Security Now Episode 919 Transcript
Please be advised this transcript is AI-generated and may not be word for word. Time codes refer to the approximate times in the ad-supported version of the show.
Jason Howell / Steve Gibson (00:00:00):
It's time for security now with Steve Gibson. I'm Jason Howell filling in for Leo LaPorte one last time. I promise you he's gonna be back next week, but we have a lot of fun talking about security news this week. Google's free assured open source software service. Steve talks all about that Microsoft Patch Tuesday kind of feels like past Tuesday in perpetuity and in reality, that's probably exactly what it is. We check in on a European psychotherapy clinic that failed to provide minimal security for their patients records and the consequences attached to doing so. And Steve Gibson takes a closer look at the forced entry exploit for iPhones. It's really fascinating. That's next on Security Now.
... (00:00:45):
Podcasts you love. From people you trust. This is is TWiT.
Jason Howell / Steve Gibson (00:00:55):
This is Security now with Steve Gibson. Episode 919, recorded Tuesday, April 18th, 2023, forced entry. This episode of Security Now is brought to you by Cisco Meraki. With employees working in different locations, providing a unified work experience seems as easy as herding cats. How do you reign in so many moving parts? Well, the Meraki Cloud Managed Network. Learn how your organization can make hybrid work work. Visit meraki.cisco.com/twit and by BitWarden, get the password manager that offers a robust and cost-effective solution to drastically increase your chances of staying safe online. Get started with a free trial of a teams or enterprise plan, or get started for free across all devices as an individual userbitwarden.com/twit. And by ACI learning aci. Learning amplifies expertise across industries that command higher pay ACI learning, transforming how companies train and technology professionals learn to fuel the modern workforce for premium training in audit it and cybersecurity readiness.
(00:02:07):
Visit go.acilearning.com/twit. It's time for security now with Steve Gibson. And Leo is still not here. I'm Jason Howell sitting in for Leo. But Steve, you are always the constant on this show. We appreciate that about you. <Laugh>, glad to be back with you. Jason. Glad you're here. Thank you holding down the fort at your end. And yes do what I can. Certainly, certainly glad to be back. Okay. So an interesting sh episode I think for us. This is security now, number nine, 19 for the 18th. I got the of, of April, right? I got the month right this time or whatever it was. I got wrong last time. Anyway okay, so we're gonna, as we have been, answer some questions, what happened with last week's patch Tuesday? Was there anything of note if we took a quick overview of just a tiny bit of last week's news, just sort of a, you know, a quick scan, what would that look like and what would all those stories have in common?
(00:03:18):
What new developer-centric service is Google making freely available for the good of the open source community? And I'm very bullish about this. It looks really cool. What moves is what's app making to improve the security of what is the world's most popular secure messaging system? You know, theirs, what happens when a European psychotherapy clinic apparently doesn't care enough to provide even minimal security for their patient's records? And finally, in this week's deep dive, we're going to answer the question, what could researchers have found? These are Google Project Zero researchers who, you know, they've been around the block a few times, right? You know, they've seen it all. What could they have found inside a piece of the NSO group's, Pegasus smartphone spyware that actually and truly terrified them? Oof. And why? That's intriguing. They've seen stuff. Mm, very what they found. They're like whole goodness.
(00:04:32):
What they found may surprise you as as clickbait headlines might, <laugh> might have. You're just gonna have to wait to find out. That's, that's what we know. Awesome stuff. We've got a lot to talk about this week. Before we do though, let's talk about our sponsor of this week's episode of Security Now, brought to you by Cisco Meraki, the experts in cloud-based networking for hybrid work. So, you know, are your employees working at home? Do you even know where they're working, like they're doing work for you? Are they at a cabin? Are they on the beach somewhere? Could be. And a cloud managed network provides the same exceptional work experience no matter where they are. So if they are at the beach, doesn't matter. The cloud's working for them, you know, hybrid work, it's here to stay. It works best in the cloud.
(00:05:23):
It has its perks for both employees and leaders. Workers can move fast. Yes, they can deliver better results with a cloud managed network. And leaders can actually automate distributed operations. They can build more sustainable workspaces, proactively protect the network. And there's an I B G market pulse research report that was conducted for Meraki that highlights top tier opportunities in supporting hybrid work. Hybrid work, according to the report, is a priority for 78% of C-suite executives. Leaders, of course, want to drive collaboration forward. They wanna make these these things easier for their employees to do while staying on top of or in fact, boosting productivity and security in the process. Hybrid work does have, you know, an assortment of challenges as well. The I D G report raises the red flag about security notes that 48% of leaders report cybersecurity threats as a primary obstacle to improving workforce experiences.
(00:06:24):
You know, always on security monitoring. This is part of what makes the cloud managed network so awesome. Now, it can use apps from Meraki's ecosystem of partners. These are turnkey solutions that are built to work seamlessly with the Meraki cloud platform. And you can, you know, do your asset tracking, your location, analytics and so much more. And that gives you a whole bunch of benefits. Things like gathering insights on how people use their workspaces. So when smart space environmental sensors can actually track activity and occupancy levels to stay on top of things like cleanliness, as one example you can reserve workspaces based on vacancy based on employee profiles. This, you know, we've heard this referred to as hot-desking. It allows employees to scout out a spot in a snap locations in restricted environments can be booked in advance, and that includes time-based door access as well.
(00:07:21):
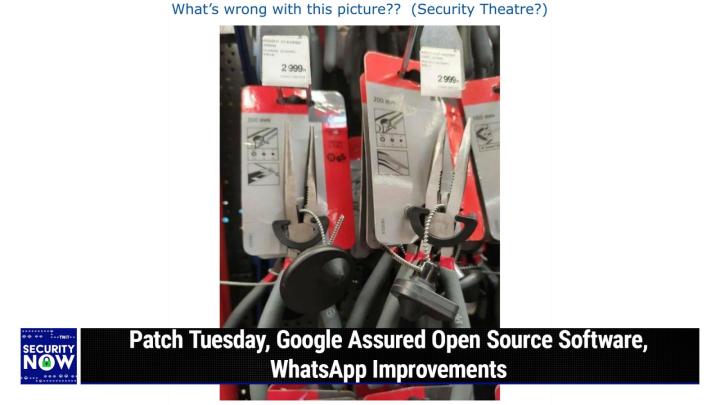
And finally, mobile device management. This is integrating devices and systems to allow it to manage, to update and troubleshoot company owned devices. Even when that device, that employee, even when they are sitting on the beach somewhere on a remote location somewhere, you can turn any space into a place of productivity and then empower your organization with the same exceptional experience no matter where they work with Meraki and the Cisco suite of technology. And you want to check it out for yourself. You can learn how your organization can make hybrid work work by visiting meraki.cisco.com/twit. That's M E R A K i meraki.cisco.com/twit. And we thank them for their support of security. Now, all right, picture of the week time. This one this one's not too difficult to decipher. You look at it for a second. You figure it out and you wondered, did that really happen?
(00:08:19):
Really? Somebody did that. At least that's, that was my ex my experience. <Laugh>, okay, so for those who don't have the advantage of video or, or the show notes we've actually had a variation on this before. There was one where bolt cutters were being held cap at a hardware store with a, you know, a like a thick gauge steel cable that that was looped through them. But again, you know it's a bolt cutter <laugh> that, that, you know, you're trying to keep from being stolen, obviously, by looping something that this thing was designed to cut through its jaws. And so we have a variation on that this week. I thank one of my Twitter followers from, from sending it here. We have some needle nose pliers with where down near the hinge of the jaw, they've got wire cutters.
