many times do people email stuff like tax records?
Leo Laporte / Steve Gibson (01:20:17):
It should not be emailed. It will generate unique and secure passwords for every site. Enterprise grade security, GDPR compliant, ccpa, HIPAA two compliant. They recently added even more enterprise capability by adding skim support that's good for provisioning and managing your users. So let me talk about the enterprise plans. There's a teams organization option that's just $3 a month per user. Bigger company you wouldn't wanna use the enterprise option, the enterprise organization plan $5 a month per user. These added ability to share securely share data with coworkers across departments. The entire company here's the contract and it's secure, it's private, it's protected. Individuals of course that basic free account, use it forever. Unlimited number of passwords across every platform worth upgrading the premium count less than a buck a month. I just do it to support also if you want your whole family to use it, $3 33 cents a month, that's all it costs.
Leo Laporte / Steve Gibson (01:21:14):
You gets up to six users. All the premium features. Look, I know if you listen to Secure now you're using a password manager if you're not. Or more importantly, if family and friends are not pleased, tell them about Bit Warden, the only open source cross platform password manager that you can use at home on the go at work that's trusted by millions of individuals, teams, and organizations worldwide. It's free forever for the basic account. If you want to try the teams or enterprise plan, they have a free trial, just go to bit warden.com/i love it. It works great. Works better than anything else I've ever used. I've used 'em all by the way, I have accounts with almost every password manager including the open source and the free ones and all that stuff. And this is the one I always come back to cuz it just works great everywhere.
Leo Laporte / Steve Gibson (01:22:03):
Bit warden.com/twit I trust bit worn, they're the best. Bit warden.com/twi free forever for individuals. Although kind of a kind of $10 a year cuz it's just nice to support 'em doing good work. And I didn't even mention the new thing where you can have the IT gen, auto generator username and they work with fast mail by the way, as well as some other providers to generate a unique email account that is just for that particular account. Another great way to do security. All right, back to you Steve. I want to hear all about address, random address access. Yes. Got some feedback to share first. Oh okay. Yeah, one of our listeners Zendo, Deb said something that I thought was brilliant. He said at SG GRC re captured discussion from security now 8 91, that was last week. Yeah. He said, I've wondered if using Firefox makes it worse since Firefox is now stove piping cookies, especially third party cookies.
Leo Laporte / Steve Gibson (01:23:14):
So when you show up at a new site, Google can't find a cookie. Oh that is brilliant. Brilliant. That's going on. Exactly. Yeah, exactly. There's no question. That's why we Firefox users are saying, Hey, why am I having to click on chickens constantly or fuzzy bears or whatever it is. Yeah, it is a consequence of the fact that Google is highly rate ranking the presence of their own cookie as one of the signals that they're using. And when you go to a site that you haven't been to before, there's no Google cookie there thanks to the per site stove piping that Firefox is now doing. So very, very clever observation. Thank you Sendo. Robin r said Hi Steve with all these buffer overflow and use after free issues, I've seen talk of getting development to switch to rust. My question to you is what kind of concerns or defensive techniques do you do when developing an assembly?
Leo Laporte / Steve Gibson (01:24:17):
Is it the fact that you are so low level, you are forced to be aware of everything and thus don't fall into the same traps? Additionally, would you change anything with a piece of software that you knew would be always on and be available on the internet? And I thought about this for a while. So first of all, I do have a piece of software which is always on and available on the internet. And that's server. It is laced with a lot of my project code that shields up itself. Probably the most complex asynchronous thing I've written, which is always online is the dns, The DNS cash ability or spoof ability test. That thing has all kinds of synchronous queries off to individual servers as it discovers them. Lots of things happening dynamically. I have the same problems that anybody writing in C would have, which is to do that.
Leo Laporte / Steve Gibson (01:25:23):
I create a length list of tasks and each of the objects in that are pointed to in the link list is a structure which I allocate in ram, which contains the details of where that task is and what's going on. That those have dynamically created lists of queer, of outstanding queries and their responses. I don't know how many there will be. So that's a list. So it's an extremely dynamic construction and it's been running for many, many years and it's never had a bug or crashed. So I think the advantage I have is I'm first of all one developer, so I don't have a problem explaining anything to myself. And while there's a lot going on, it's still not nearly as complicated as what has happened to today's browsers, which are just like, I don't know if there's any one person who's single mind is able to encompass, to encompass the entire thing.