(00:09:19):
And you, I mean, you could, you don't, this doesn't even take any imagination. You, you don't have to move anything. You just have to squeeze the handle on one of these because the, the, the thin metal cord essentially that is, that is looped through them, is going through the wire cutter portion of these needle nose pliers. I mean, it could be lined up perfectly, more perfectly than no, you know, literally just pull the handle all you need to. No, I mean, handle, yeah. And, and, and looking at it, you know, looking at it, even if you were not a thief and you encountered this, you'd be just tempted to squeeze the handle just to say, okay, idiots, you know, I, I'm not taking this, but you should take a lesson anyway. Wow. Yeah. I gu I guess instead of looping it. Well, no, I guess there's no real way to do that if it's got a wire cutter there, you just gotta come up with a different system.
(00:10:22):
You're in trouble. Yeah. I, I, I know that you produced the podcast ev ev every week, whether you're on camera or not. Do you were, did you see the <laugh>, the picture of the bicycle that was locked to a yellow post that like had no top, had no top. Oh, right. So you just lift the bicycle, whoop off <laugh>. I mean, I guess security in that case is like, can we slow down the majority of people who might do something? But there's al but that's like pretty low effort right there. <Laugh> or maybe an IQ test. Like, okay, you know if you can't get away with, with, you know, if you want to steal the bike, but you can't figure out how, you probably should not be riding a bicycle <laugh>, but if you can, hey, free bikes <laugh>. That's right. Yeah. Wow.
(00:11:19):
Okay. So last Tuesday was our monthly celebration of all things we know of. Hopefully all the things we know of that we wish were different in the details of our Windows software. I would like to say that to that end, we received new and improved software, but since we never appear to be getting ahead where we're basically just treading water, hoping to keep our heads above what that suggests is that we actually received last week software that is broken in new and different ways than what we had before. You know, you know, what's different is that we haven't yet discovered all of the new ways that this replacement software is broken, but we've eliminated a bunch of the ways that we knew the old software was broken. So we'll be back next month and the month after that and the month after that, add infinitum.
(00:12:27):
This will never end. You know, think about that. This shows no sign of ever ending. It's not as if the number of problems is diminishing over time. Patch counts are dropping, and there's a chance of us not needing one of those monthly rituals. No, you know, I'm not really up on pop culture. Leo typically helps me with these things, but I think that the official technical term for this monthly dance that ultimately goes nowhere is whack-a-mole. So yes, this month we reportedly cured 97 flaws in our software from Microsoft, including one actively exploited zero day flaw. There were seven flaws, which received a critical rating because they allowed for remote code execution <laugh>. However, overall, nearly half of this month's, 97 vulnerabilities allowed for remote code execution. Okay, so here's the breakdown of the 97, 45 were remote code execution vulnerabilities 20 were elevation of privileged vulnerabilities, 10, information disclosure nine, denial of service eight, security feature bypass, and six were spoofing vulnerabilities.
(00:13:50):
Okay? And as we know, the two most potent vulnerability classes are remote code, execution and elevation of privilege. So together that was 45 plus 20, they formed 65 out of the total 97 patched problems. Oh, and that count is separate from the 17 newly discovered vulnerabilities, which Microsoft fixed for us the week before in their edge browser. The zero day vulnerability is an elevation or privilege problem in the Windows common log file system driver. This tends to be a problematic component of Windows. We've, we've run across problems in it before. You know, and we hear about it too often. The problem with Windows e o p elevation or privilege bugs in core component drivers, such as the common log file driver, is that they're always there. That is the drivers are always there, and they're in the kernel. They're installed on every Windows computer.
(00:14:53):
Consequently, they allow attackers with few or no significant access privileges to promote themselves directly to the system account level, you know, root, which gives them free reign over the machine. This is why elevation of privilege, which sounds less scary than remote code execution, can be at least as troublesome and certainly as le at least as handy to attackers. One of the critically rated remote code execution bugs may be a bit extra worrisome. Microsoft disclosed a remote flaw in their Microsoft Message Q system known as MS M Q. It provides a robust means for intersystem message passing communications when absolute reliability in messaging is critical, you know, you just don't send it and hope that it got there. It's got, you know, delivery confirmation and receipts and all that stuff added to it. But since it's a bit special purpose, it's not always enabled, but when it is, it can be trouble because Microsoft gave it a 9.8 C V s S score and which was, we know it's very difficult to get.
(00:16:11):
I mean, you rare do, do you get a ten nine point eight still r way bad. And apparently from Microsoft's description they said, quote, to exploit this vulnerability, an attacker would need to send a specially crafted, malicious MS MQ packet to an MS MQ server. This could result in remote code execution on the server side. Okay? So, you know, we've been around long enough to know that's not good. That's, there's some exploitable, you know, buffer overflow ish sort of thing where just sending a packet at the server can allow it to execute your code. So not good. So let's hope that Ms MQ servers are entirely constrained as they should be within enterprise intranets, and that none are exposed on the public internet. On the other hand, you know, reality too, we now know with absolute certainty that it's not only security researchers who compare pre patched software to post patched software in order to reverse engineer the flaws that were fixed by the patch.
(00:17:31):
So, and, and thus discover the vulnerability that wasn't known until the patch was made available. So it won't be long before bad guys are working to gain entry into enterprises that A, have not yet applied the April patches to their border servers, and B, have the MS MQ service publicly exposed, where you almost kind of feel like they deserve what they're gonna get. Because this, this really should not be, you know, there's no point, there's no reason for it to be out on the internet. And as a matter of fact, another worrisome critical bug also should not be out on the internet. It's a remote code execution flaw in Microsoft's DCH P server service. As we know, dch h p is the dynamic host configuration protocol, which is the way most of the computers in the world receive their IP addresses. It's a slick system that allows a machine that knows absolutely nothing about the network it's connected to, to emit a totally generic ethernet broadcast packet out onto whatever network it's attached to, wired or wireless, that packet, which essentially says, Hey I'm here, help will be received by a listening DC D H C P server, which is then able to reply with all of the instructions and settings necessary to get that machine's IP stack configured with a unique non conflicting local IP address, the IP of the network's gateway, so it's able to talk to the rest of the world and the addresses of some d n s servers, which are available to the, the hosts on the internet or on the intranet.
(00:19:28):
Okay? So, you know, my own server network at GRC uses 100% statically configured IP addresses, because there's just no need. Nothing is coming and going. You know, people are not, you know, attaching to that network on an ad hoc basis, unlike, you know, at, at Starbucks and airports, and in our homes at home, I have a combination of static ips and D H C P, some machines I want to always have at the same location. Whereas things like iPhones, iPads, Rokus, you know, i o t thermostats and whatnot, they don't matter, and there's no point in tying them down. One of the cool things that a DHCP server can be configured for is the range of ips that it is allowed to allocate from. So, for example, in a / 24 network, like, you know, most of us have in our, our, you know, most residential users have, which typically begins with 1 92 0.1 6, 8 0, or one.
(00:20:33):
The final bite can range from two from zero to 2 54. So, you know, a residential network's dhcp DHCP server could be configured to automatically assign ips only from the upper range, like, like where the last bite runs from 100 to 2 54, which leaves, or I'm sorry, 2 53. 2 54 is typically the gateway, which leaves the lower 100 ips zero to 99 guaranteed to always be available for manual static assignment. In, in any event, d HCP server flaws have historically and understandably been a little extra frightening, because if you stop to think about it, the entire nature of the way D H C P servers operate is inherently unauthenticated by design. They're supposed to be there for anyone who asks for their help without question. This means that D H C P service must be robust enough to accept and reply to packets from unknown untrusted and potentially hostile devices.
(00:21:46):
You know, they've gotta be sturdy. Fortunately, although we've seen very serious problems in the past with DHCP servers, today's problem only rates an 8.8 out of 10 since the flaw turns out to be a post authentication problem. So different than just querying for your IP address and stuff, you know, that's still bad, but at least it's less. So, Microsoft said, quote, an authenticated attacker could leverage a specially crafted R P C call, you know, remote procedure call. So I guess that'd be our remote, remote procedure. Call, call R P c, call to the D h CCP service to exploit this vulnerability, they said, and being D H C P, it's going to be on the land, not the wan. So, exploitation of this vulnerability requires an attacker. First, have access to the local internal network, then have some form of authentication, which is recognized by the D H C P server, and then be clever enough to craft some RPC call in order to, to take it over.
(00:22:58):
So we did not have this month any serious post patch meltdowns, which we've covered in prior months. Actually, I don't think any of this year, but lots were last year. Microsoft had a tough time, especially at the beginning of last year. But none of those have been reported this month. So there's no obvious reason not to proceed, update our machines to eliminate the latest batch of known problems while apparently, given all the evidence, introduced at least as many new unknown problems, which, you know, we'll get to fixing eventually. So we'll see you next month for more of the same.
(00:23:43):
Okay. So I was the news of the past week, right? To pick out those things that I thought were most interesting and, and, and worthy of some conversation. There's a section which risky business news calls, breaches and hacks. And as I just scanned it, none of them were gripping. None of them I wanted to go into in any detail, but still, they just sort of had me shaking my head. Now, I remind myself that our listeners are, are only aware, at least through this podcast, of those things that rise to the top of the week's news, which, you know, seem worthy enough for mention you know, and some further exploration and, you know, deeper dives here, but that could have the effect of inadvertently obscuring what the broader view looks like of just how much nonsense is continually going on out there in the wider world.
(00:24:45):
So, risky businesses tagline is <laugh>. It's a jungle out there. So I wanted to share briefly what I encountered in just this one short section covering the past week's news under the topic of breaches and hacks. So I'm just gonna read the headline and the short little blurb just to give you a sense for it. So, N c r gets ransomware. Ncr, the world's largest banking and payment software maker has confirmed that a recent data center outage was caused by a ransomware attack. According to ncr, the incident was, has impacted the availability of its aloha p o s payments platform. The intrusion was claimed by the ALF v ransomware gang, which temporarily listed the company on its dark website. Also, cyber attack on irrigation systems. A cyber attack is suspected of having disrupted the operations of irrigation systems in Israel's upper Galilee region water controllers for irrigating fields in the Jordan Valley and control systems for the Galley sewage corporation.
(00:26:02):
Were were down last week during yearly cyber yearly cyber attacks aimed at Israeli targets known as Ops Israel. While several activist groups announced their participation in Ops Israel this year, the identity of the hack of the attacker remains unknown. The Jerusalem Post reported also Hyundai data breach. Hyundai's, Italian and French branches have lead customers details, exposed date includes email addresses, telephone numbers, physical addresses, and vehicle chassis numbers. MSI ransomware attack, Taiwanese hardware vendor MSI, has confirmed a security breach after the money message. Ransomware gang claimed to have breached and encrypted some of the company's systems. Hundred Finance Crypto Heist. The hundred finance platform was hacked for 7.4 million following a flash loan attack, G D A C, crypto Heist, South Korea, and cryptocurrency platform. G D A C was hacked earlier this month for 13 million worth of assets. Bit true crypto heist, the bit true cryptocurrency exchange says it was hacked and lost 23 million worth of assets following an attack on one of its hot wallets on April 14th.
(00:27:21):
Bit True says it's currently investigating the incident and doesn't know how the attack took place. Year finance, crypto heist, a threat actor exploited a bug in the yearn finance platform to steal 11.6 million worth of cryptocurrency assets. And finally, Terra Port Crypto Heist, the Terra Port Defi platform was hacked for 4 million worth of crypto assets. Okay, <laugh>, what a week? 19 years ago when Leo first proposed this podcast to me, none of this sort of nonsense was going on. You know, we had cute little email macro viruses that like to send out email to all of the contacts in someone's address book. You know, you, you'd receive a bizarre email from your mom and call her up and say mom, unless we have a Nigerian cousin that you've never told me about, I think that maybe your computer has a virus. You know, and that was pretty much the extent of it, right?
(00:28:34):
Simpler times. But thinking about that brief news blurb summary that I just shared, you know, the one thing that most of them have in common, the thread that winds and weaves through them all, is cryptocurrency. That's today's common factor. Partly it's because it enables ransoms, you know, payments which are now facilitated by the inherit anonymity offered by cryptocurrency, but even more so, it's the cryptocurrency itself. The software being used to implement cryptocurrency systems is apparently given the evidence no better than the software that does anything else. But rather than, you know, just getting the font wrong, when an item is selected in a word processor, when a hole is found in cryptocurrency software, millions of dollars of actual tradable fiat currency drained out through that hole. You know, and where there's money, there's bad guys. That's, so, that's exactly it. Where there's money, there's bad guys, <laugh>.
(00:29:43):
Yep. Yeah. Okay. So this is cool. We're in, need some of, some good news at this point. And we have some courtesy of Google. Last Wednesday the 12th, Google announced that their so-called Google assured open source software service would now be generally available to all. Here's what Google posted and explained. They said threats to the software supply chain and open source software continue to be major areas of concern for organizations creating apps and their developers. According to Mandiant's m Trends 2022 report. So from last year, 17% of all security breaches start with a supply chain attack, the initial infection vector, second only to exploits. They said, building on Google's efforts to improve open source security, we are announcing the general availability of the assured open source software, which they call assured o s s service for Java and Python. Ecosystems available today at no cost assured.
(00:31:05):
O s s gives any organization that uses open source software, the opportunity to leverage the security and experience Google applies to open source dependencies by incorporating the same open source software packages that Google secures and uses in their own developer workflows. Wow. Okay. So in other words, just to be clear, this new service will provide free use of the same vetted and carefully reviewed Java and Python packages that Google themselves use internally for their own applications. Google explained, using assured OSS, organizations can obtain their OSS packages from a trusted and known supplier, know more about their ingredients with assured software bill of materials provided in industry standard formats like S P DX and VEX reduced risk as Google is actively scanning, finding and fixing new vulnerabilities in curated packages, increased confidence in the integrity of the ingredients they're using through signed tamper evident Providence, and choose from more than 1000 of the most popular Java and Python packages, including common machine learning and AI projects like TensorFlow and Pandas.
(00:32:40):
Since our public preview announcement in May of last year, 2022, and integrating assured o s s as a key component in software delivery shield the following October, we've received an overwhelmingly positive response and interest from our customers. They then cite one John Meadows managing director at City Tech Fellow cybersecurity. As Citi said, Citi has been an advocate and active leader in the industry's efforts to secure enterprise software supply chains, both city and Google. See, untrusted and unverified open, open source dependencies as a key risk vector. This is why we've been excited to be an early adopter of Google Cloud's. New assured oss product assured OSS could be, can help reduce risk and protect opensource software components commonly used by enterprises like us. Okay? So Google said, assured O s s guards, o s s packages against attacks and risk by continuously mirroring key external ecosystems to manage end-to-end security without creating forks, managing the security and integrity of the mirrored repos and end-to-end build tool chain with tamper evident providence and attestations continuously scanning for fuzz testing and fixing critical vulnerabilities, which are then quickly contributed back upstream to limit the exposure time and blast radius.
(00:34:22):
And finally, operating a critical patching team to support covered packages. Another early adopter of this, of, of Google's is Melinda Marks a senior analyst with E S G. She was quoted saying, as organizations increasingly utilize OSS for faster development cycles, they need trusted sources of secure open source packages without proper vetting and verification or metadata to help track open source software access and usage organization's risk exposure to potential security vulnerabilities and other risks in their supply software chain. By partnering with a trusted supplier, organizations can mitigate these risks and ensure the integrity of their software supply chain to better protect their business applications. Okay, and then Google finishes. There are significant security benefits to assured o s s adopters and the larger community from the curation process. Since our assured o s s team curated the first 278 packages, we have been the first to find 48% of the new vulnerabilities.