Leo Laporte / Steve Gibson (01:26:35):
And the same is certainly true for operating systems. So I at a low level, I met essentially at the level that C operates cuz all the things I've just described is exactly how I would code something. Were I coding and C, there's not that big a difference I think. So you do an assembler, you doing effectively your own Malik your allocating memory. You have to remember, and I'm doing reference and I'm doing my own reference counting. So you gotta know when you can throw, you do your own garbage collection. In other words you don't get. And the off by one problem probably is a little bit less of a problem for you cuz you're so intimately connected with what's going on. I think some of the problems that come from high level languages is they're so in, programmers are so insulated from what's going on that they can make, it's easy for them to make a mistake.
Leo Laporte / Steve Gibson (01:27:29):
Well, and we talked for example about Microsoft's decision to use Electron as their platform for implementing teams. The problem is that that's JavaScript, HTML and css. You don't have to be a power coder in order for something to look like it's working in JavaScript. And so I exactly as you say Leo, I think that does tend to admit less capable or less rigorous programmers. The lower level the language, the more careful you need to be or it's very obvious that yeah, you see what something's gonna Yeah. Yes. And I think also the reason they're talking about Rust is Rust is it is garbage collected but it's very type constrained. It's a static type system and it really tries very hard to keep you from making mistakes. Every time we see languages like that, like ada I think programmers appreciate it but also don't like to use it.
Leo Laporte / Steve Gibson (01:28:30):
Yeah, exactly. I mean yeah, they're like nanny languages. Yeah. It's like, okay, well yeah that's a language, but boy I don't wanna code in that. That's fun. Rust impressive. And I guess what it's replacing, which is mostly C and to some degree c plus plus is bad enough. So I guess <laugh> people who use Russ like it and I played with it a little bit, it's very impressive, but there's a lot of boiler played a lot of extra code. It's like Java a little bit in that respect that somebody like you and to some degree me, I don't wanna spend all that time typing in all that crap. I wanna, And I think what's gonna happen is we'll get to the point where coders will not be given a choice. That is what we see happening is that we're getting to the point where we've got all the processing power we need.
Leo Laporte / Steve Gibson (01:29:23):
It used to be be that we didn't have enough RAM and we didn't have enough speed to support the overhead. Yeah, okay. Yeah, right, exactly. To support the overhead of sophisticated languages that do a lot to protect the way they're operating today. We do. And I think at some point there will be a browser that bites the bullet and says we're coding everything in Rust, right? Because we we're done with use after free errors period. And we don't care if you don't like it. Remember Rust was written by Mozilla. I mean it comes from Mozilla. There's a reason, right? It is very much for that. And by the way, once you can compile it, rust is extra. One of the reasons people like Rust is' the systems level language. It can be as fast as CNC plus plus. So once you can pile it, it's very, And think of the upside Leo, if you get paid by the line for code <laugh>.
Leo Laporte / Steve Gibson (01:30:25):
Russ is, I'm thrilled that Russ is now in the latest colonel. That is a good thing for everybody who uses Linux. I completely agree. I think that's neat. The issue is really libraries and support and a lot of that's being handled now. So that's good. So I've got one for you here from Ben Hutton. He says, Steve, we often hear breaches could have been avoided through the implementation of a systematic software patching and update strategy for enterprises. There are many solutions while performing tech support for a relative today I found IO bit updater. He says IO bit being a name I had previously trusted for the better part of a decade was showing adverts for commercial products in the same, I know in the same space as notifications for software updates. Finding this unacceptable. I looked for an alternative solution, I found one and expected to pay, but the customer, I'm sorry, the consumer slash home edition was free.