(00:35:36):
You know, CVEs, each of these CVEs has been fixed and upstreamed. So to me, this seems like all good news. I do have the sense for like those who've have a, you know, a cross to bear, a, a, you know, an ax to grind with Google, that, you know, this might cause free software, open source purists, you know, to blow a gasket if they sense any sort of effort to, you know, in any way PR, privatize or taint the openness and freeness of open source software. But we all know too well now that public open source software registries are, are under constant and growing attack. You know, they are being polluted, wi wi with like similarly named deliberately malicious packages and people are downloading them. So while the idea of having an open community of like-minded contributors is terrific, the reality is that not everyone is like-minded.
(00:36:46):
So I, for one, think that it makes all kinds of sense to have access to a vetted and curated source of open source software. So, you know, to Google, I say Bravo. I think, you know, this is a big win. And, you know, Jason, I think our next sponsor is a big win too. I agree. That's right. I knew you would. I, I completely agree because I have the next sponsor on my phone and next sponsor on my computer. And if you need help, you know, with your passwords managing all those passwords, then I think you're gonna appreciate this. Security now is brought to you by, I know BitWarden. Bitwarden is awesome. It's the only open source cross-platform password manager that can be used at home. It can be used at work on the go. It's trusted by millions. We love it here at twit.
(00:37:41):
We're all using BitWarden these days. And you know, that includes Steve Gibson. Of course, even Steve has switched over, which is awesome with BitWarden. All of your data, all of the data in your vault is end-to-end encrypted, not just your passwords. So you can protect your data and privacy with BitWarden by yes, adding security to your passwords with strong randomly generated passwords for each account. You can go even further. You can use their username generator. You can create unique usernames for every account, or even use any of the five integrated email alias services. It's like a security toolkit <laugh> around keeping your data private and protected. I should add, bit Warden has new features to announce in their latest release. Just a couple to, to list off here. First of all, there will now be an alert when BitWarden's autofill detects a different U R I than the saved vault item, such as when an iframe is used for the login process, that's useful.
(00:38:43):
New users who create their accounts on mobile apps, on browser extensions and desktop apps can now check known data breaches for their perspective master password via H I B P. That's incredibly useful, right? The more knowledge we have about that stuff, the better protected we are logging in with a device is now available for additional clients. So login requests can also be initiated from browser extensions, from mobile apps and desktop apps. And then starting later this month, the BitWarden application will begin alerting users if their K D F iterations are lower than the recommended default of 600,000 for pbk D F two argon two IDs also an optional alternative, K D F for users seeking specialized protection and a stronger master password as we know, has a higher impact on security than K D F iterations. So you should have a long, strong, very unique master password to get the absolute best protection possible.
(00:39:46):
You can share private data securely with your coworkers across departments or the entire company with fully customizable and adaptive plans. There's BitWarden's team organization option. It's three bucks a month per user, and then of course, they have their enterprise organization plan. That's $5 a month per user. And then if you're just an individual user you can always use the basic free account. You get an unlimited number of passwords. You can upgrade any time to a premium account for less than $1 a month. That's it, $1 a month. Or you can bring the whole family on board with their family organization option to give up to six users premium features. That's only $3 and 33 cents a month, which is just, I mean, it's so, so little for the, for the protection that you get for everything that you get with BitWarden. It's awesome.
(00:40:39):
At twit, we are fans of password managers. Bit Warden is the only open source cross-platform password manager that could be used at home on the go or at work. And as I've said, it is trusted by millions of individuals, by teams and organizations worldwide. You can get started with a free trial of a teams or enterprise plan, or get started for free across all devices as an individual user at Bit warden.com/twit, you've heard us talk about BitWarden a lot on this network. That's because they are great at what they do. So you should check it out. Bit warden.com/twit. We thank bit word for their support of security now. All right, WhatsApp, <laugh>, WhatsApp, what's happening with WhatsApp? What's happening? I'm not a big social media user. <Laugh>, you as, as Leo often notes, it took him quite a while to get me into Twitter.
(00:41:39):
And he's not really even trying to move me over to Discord. He's, I think he knows that's not gonna happen. <Laugh>, I just, you know, I don't need, I can't handle one more. I understand Steve outlet that I need to be checking all the time. Totally get it. <Laugh>. okay. So, and also the fact is I'm not moving state secrets securely. And of course, I'm skeptical that it's actually possible to do so with any of our modern mainstream technologies. You know, I've al we've often joked that if you really wanna tell someone a secret, go out into the middle of a, of a football field both of you huddle under a, a, a thick blanket and whisper into each other's ear. Oh, and you have to be naked so that there's no recording devices anywhere on, on either of you. And then you have a chance of actually conveying a secret and not having it leak out anywhere.
(00:42:30):
Otherwise I don't think so anyway. You know, the only encrypted messaging service I bother with is iMessage. And it's just cause it's there. It really wouldn't matter much to me if it wasn't encrypted. You know, I have some friends who have green bubbles on my iPhone, you know, which means they're using sms and you know, those messages fly out in the clear, you know, okay. But all that aside, when the world's leading secure messaging platform, which for better or for worse is WhatsApp announces security improvements, it's something that we need to at least take note of. So last week, WhatsApp received three new security features. They called them account protect, device Verification, and automatic Security codes. And we'll look at these things one at a time. Here. So here's how WhatsApp described the first one of those. Account Protect. They said, if you need to switch your WhatsApp account to a new device, we want to double check that it's really you.
(00:43:37):
Okay, good <laugh>, they said, from now on, we may ask you on your old device to verify that you want to take this step as an extra security check. To which I thought you're not doing that already. That seems like a really good thing to do. Anyway, they said this feature can help alert you to an unauthorized attempt to move your account to another device. As I said, that one seems kind of obvious. You know, we often see that when we're changing an email account, a notification is sent to both the old and the new accounts to help prevent a malicious email change. This is the same sort of thing, and sort of similarly, when a new trust relationship is being established, both ends are typically asked to affirm that they both wish to trust the other. So this so-called account protect feature is, you know, obviously useful, but you have to wonder why it's only happening now.
(00:44:41):
You know, and we know, right, that anything that is done to increase security will have some degree of backlash. Some, some trouble. You know, people have moved their WhatsApp account from device to device in the past, and the old device never asked if they wanted to lose access to it in favor of another one. Now it's going to. So, okay, that'll cause some confusion, but it does, sure does seem like it's worth the add, the additional security of not, you know, suddenly d de discovering that the WhatsApp has moved to a different device that you did not authorize. Okay? Net up n Next up we have what WhatsApp is calling device verification. Describing this. They write mobile device Malware is one of the biggest threats to people's privacy and security today because it can take advantage of your phone without your permission and use your WhatsApp to send unwanted messages to help prevent this.
(00:45:51):
We've added checks to help authenticate your account with no action needed from you and better protect you if your device is compromised. This lets you continue using WhatsApp uninterrupted, okay? So I'd add the doula more digging into that one. This device verification is some backend technology designed to prevent malware, which crawls into a user's phone from obtaining the user's authentication token, and then impersonating them in subsequent secure messages. Okay? Now, having said that, that's not actually what it does but exactly what's going on here isn't yet clear. So here's how WhatsApp describes the situation. They said WhatsApp uses several cryptographic keys to ensure that communications across the app are end-to-end encrypted. One of these is the authentication key, which allows a WhatsApp client to connect to the WhatsApp server to reestablish a trusted connection. This authentication key allows people to use WhatsApp without having to enter a password pin, s m s code or other credential every time they turn on the app.
(00:47:19):
This mechanism is secure because the authentication key cannot be intercepted by any third party, including WhatsApp. If a device is infected with malware, however, the authentication key can be stolen, okay? So that's the point is that's different than using it locally on the app and like sending out messages through the, the client's WhatsApp app. This is obtaining the AU authentication key and exfiltrating it. So they said, we are primarily concerned about the popularity of unofficial WhatsApp clients that contain malware designed for this purpose. These unofficial apps put users security at risk, and it is why we encourage everyone using WhatsApp to use the official WhatsApp app. Once malware is present on user devices, attackers could use the malware to capture the authentication key and then use it to impersonate the victim to send scams phishing attempts, et cetera, to other potential victims. Device verification as they're calling this will help WhatsApp identify these scenarios and protect the user's account without interruption.