Leo Laporte / Steve Gibson (01:31:23):
And it seems like there are no limitations to speak of. Is there a solution you would suggest for Windows users for installing updates free or otherwise? The solution I found looked suspicious but had attained leader in Gartner's magic quadrant for patch management summer 2022. The solution I found is Patch my pc. Huh? He says only tried it today. So not an endorsement but seems to do the job. And so Leo, my particular approach is just to rely on individual apps to tell me when they need to be updated and then I update them like Notepad plus is my God, would the guy just leave it alone? Please? Cuz it keeps wanting to update itself. But normally apps today take care of that. And it looks like what Ben's talking about is some sort of an over watcher who rifles through your system, looks at all the apps you've got installed, checks their versions, checks to see whether that's the latest and then gets involved in telling you that you need updates.
Leo Laporte / Steve Gibson (01:32:37):
I just kind of thought maybe from your tech guy stuff on the weekends, not I've heard of one. The good news is Microsoft finally is acknowledging the need for this and has a package manager, believe it or not, called Get which how package managers on Linux will manage updates for everything on your system, including system updates, right? That's the idea of Winge. It's new relatively, so I'm not sure how complete it is. So it would be things through the Microsoft store probably. Actually that's an interesting question. Now the store does its own updates automatically. I think win Get is is it goes beyond that. You do get it from the Microsoft store. I, I'll have to ask Paul about that, but I think my sense is Winge is a full or intended to be a full package manager for Windows. So how would it know about, in the case of our Unixes and Limits, we have you installed a repository because you installed through the package manager, right?
Leo Laporte / Steve Gibson (01:33:40):
So the package manager, as you install stuff, makes a database of installed stuff and then when you do an app get update or whatever, it will look at that database, see what's been installed, check for new versions. It does that in the repositories. Exactly. So you would need some sort of Microsoft maintained database of application versions and then you could download. So yeah, I mean I think that's probably why it doesn't yet do everything, but it does create these manifests. It has sources, source repositories. So I'm hopeful, but I'll have to take a look. I haven't looked at Patch my pc. I think it's an unfortunate name, but doesn't mean it doesn't work Well. It looks like it's for Microsoft's own endpoint manager. So it sounds like, And then most of these guys I'm looking at, the engineers are at Microsoft MVPs and so forth.
Leo Laporte / Steve Gibson (01:34:41):
So it says it looks similar to Winge to be honest with you. 710 supported products. I mean, when you're looking at Debbie and you're looking at apps, that's more than 10,000 packages. Yes. Apps knows about, I mean this is remarkable ecosystem on the Linux side. I'd love to see Windows get to that point. Yeah. Okay. J jt, Red Hill, he said a quick question you or Leo mentioned in a side comment a couple episodes back that you block Origin can block this damn gdpr Cookie popup Popups <laugh>. He said, good, I've tried. Hey, hit him. Oh, hit him. She says, I've tried clicking on the block all popups button. He says, I use Chrome by the way, but that doesn't do it. Can you please tell me how you do this? Or if another alternative that you know you know of, I thought I showed this when the show, but maybe I showed it afterwards.
Leo Laporte / Steve Gibson (01:35:35):
You wanna go to you block Origins, filter lists and then go down and expand annoyances. So there's a whole, and it's hidden. There's a whole bunch of filters underneath Annoyances. I check you block filters, annoyances and Fanboy. Annoyances and fanboy incorporates the easy list cookie list. And while it's not a hundred percent, it's 90% at least of all those cookie popups, the cookie cookie. Oh nice. Yeah, I didn't know that either. Yeah. So I'm glad we asked it. It's a nice thing. Told us, as you know out of the box you block Origin does everything you'd want it to do, but it can do a whole lot more if you go into the filter list. They support a massive number of filter lists. I don't think you need to add them all, but that's a couple. You might wanna wanna good old Gore Hill. Amazing.
Leo Laporte / Steve Gibson (01:36:27):
I can imagine. I see him with a long beard, hot exactly. Somewhere up in the Pacific, Northeast, northwest and off <laugh>. Get outta my case. He's probably nothing like that, but is that, That's what I think of. Yeah, he's like a Devo curmudgeon I think. Yeah. So Joel Clearmont, he said, just listen to SN eight or eight 90 about Google Analytics in the EU and thought you might be interested to learn about Fathom Analytics. It's used fathom.com, U S E F A T H O m.com. They're designed from the ground up around privacy and designed their infrastructure to comply with gdpr, including an option to have your data never leave the eu. I love this. I wanted to use this. He says, I have switched all my sites over to it a year ago and love it. And then I have a link to his blog which is really good and I recommend it to our listeners titled Why I Switched to Fandom Analytics.
Leo Laporte / Steve Gibson (01:37:37):
It turns out it does more. No wait, it does a better job with less of the random cruft that analytics. He said that analytics had all kinds of crap that he didn't need, but what this one does, it does better than Google Analytics was, what was doing in his opinion. So we have something that will give our sites analytics without and be privacy respecting of our users. I will try to convince our team to use it. We still use ga ga, I'm sorry to say have him take a look at it. Yeah. Yep. So Blaine Tramel said, Have you talked about the safety of public wifi? But that article only talked about browser traffic. So if you are only using a web browser, then yes, most likely safe. But if you are using apps that communicate unencrypted for their work and apps on mobile devices might be making non TLS requests.
Leo Laporte / Steve Gibson (01:38:37):
So I would say still not safe without a vpn. He says, have to remember someone in China could hack the wifi router in San Francisco and capture the traffic. You do not need to travel and be local. So anyway, I thought that was worth noting that he, He's absolutely right. I was thinking entirely of brow of everything being done through the browser with the fact that the world has switched to https. But it certainly is the case that you could have an app. I mean, I hope you wouldn't, but you could have an app that just says, Ah, nobody's probably looking and does its thing, whatever it might be in the clear. So anyway, blame. Thank you. That is certainly a good point Bob. Karen said, Hi Steve in re two SN 8 91 last week as an IT consultant. And I guess he says, I am an IT consultant and I never use public wifi.
Leo Laporte / Steve Gibson (01:39:30):
Not so much from fear of hacking from someone else on the same wifi, but from the provider of the wifi itself. An IT person who runs it could set up a proxy or man in the middle much easier and scrape all data through it. I always tell my clients, turn the hotspot on your phone on and use that for your laptop if needed. I feel there's much less chance of Verizon trying to steal my traffic than some local coffee shop IT guy or even a big airport. Unlimited data is very common now on cell plans. Anyway, thanks for the great show for all these years, Bob. So anyway, I just wanted to share that idea. I often use my iPhones hotspot when I'm somewhere that I don't have wifi and I want to have access and what I promise will be the last CPE comment.
Leo Laporte / Steve Gibson (01:40:31):
But I liked it cuz there was a little more information. David Lameer said, I'll trouble at SG GRC with one more C S S P CPE comment. When I was way behind on CPEs from my first year of certification, I found a blog post on the ISC website that specifically listed your podcast among a NUM number that could count for free CPEs, he said, really saved my behind. So I just wanted to mention that it's not that they're allowing it formally endorsing security now as a source of ongoing education. Good. That's great. I didn't know that. That's great. Yeah, really happy to hear that. I just wanted to add thanks to the Discord. The winge repository is actually a GitHub repo and you can submit your software just as a poll request in the repository and say, Hey, I'd like you to manage my updates.
Leo Laporte / Steve Gibson (01:41:36):
Nice. I think this ultimately could be really good if the community gets behind it. It's in the Microsoft GitHub repo wind get packages and at this point that's not built into Windows that the, No, I don't think so. You have to get it, but you can get it for the Windows store. I would just love to see it just become the default way to install software or hook the Windows store. Yeah, and I was gonna say that if at some point we could application developers could depend upon that being present, then we could eliminate all of the know individual tip check for update. Yeah. Stuff so annoying. Yeah, this is so much better. Thank you for that. I appreciate it. This is why we love our yeah, Club TWI members. Appreciate it. Em. Okay, so an unintended side effect in Linux, as we know, internet protocol address addresses endpoints by IP address and at an IP address we have a 16 bit port number which identifies specific services operated at that IP address.