(00:48:43):
Okay? Now, I'll just note before we go any further that WhatsApp in writing this is being optimistic, if not disingenuous, since Sirius spy malware, such as we will be looking at closely in our final topic today. Is purpose designed to do this with the official WhatsApp app? So, you know, they say, oh yeah, it's only the third party apps that that are, that are like, you know, third party WhatsApp apps that are a problem. Eh, you know, the, clearly the vast majority of WhatsApp users are using the WhatsApp app, and that's what the spyware is targeting, okay? In any event, the problem is certainly real. So here's how they're solving it. They wrote, WhatsApp has built device verification to benefit from how people typically read and react to messages sent to their device. When someone receives a message, their WhatsApp client wakes up and retrieves the offline message from WhatsApp's server.
(00:49:55):
This process cannot be impersonated by malware. That's cannot, cannot be impersonated by malware that steals the authentication key and attempts to send messages from outside the user's device. Okay? That's not quite true, but will, when we understand what they're doing, we'll be able to sort of dissect this. They wrote device verification introduces three new parameters, a security token that's stored on the user's device. A nonce that is used to identify if a client is connecting to retrieve a message from WhatsApp server and an authentication challenge that is used to asynchronously ping the user's device. They said these three parameters help prevent malware from stealing the authentication key. Again, that's not what it does, but okay, and connecting to WhatsApp server from outside the user's device. And every time someone retrieves an offline message, the security token is updated to allow seamless reconnection attempts in the future.
(00:51:04):
This process is called bootstrapping the security token. Okay? And giving it a fancy name doesn't make it <laugh> fancy. Every time a WhatsApp client connects to the WhatsApp server, we require the client to send us the security token that's on their device. This allows us to detect suspicious connections from malware that's trying to connect to the WhatsApp server from outside the user's device. An authentication challenge is an invisible ping from the WhatsApp server to a user's device. We only send these challenges on suspicious connections. There are three possible responses to the challenge success. The client responds to the challenge from the connecting device failure. The client responds to the challenge from a different device. This means the connection being challenged is very likely from an attacker, and the connection will be blocked or finally no response. The client doesn't respond to the challenge. This situation is rare and indicates that the connection being challenged is suspicious.
(00:52:16):
We retry sending the challenge a few more times. If the client still doesn't respond, the connection will be blocked. Okay? And then they finish by adding device verification has been rolled out to 100% of WhatsApp users on Android and is in the process of being rolled out to iOS users. It enables us to increase our user's security without interrupting their service or adding an additional step they need to take. Device verification will serve as an important and additional tool at what's app's disposal to address rare key theft security challenges. We will continue to evaluate new security features to protect the privacy of our users. Okay? Okay. So here's what's actually going on. What they've described when you sort through and weed out the mumbo jumbo is a simple but certainly useful protocol for detecting when two physically separate are both checking in for messages. The idea is that every WhatsApp client will now be maintaining some state, a transient state in the form of this new token, which they've received from the WhatsApp server.
(00:53:43):
You know, it's probably just a random nonce. That's all it needs to be. That was the, it was the random nouns that was most recently received from the WhatsApp server when the client last connected. This nouns will be changed by the server and sent every time a WhatsApp client connects to transact messages, and at the start of each new connection, which after all the clients initiate, the client will return the last nouns it received to the server. Okay? Clearly, if only one client is ever doing this for a given account, the server will always receive the knots that it had previously sent to the client for that account. But if a user's WhatsApp identity authentication has been stolen and is being used by a physically separate client, then two clients will both be returning NAS and only one of them will have the NAS that was most recently sent to that user's account by the server.
(00:55:01):
As soon as the client, that doesn't mo that, I'm sorry, as soon as the client that didn't most recently connect to the WhatsApp server does. So it will provide an obsolete nonce to the server, and the server will know that something's not right. So, yeah, it's a clean and simple solution to this cloned client problem. Again, not that big a deal and certainly a good thing to do. Again, one wonders why this wasn't already in there, but it's good that it is now. And lastly, this third feature they call automatic security codes. They describe it this way. They said, our most security conscious users have always been able to take advantage of our security code verification feature, which helps ensure your chatting with the intended recipient. You can check this manually by going to the encryption tab under a contacts info. To make this process easier and more accessible for everyone, we're rolling out a security feature based on a process called Key Transparency that allows you to automatically verify that you have a secure connection.
(00:56:28):
What it means for you is that when you click on the encryption tab, you'll be able to verify right away that your personal conversation is secured. Okay? Now, once again, in this kind of this touchy-feely boiler plate overview, they don't really explain what's going on and they gloss over some of the like important stuff I read all the way through WhatsApp's description of this thing that what they're calling automatic security codes. And you can thank me later for not dragging you through it. What it amounts to is a public auditable, appended only meaning, you know, nothing can ever be deleted. Immutable is an the other fun phrase for that immutable log of the use of WhatsApp user account public keys. Now, the WhatsApp app already allows users to display, share and verify their public keys with either a QR code or by verifying a 66 0 digit number, you know, which, which is each endpoint's public key.
(00:57:56):
But doing that requires that both parties arrange to interact in real time, preferably face-to-face with their phones to exchange QR codes. And as we know, this was a feature that three a, the secure messaging app has used since its inception. You in three A, you had like a little stoplight. You had green, yellow, and red or I guess I better put it be red, yellow, and green, where green is the highest level of verification, which is only obtainable if you, if each phone gets shown to its, it, the, the phone that you're peering with, and they're able to exchange the, their i their identities, like literally face-to-face. Okay? So what WhatsApp is now creating under the name key transparency is a, is a global public directory of user accounts and their matching public keys, which will allow one-sided verification of the public keys of, of a user's contacts on WhatsApp.
(00:59:12):
So, you know, and, and, and that's the key and that's certainly useful. The, the point is that I, in the, in the encryption tab on WhatsApp for one of your WhatsApp contacts, you, you, you could, if you clicked it, you got a QR code or a 60 digit number for you that contacts public key. So you're seeing that, but in order to verify it, so all, all you know is you've got a public key, right? You don't know that it's actually theirs. In order to verify it, you both need to be available in real time. So where the, the where your contact is able to read out their public key and you verify that it matches the key that you believe is their public key. So thus, a double-sided verification requirement. What, what WhatsApp has done now is they're creating a global automation accessible immutable append only you know, reference for all of the public keys of all of the WhatsApp users.
(01:00:26):
So the user's experience is that now they will be able to press a button to verify the public key of any of their contacts. The, the, the, the contact gets looked up in this public key directory, the so-called key key transparency directory, and it's verified with the phone on a one-sided verification, not needing the other side. So it's another nice feature improvement, you know, in a way that makes sense and, you know, good, I'm glad they have it again, you know, WhatsApp is the number one global leader in secure messaging by far and away they are in the lead thanks to, you know, Facebook's prevalence. So it, it needs to be easy to use and it needs to be as secure as possible. Okay? the last thing I wanted to share before we get into the the thing that terrified Google's Project Zero folks is a follow up to a previous story.
(01:01:31):
Remember back near the beginning of February of this year, it was episode 9 0 9. Leo and I talked about a particularly astonishing and horrifying data breach, which had occurred at a psychotherapy clinic in Europe. Here's how I described it then. I said, the news was that French authorities have detained a 25 year old Finnish national whose accused of hacking the vest Vesto psychotherapy center for reasons, for reasons. We'll see, I said, this hack of vesto is considered to be one of the worst in the country's history. Okay? Now, it occurred back in 2018 and 2019, so I guess this kid was what, 20 years old then when he allegedly stole the personal medical records of the clinic's patients and attempted to extort the clinic to put pressure on the company. The hacker leaked extremely sensitive client files on the dark web. When that failed, he sent emails with ransom demands to more than 30,000 of the clinic's patients asking them each for 200 Euros and threatening to publish their medical records if they did not pay up.