Leo Laporte / Steve Gibson (01:42:45):
So an end to end connection will have an IP address and port on one end like the source IP in source port, and an IP address in port. On the other end, the destination IP in port at the receiving end where a client is connecting to a web service or to a service like web, email or whatever. The port as we know is typically well known, 4 43 25, 1 10, whatever. And on the client's connection initiating end, it has long been the case that when a client asks its operating system for a new outbound connection, the OSS T C P I P network stack simply moves linearly upward, starting above the reserved service port range at port 10 25, sometimes 10 24, and incrementing and incrementing numbers until some upper limit, perhaps all the way up to 6 5 5 3 5 is wrapped before wrapping around. So traditionally, the way to all T C P I P network stacks worked when client applications asked to initiate a new outbound connection, the stack would simply initiate the next free port in line.
Leo Laporte / Steve Gibson (01:44:17):
And you often see sequential numbered ports in blocks, like if you do a net stat command on your system, they're not just scattered randomly in a linear list. But 11 years ago, back in 2011, having the OS allocating client connection ports, which is to say the source ports linearly, was seen as a potential problem since it made the next ports to be used guessable by an adversary. And that guess ability might allow adversaries to hijack connections by just assuming what they were gonna be assuming what the clients, the IP and source port would be. That's the only way you designate an endpoint. So if a bad guy injected traffic sent traffic toward the destination, there's no way to differentiate it from the traffic coming from the legitimate source sequence numbers comes into play there also for TCP connections, but we've already talked about all that in the past, so we know that this is all possible since it was precisely the lack of source port randomization that alarmed Dan Kaminski about the spoof ability of DNS servers.
Leo Laporte / Steve Gibson (01:45:45):
Internet wide attackers could blindly spoof replies by guessing the linearly allocated source ports of outstanding DNS queries. So in response to this perceived threat, RFC 6 0 5 6 was published by the I E TF titled, Recommendations for Transport Protocol Port Randomization and it's abstract, the abstract of the RFC reads. During the past few years, awareness has been raised about a number of blind attacks that can be performed against transmission control protocol tcp, and similar protocols. The consequences of these attacks range from throughput reduction to broken connections or data corruption. These attacks rely on the attacker's ability to guess or know the five TU protocol, source, address, destination, address, source port, destination port that identifies the transport protocol instance to be attacked. This document describes a number of simple and efficient methods for the selection of the client port number such as the possibility of an attacker guessing the exact value or I'm sorry, such that the possibility of an attacker guessing the exact value is reduced.
Leo Laporte / Steve Gibson (01:47:15):
While this is not a replacement for cryptographic methods for protecting the transport protocol instance, the affor mentioned port selection algorithms provide improved security with very little effort and without any key management overhead. The algorithms described in this document, there are five of them are local policies that may be incrementally deployed and do not violate the specifications of any of the transport protocols that may benefit from them, such as tcp, udp, udp, light stream control transmission protocol, datagram congestion control protocol and RTP is they say, provided that RTP application explicitly signals the RTP and R TCP port numbers. Who? So that's what they said, <laugh>. So the idea was the RFCs LEO there if nothing, if not thorough. So a great thing to read if you're getting a little sleep deprived. Yes, absolutely. Oh, that's how I learned all this stuff in the early days was literally sat down.
Leo Laporte / Steve Gibson (01:48:19):
Okay, RFC one, the rfc. Oh god. So the idea was since the source port chosen by the OS doesn't matter at all, there is no reason not to be a lot more clever when choosing the next one. RFC 6 0 5 6 presents five different algorithms for doing just that. And it states that the so-called double hash port selection algorithm offers the best trade off. Consequently, it was recently adopted with minor modifications in the Linux kernel, starting with kernel version 5.12, RC one, and this prompted a trio of industrious researchers at the Hebrew University of Jerusalem to take a look at Linux result. What they found was not good. Their paper titled Device tracking via Linux new TCP source port selection algorithm will be presented during the 32nd use Nick's security symposium, which is upcoming, but I have the paper now. They explain in their abstract, which is all that's worth sharing here because as we'll see what happened.