(01:02:57):
To which Leo replied, oh boy, <laugh> and I continued saying, ah-huh <affirmative> Finn authorities formerly identified the hacker in October last year when they issued a European arrest warrant for his arrest, and they detained him last week. Okay? So I, and I said, okay, so this is brazen and bad, right? The hacker obtained extremely sensitive personal medical information and shows to use it to extort both the clinic and its past patients, all 30,000 of them. And it was that number of files and patient histories that raised my eyebrows. I said, 30,000, okay? No matter how large and busy this clinic might be, they cannot be currently treating 30,000 patients. And in fact, you know, there are 260 working days a year, five times 52. So if the clinic averaged 10 new patients per day, which seems like a high side number, 30,000 patient records would be 11 and a half years worth of patient files at the rate of 10 per day, okay?
(01:04:01):
So that was in early February. We have an update for one thing. The Finish Psychotherapy Clinic is now bankrupt. What a surprise. That's what'll happen when apparently the entire past hyper confidential history of your clients is publicly exposed to the internet. Who's gonna make an appointment after that? So the clinic has gone. What's a bit more interesting is that the ex c e o of the clinic also faced criminal charges. And it's difficult to feel sorry for him since, as we know, mistakes can happen, right by mistake. But policies do not happen by mistake. You know, they happen by policy. So someone needed to be held accountable for this clinic's online preservation of the past records of 30,000 patients, which, you know, as I said back in February, if you, if you really have to keep it for like HIPAA equivalent regulations, but take it offline, don't leave it on, you know, exposable accessible to the internet where it was, th this, it turns out that, that this, this kid, this 25 year old didn't hack into their network.
(01:05:32):
He used a password in order to access the database over the internet. So that's just unconscionable. Okay? In the process of digging around within the facts of this data breach, it came to light that in addition to failing to take this sort of data security, you know, like, like any sort of data security precautions that any medical patient would reasonably assume were in place and that the law would both expect and require to have in place, the clinic's c e o knew about his company's SL sloppy cybersecurity for up to two years before the black male, which took place in 2020. It turns out that th those earlier attacks that I mentioned in 2018 and 2019 were separate events that were previously known. They happened under this guy's watch. The clinic suffered several da previous data breaches, as I said, in 2018 and 2019, and never reported them presumably hoping that no traceable cyber crime would arise as a result, and thus the company would never be held to account.
(01:06:58):
Of course, the final breach was what in the security industry we call a doozy. So there was no sweeping that one under the rug. When you send email to 30,000 previous clients asking them for 200 euros each or their, their, their, their private psychotherapy records will be made public. That's not good. Okay? Moreover, current breach disclosure and data protection regulations such as our favorite GDPR in Europe make it very clear that data breaches can no longer simply be ignored with the hope that no one will find out. No, they must be promptly disclosed for the greater good of all. So the final news from Finland is that our arguably criminally negligent c e o was in fact found by the courts to be criminally negligent and has been convicted and given apri a prison sentence. And one wonders whether he'll have the cell next to the young hacker who stole his data.
(01:08:10):
The hope is that this will serve to remind other business leaders that merely promising to look after other people's personal data is not good enough. You actually have to at least be able to demonstrate that you tried to do so, and that clearly did not happen in this case. And the fact that after multiple breaches, no improvements were made in, in the clinic's security posture, nothing was done to to, to, to fix those previous problems. So yeah, it's good as we know that people are beginning to be held accountable because nothing will change otherwise. Okay, Jason, one last mention of, of why we're here and then we're gonna look at forced entry. The thing that the Project Zero guys at Google discovered that really did keep them awake at night, that may surprise you.dot, I'm terrifying. Keep going that because apparently it works for for Click Babe.
(01:09:15):
Yes, very interested to hear what you got in store for us there, but let's take a minute right now and thank the sponsor of this episode of Security Now that is ACI learning for the last decade. Our partners at IT Pro, you've seen 'em on the network, right? They brought you engaging and entertaining IT training to level up your career, your organization. Well, now IT PRO is part of ACI learning, and with IT Pro ACI learning is expanding its reach and its production capabilities, offering you the learning content you need at any stage in your development. Now, one of the most widely recognized beginner certifications is the compt A plus certification and compa courses with IT pro from ACI learning make it easy to go from daydreaming about that career and it that step that you want to make to actually launching it.
(01:10:11):
Earning certificates opens doors for most entry level. IT positions, supplies, potential promotions if you happen to already be in the field. That's a wonderful thing right there. Tech is one industry where opportunities outpace growth, especially when you're talking about cybersecurity. The demand for talent remains strong as tech continues to be a field that requires expertise and commands higher pay. About one third of information security jobs require a cybersecurity certification. That's compared to 23% of all IT jobs. While organizations, you know, they're hungry for cybersecurity talent, the cyber skills gap grows with every day. The average salary for cybersecurity specialists is $116,000. Well, ACI learnings, information security analyst and cybersecurity specialist programs can actually get you certified, get you in the door. ACI learning offers multiple cybersecurity training programs that can help you to enter or advance within this wonderful industry, right? C I S S P certified Ethical Hacker Certified Network Defender cybersecurity Audit School and Cybersecurity frameworks.
(01:11:26):
They all offer the most popular cybersecurity certifications. Now, how you learn actually matters a lot, and ACI Learning offers fully customizable training for all types of learners. So whether you prefer in person, on demand or remote, you can take your learning beyond the classroom for teams of two to 1000. You get volume discounts that start at five seats, and you can ask about a free two week trial for training for your team as well. Now just right around the corner here, a today as at the time of this recording, it's April 18th on April 24th through April 27th, IT Pro wants to connect to you connect with you at rsa, the products you know and love it. Pro Audit, pro and Practice Labs are now training the modern workforce together as ACI Learning. And you can visit Booth 24 29 at rsa to check 'em out for yourself.
(01:12:26):
ACI Learning Transforming how companies Train and Technology Professionals learn to fuel the Modern Workforce for premium training and audit it and cybersecurity readiness. You just have to go to go dot ACI learning.com/twit. That's go dot ACI learning.com/twit and make sure when you do that, you use our special code that's TWIT 30 and you'll get 30% off a standard or premium individual IT Pro membership. We can't thank ACI learning enough for sponsoring this episode of security now for sponsoring the studio that I'm in right now. They really are awesome. So check it out for yourself. Go dot ACI learning.com/twi, use code TWIT 30. All right. We've done a lot of really big setup for this main event here. I'm super curious to know what <laugh>, what they've found, cuz it doesn't sound good. It's not good <laugh>. Okay, so but that's way interesting.
(01:13:29):
So that's of course the criteria for making the podcast. Yeah, my original title for today's podcast was King's Paw. Now that's capital P, not capital S, not King Spawn King's Pawn. That's the name that's been given to a powerful piece of spyware being offered by one of those Israeli spyware purveyors other than the n o group, who as we know offer now their two well known for comfort Pegasus spyware to various governments. But while doing the background legwork for that story, I ran across the fascinating technical of another earlier piece of spyware that was used by both this second group who we will be talking about soon. And by NSO Group with Pegasus, I knew our listeners would be with, would find the technical details of this. Very interesting. So I decided to push our discussion of King's Pawn to next week, unless something even more juicy comes up, but we'll get to it today.
(01:14:37):
I wanna take us through what Google's Project Zero team discovered about their so-called forced entry exploit that has been successfully deployed by several malware vendors to gain entry into Apple iPhones Citizen lab, which is at the Monk School of Global Affairs and Public Policy at the University of Toronto and Canada. Provided Google's Project Zero team with a sample of the forced entry exploit and Apple Security Engineering and Architecture Group collaborated with Google in working through exactly how it was possible for a gif thumbnail image to take over any iPhone despite all of apple's, many layers of protection, which work to make that impossible. So what we had here with forced entry was the holy grail of exploits providing attackers with remote code execution via a zero click iMessage Citizen lab somehow arranged to capture an NSO group generated iMessage based zero click exploit while it was being used to target a Saudi activist at the time that Project Zero wrote about this, they said, quote, based on our research and findings, we assess this to be one of the most technically sophisticated exploits we have ever seen.
(01:16:20):
Further demonstrating that the capabilities N S O provides rival those previously thought to be accessible only to a handful of nation states unquote. And of course, what makes this so disturbing is that this is for sale so that it's not only a handful of nation states that now have access to this sort of technology, any qualified government and some unqualified governments unfortunately, can now purchase this advanced targeting malware. Okay, so here's how Project Zero described. Just for reference, the NSO group they wrote, NSO Group is one of the highest profile providers of access as a service selling packaged hacking solutions, which enable nation state actors without a homegrown offensive cyber capability to pay to play vastly expanding the number of nations with such cyber capabilities. For years, they wrote groups like Citizen Lab and Amnesty International have been tracking the use of NSOs mobile spyware package.
(01:17:37):
Pegasus, despite NSOs claims that they quote, evaluate the potential for adverse human rights impacts arising from the misuse of NSOs products. Pegasus has been linked to the hacking of the New York Times journalists, Ben Hubbard, by the Saudi Regime Hacking of Human Rights defenders in Morocco and Bahrain, the targeting of Amnesty International staff and dozens of other cases the United States has added NSO to the entity list to severely restrict the ability of US companies to do business with nso. And stating in a press release that quote, NSOs tools enabled foreign governments to conduct transnational repression, which is the practice of authoritarian governments targeting dissidents, journalists and activists outside of their sovereign borders to silence dissent when they finished Citizen Lab was able to recover these Pegasus exploits from an iPhone. And therefore this analysis covers NSOs capabilities against iPhone. We are aware that NSO sells similar zero click capabilities, which target Android devices.
(01:19:03):
Project Zero does not have samples of these exploits, but if you do, please reach out <laugh>. Okay, so in previous cases, analyzed targets were sent links in s you know, like links in SMS messages. And while as we know, these sorts of phishing style attacks are often successful, individuals at the highest risk levels who are probably more technically savvy or have received training about like where not to click are less LA or less apt to click on something that you know, does it really look absolutely 100% legitimate and, you know, pass a very stringent smell test. So although a one click exploit might work, the holy grail is the exploit that requires zero action on the part of the target. The exploit just works silently in the background. You know, short of not using a device, there really is no way to prevent exploitation by a zero click exploit.
(01:20:23):
It's a weapon against which there is no defense since the initial entry point for Pegasus on iPhone using this attack. That is, this forced entry attack is iMessage. This means that a victim can be targeted just using their phone number or their Apple ID username, which is typically not difficult to find or obtain for high profile individuals. Okay. iMessage offers native support for GIF images, which can be directly sent and received in iMessage chats. They show up in the chat windows chat log timeline as Leo and his Discord denizens are all too aware. GIF images can also be animated by causing the GIF to contain a series of frames which are displayed in succession creating animation. Apple wanted to make those gifs, which don't naturally loop, loop endlessly, rather than play through only once, so very early in the incoming iMessage parsing and processing pipeline after a message has been received.
(01:21:52):
But well before the message is displayed, iMessage calls a method in the IM trans coder agent process to which it passes any image file it receives with the extension dot G I S F. The method called is named I M G I F utils with copy from path and to destination path parameters as suggested by the selector's name. The intention was presumably to just copy the GIF file before editing the loop count field to make the GIF repeat endlessly. The method uses the core graphics APIs to render the source image to a new GIF file at the destination path. And although the source file name does need to end in GI F, that doesn't mean it's actually a GIF file. So apparently we're gonna learn this lesson all over again, or at least a variation of it. Apple's image IO library is used to determine the actual format of the source file, ignoring the file extension, and then parse it completely and deliberately ignoring the file extension.
(01:23:28):
This was actually done to prevent type, you know, file type confusion attacks, which we've seen in the past. But in this instance, the protection backfired, thanks to the use of this fake GIF trick, over 20 different image processing codex are now suddenly part of the iMessage zero click attack surface. Unfortunately, this includes some very obscure and complex formats. As a consequence of this unintentional chain of dependencies, hundreds of thousands of lines of code are now remotely exposed. Remember, last week's podcast a chained a dangerous interpretation. That was just one example of how difficult it can be to get complex codex. Exactly right. Okay. So what codec do you imagine the NSO group chose to invoke with their fake gif in an iMessage attack? Would you believe A P D F? Yes, believe it or not, the unintended chain of dependencies in iMessages processing of incoming GIF images allowed external, remote, malicious parties to send anyone A P D F, which the receiving I, but it's a PDF with a GIF extension, right, which the receiving iPhone would then attempt to parse and display for how many years, for how many years were we as an industry dealing with malicious PDFs?
(01:25:24):
Yeah. Wow. You know, this is a lesson learned. Oh, so my God thought <laugh>. Yes, exactly. What wouldn't you think? So as we know, PDFs were one of the more popular exploitation targets due to the file format's, ubiquity, and the complexity of its wait for it, its interpreter. And on top of the difficulty of rendering a document image from a typesetting specification, which is what PDFs are, PDFs later required the ability to interpret JavaScript, which is where we all in tone in unison, what could, could possibly go wrong, <laugh>. Okay. Fortunately, Apple's core graphics PDF parser does not appear to interpret JavaScript. So we can be thankful for that. But those evil geniuses and as you'll, as you'll soon see, I'm not using the term genius casually. I rarely use the term the evil geniuses at the N S O group found something sufficiently powerful lying inside the choreo graphics.
(01:26:34):
P d F parser turning the clock way back to the late 1990s. We can all remember a time when bandwidth and storage were much more scarce commodities than they are today. And when it made much more sense to actually code an assembly language, I'm just saying but back then a compression standard known as J big two J B I G numeral two was created. J big two had a very narrow and very specific purpose, but it was very good at it. It was an image Kodak designed to highly compressed monochrome images where pixels were only black and white, and where there was an extremely high degree of redundancy of what was being compressed, it was developed to achieve extremely high compression ratios for scans specifically of text documents and was implemented and used in high-end office scanner and printer devices. If you were to use the direct scan to pdf f feature of such a machine, a PDF file would be produced, which was mostly just a thin p f wrapper around a JBI two compression stream.
(01:28:20):
As it happens, the PDFs produced by those scanners were exceptionally small, often being on the order of only a few K bytes. Okay, you might ask, how's this possible? There were two novel techniques which J big two used to achieve its extreme compression ratios, which are relevant to the exploitation we're talking about here. The first technique was known as segmentation and substitution. Okay? Segmentation as in looking at the individual black blobs on the page, meaning the text characters and substitution as in let's not compress all of them. Let's just compress one of them and then point to the others. If you think about it, a text document contains a bunch of text, and in a language such as English having a relatively small alphabet, the same character like s t and E will appear all over the page. Believe it or not, J Big two actually segments documents to be compressed into their individual glyphs and uses a simple pattern recognition matching to match and collect all of the glyphs that look almost the same.