Leo Laporte / Steve Gibson (01:49:45):
They said, we describe a tracking technique for Linux devices exploiting a new TCP source port generation mechanism recently introduced to the Linux kernel. This mechanism is based on an algorithm standardized in RFC 6 0 5 6 for boosting security by better randomizing port selection. Our technique detects collisions in a hash function used in the said algorithm based on sampling TCP source ports generated in an attacker prescribed manner. These hash collisions depends solely on a per device key and thus the set of collisions forms a device ID that allows tracking devices across browsers, browser privacy modes, containers, and I P V four V six networks, including some VPNs. They said it can distinguish among devices with identical hardware, software, and lasts until the device restarts. We implemented this technique and then tested it using tracking servers in two different locations and with Linux devices on various networks. We also tested it on an Android device that we patched to introduce the new port selection algorithm.
Leo Laporte / Steve Gibson (01:51:13):
And by the way, Android was going to adopt it, but changed his mind when this happened. The tracking technique works in real life conditions and we report detailed findings about it, including its dwell time, scalability, and success rate in different network types. And finally, we worked with the Linux kernel team to mitigate the exploit resulting in a security patch introduced in May of 2022 to the Linux kernel and we provide recommendations for better securing the port selection algorithm in the paper. So the principle that I wanted to highlight and that we keep seeing playing out over and over is that things that once seemed to be secure enough, mostly because we weren't trying as hard as possible, are no longer considered to be. So the mess with modern processor, micro architectures, specter and meltdown, and the rest is a perfect example. For quite some time we were all happily living with the way our processors worked and with all of the performance those optimizations delivered, but that all ended overnight when some very clever academic researchers started looking much more closely.
Leo Laporte / Steve Gibson (01:52:39):
Another example is dram, same story there. Everything seemed fine until researchers began wondering whether too many bits may have been squeezed into two smaller space and whether that might create some adjacent row interference. And sure enough, we know what the consequence of that was. Similarly, the issue of IP source port assignment was happily ignored. Then Dan Kaminski realized that it could be a disaster for dns. So operating systems moved to change to ephemeral key based, pseudo random assignment. And then these clever researchers said, Ah, not so fast, and discovered that there's a unique per machine pattern that could be used for tracking. Wow. I wonder what will be next. Stay tuned to this podcast to find out. Never underestimate the ingenuity and perseverance of a hacker. That's just the rule there. Amazing. Yeah, that mean that is the case. And so all these things, we lived with them for years, sometimes decades, and then someone said Don't so bad, not so fast. I love it. I love it, Mr. Gibson. You're a gem, a jewel. And if I could say it in assembler code, I would. But I'm sending you a book and an old Relic <laugh>, an old relic. I'm sending you two books. I told you about one, I'm sending you another. I just thought of, Oh, that's entirely an X 86 assembler. I hope you enjoy it. <laugh>.
Leo Laporte / Steve Gibson (01:54:19):
No pros. No pros. I don't know if you've ever seen this book. It's a title is Exchange Ra XX <laugh>, and I think that's all you need to know. The author is X or PD and <laugh>. I just thought I'd send it to you cuz it's kind of silly. Cool. Yeah, everybody should have an assembly language written book on their shelf, just an assembler. I bet you. I'm actually really curious if you can look at it and you go, Oh yeah, I know what that does. Oh yeah, yeah. Oh, that's cute. Oh. Oh, what a laugh. I bet you, I bet you'll laugh reading this. We'll see. Sounds great. Yeah, no kidding. Exactly my kind of puzzle. You should show this to Laurie <laugh>. <laugh>. Anyway, Steve is the best. We are so glad we have him every Tuesday right here talking about security and technology in the most lucid way possible.
Leo Laporte / Steve Gibson (01:55:19):
He even makes RFCs sea entertaining <laugh>. You'll find us here at 11 a, I'm sorry, 1:30 PM Pacific right after Mac break. Weekly, 1:30 PM Pacific, four 30 Eastern, 2030 utc. If you follow Steve on Twitter, SG grc, two reasons to do that. The show notes go there right before the show so that you can download them and read them along. He also has 'em on his website, but you can also message him there. His dms are open if you've got thoughts or comments, that's where a lot of the feedback on the show comes from. grc.com, the website to go to Gibson Research Corporation, not only for spin, right? And as you can see this is probably a good time to get spin, right? If you buy 6.0 right now you'll get 6.1, which is imminent. Perhaps even participate in the testing. You could be the one that says, Steve, I found a flaw.
Leo Laporte / Steve Gibson (01:56:12):
Get a gold star on your forehead for the help him to help him out here. grc.com. While you're there, of course you can get a copy of the show. Steve has two unique versions, a 16 Kilobit audio version, which sounds a little bit like a Thomas Edison cylinder, but has the one benefit small for the bandwidth impaired. We also have transcripts written from that 16 Kilobit Edison Cylinder by Elaine Ferris. She gives us beautiful transcripts that you can read along as you listen or use them to search for parts of the show. All of that's at grc.com, along with a 64 Kilobit audio version, the full quality audio version, grc.com plus check out all the other stuff he does if you wanna try his DNS caching utility and think about all the stuff going on behind the scenes in his server. Was the server written assembler?
Leo Laporte / Steve Gibson (01:57:03):
No, that's in C So at iis it's Microsoft's iis. Yeah. But it has a really nifty add-on facility called IS apy which is IIS api. Yeah. And so it's a huge is I've written huge is APY extension, which is the shields up and the certificate testing and all of the stuff that GRC site does. And all of the eCommerce I wrote in Assembler also. Wow. So did you write glue code and C or c plus plus and then everything else can be an assembler or no whole thing? The whole assembler. Yeah. It turns out that the calling convention for the API is you all have to do is set up the stack and just jump to a call. So nice. It all works directly. Yep. It's a nice feeling when you are, It's almost like you're looking into the machine and seeing it work and you get it, you understand it.
Leo Laporte / Steve Gibson (01:57:59):
It's pretty cool. I just like it. Yeah, I think that's why coders code is that at any level you get a sense of satisfaction. But that's why I think that's assembly language. Coders pursue this. What seems a seemingly arcane art because you are writing in the computer's native tongue, you're exchanging RA with ra. You're doing it at the very base level of it, which is cool. Although it's also why I doubt I'll ever use, I'll ever code arm at a in assembler cuz it just doesn't seem friendly. It's mean. The risk reduced Intruction set computer as opposed to sys complex instruction set computer. I like sys. Well, you've learned all the instruction codes, right? Yeah. You got 'em up here. Yeah. And probably you can do in one instruction what risk requires five for I would guess. I would guess that's what it is, right?
Leo Laporte / Steve Gibson (01:58:58):
Is that, Yes. Well for example, I, I'm able to add two locations in memory with a single instruction, whereas risk, you have to load it and register load. The other one are register, add the two together and then store the result back out. Yeah, that's careful. Yeah. Yeah, I can get it. Yeah. Yeah. Store architecture grc.com. We have copies of the show at our website. In fact, if you go to TWI tv slash sn, you'll see every show ever recorded all 892 of them one after the other. There. You can also go to a YouTube. There's a Security Now YouTube feed that has all the shows that we've done in video anyway there, which is not all of them. And probably the best way to do this, if you don't wanna get all the old shows, the feed only has the most recent 10 shows.
Leo Laporte / Steve Gibson (01:59:47):
If you wanna get all the old shows, you gotta go to the website. But if you just want to get the new show when it comes out, subscribe in your favorite podcast client, set it to auto download and you're just gonna get it. And that way you can listen whenever you say, Oh, I got a minute or two, let me listen to some security now. Which I think a lot of people do. But if you wanna listen on Tuesday, listen live, that's fine too. The live, do TWI do TV is the live stream, irc.twi.tv to discuss it or of course in our discord because a lot of Club TWI members in there is. Well, thank you Steve. Great job. I appreciate it. Thank you my friend. See you next time. See you back here on the 18th. Wow.
Jason Howell (02:00:28):
I'm Jason Howell. What do you get your favorite geek who already has everything? Well, I know just the thing. It's a club quit gift subscription. Of course. Quit podcast. Keep them informed and entertained with the most relevant tech news and podcasts available. An b d with the Club TWI subscription, they get even more. They get access to all of our podcast ad free, The members only Discord, exclusive outtakes behind the scenes and special content and exclusive shows like Hands on Mac, hands on Windows, and the Untitled Linux Show. You can purchase your geeks gift at twit.tv/club and they're gonna thank you every day for it
... (02:01:05):
Security Now.