(01:29:49):
Then rather than storing all of those near duplicate glyphs, j Big two pretends that they are all the same and replaces all of them with just one. This replacement of all occurrences of similar looking glyphs with a copy of just one often yields a document which remains entirely legible and enables very high compression ratios. Since the compressor just needs to store the coordinates of each of the same looking glyphs rather than the glyphs themselves, each time the output remains perfectly readable, but the amount of information to be stored is significantly reduced. Again, rather than needing to store all of the original pixel information for the whole page, we only need one compressed version of the reference glyph for each character shape and the relative coordinates of all of the places where its copies should be placed. This means that the compression stage treats the output page like a canvas onto which it paints that one copy of the glyph at each of the stored locations.
(01:31:00):
There is one big problem with such a scheme, it's possible for a poor encoder to accidentally get confused and exchange similar looking characters. This explains why the format fell out of favor and became obscure. It does not explained though, why Apple never thought to remove its decompression code deck from their image IO library. Most of Apple's core pdf de coder appears to be Apple's own proprietary code, but the J big two implementation is street from X P D F, whose source code is freely available. This means that the NSO group effectively had the full source code for an complex and not well vetted interpreter to which they were able to provide any amount of data and cause to be invoked on any unsuspecting target's. Iphone. The vulnerability that was found in the code and exploited was a classic integer overflow, which occurs when the code processes a deliberately malformed document containing a J big two compressed image description.
(01:32:33):
This flaw allows the contents of the image to be executed as code, allowing the attacker's total freedom to inject and run any code of their choosing. The only problem is that the messages sent remain on the target on the target's device, and it was the persistence of the attacking code that is on this, on this Saudi individual's phone, which they were able to provide to Citizen's Lab that triggered the unraveling of this entire scheme. Okay. Now, the extent to which the N s O group went in their implementation of this vulnerability is somewhat astonishing because the, the rendering of this was sandboxed by I can't remember the name of it blockade or something that, that Apple has that that sandboxes this. So they needed a sandbox escape, and doing that is what upped the ante for this entire attack. Since replacing all of an images text with identical duplicate versions of just one master reference character will result in an inherently lossy compression, right?
(01:33:59):
Because the decompressed image that is, you know, the, the reconstructed essentially image will not be identical to the original, right? Because one instance of e the character e has been used everywhere, so it's close, but it's not identical. So there was an additional mode added to J Big two to allow for lossless compression. An error mask would be created to represent the difference between the original image and the lossy super compressed image. And it turned out that this error mask was not that large either. However, this capability, the capability of an error mask gave the decompressor the ability to perform exor operations. Since the mask was an exor mask, which was able to flip individual bits in the image as needed to make the final output identical to the original input. This meant that the Decompressor interpreter had access to and or X or and X nor logical operations.
(01:35:26):
And it turns out that given those four operations, any computable function can be computed. It is, as we say, touring complete. J big two does not itself have scripting capabilities, but when combined with a vulnerability, which they found, it does have the ability to emulate circuits of arbitrary logic gates operating upon arbitrary memory. So these genius attackers must have thought, okay, why not just use that to build an entire computer architecture from scratch and script it? And believe it or not, this is exactly what the N S O group's forced entry exploit does by using over 70, 70 0 thousand, 70,000 J big two interpreted segment commands defining logical bit operations, they defined, they essentially built an entire small computer architecture with features such as registers and a full 64 bit adder and comparator, which they then use to search the iPhone's memory to perform arithmetic operations. It's not as fast as JavaScript, but who cares? It's fundamentally computationally equivalent. Okay, so here's what the Project Zero guys wrote to describe their amazement and their reactions to what they discovered once they had reverse engineered this exploit <laugh>, they wrote the bootstrapping operations for the Sandbox Escape exploit are written to run on this logic circuit, and the whole thing runs in this weird em emulated environment created out of a single decompression pass through a J big two stream. It's pretty incredible, and at the same time, pretty terrifying.
(01:38:01):
So from what I've just described, it's clear why the Project zero guys who were, you know, they're immersed in and live this sort of stuff day and night, they've seen it all. Nevertheless, they've never seen anything like this. They described this as the single most sophisticated attack they had ever encountered. On the one hand, it amazed them as it would anyone, and it also terrified them to think that there are people out there somewhere who are not only willing to go to these lengths, but who have the capability to do so. This is a tour de force in fundamental computer science. These people built a working emulation of a 64 bit computer replete with registers and math capability out of the pixels being manipulated by a j big two image decompressor. You know, and impressive as this is as an example of astonishing computational mastery, it's also a tragedy that the entire goal of this effort, the sole purpose, was to subvert iPhones belonging to journalists and human rights defenders for the purpose of illegally spying on their actions and communications.
(01:39:32):
It really seems a shame for such talent and capability to be spent towards such an end. Yeah, John just whispered in my ear a very, you know, very tr you know truth, that the purpose also was to sell the tools to people who wanted to do that. So it's finding something that is a value good point for others, right? <Laugh>. Very, very good point. Yeah, that is fascinating. That is really like remarkable. And like they say, terrifying. Although every, every time I heard you say Jay Big, I was reminded that was my football nickname back in high school, Jay, big <laugh>. No, not really. I didn't even play football, but but it could have been, yeah, that's pretty, that's pretty awesome and and crazy stuff there, Steve. Wow. So, yeah it, I, it just, it's to me, as someone who loves computing, I mean, yeah, thi thi this could be a PhD thesis.
(01:40:30):
This you would be Dr, you know, Abraham or whoever. I mean, if, if you, if you made this thing public, I ho sure hope that whoever did this got a, got a lot of money themselves. I mean, evil as it is because a and that they were appreciated for doing the impossible because and you know, the thing I forgot to add is that this also, this makes you wonder they would not have gone to this length if there was an easier way to skin this particular cat. Yeah, that's a good point. <Laugh>, which suggests, my God, the bar has been raised right by what Apple, by all of the, all of the, the security infrastructure that, that, that Apple has managed to cram into the iPhone. If this is what you have to do to get there, then they've done a pretty darn good job.
(01:41:20):
Boy. And you know, as you, as you've said many, many times on this show, there is no perfect security, right? Any system. I think at some point there is some way in, it's just a matter of finding it, it turns out, in this case like you, you gotta go through to great lengths, but it's, it really is remarkable what they were able to accomplish to make that happen. Where there's a will, there's a way. Wow. Yeah. Pretty incredible. Well, Steve, thank you so much for breaking that down. This and all the news and every single week, weekend, week out, all the security news. That's what Steve is great at putting it into terms that you and I could understand, because sometimes these stories, if I was to just read the article, you know about this, I'd be lost. But thanks to Steve breaking it down I have a better understanding of what's exactly going on here.
(01:42:10):
And if you find yourself in the same position and you wanna support Steve in everything that he's doing, go to grc.com. That's where you can find all the things that Steve is up to. Spin write, of course you can find audio and video of this show over there as well as transcripts. The only place you can find transcripts of the show so you can find the transcripts there, grc.com. If you wanna find security now on our site, well, you can do so. Twit.Tv / sn, the audio and the video and the feeds and everything are there as well. So we've got 'em going in all different directions. We record this show live every Tuesday 4:30 PM Eastern, 1:30 PM Pacific, that's 2030 utc. And if you go to twit.tv slash live, while we're recording, you can be part of the chat room.
(01:43:03):
Either our, either the IR/t room or the Discord, which is part of club twit twit.tv/club twit. We have the members only Discord. We've got our ad free podcast, all of our shows with no ads included. And then our TWI plus podcast content, which is just extra shows, bonus content pre and post show discussions, all this stuff in a feed that only you have access to as a member of the club. So that's $7 a month twit.tv / club twit. But Steve, I wanna give you a big thank you for the last couple of weeks getting the chance to hang out with you. Leo is gonna return next week, so next week's episode of security. Now you are going to share the stage with Leo Laport, sir, and I just appreciate the opportunity back, back, back in the traditional Leo office. That's right, <laugh>. A little bit of a location change, but it's always my pleasure to be able to do this with you, Steve, thank you so much. Really appreciate you Jason. Thank you very much. It's been a pleasure working with you <laugh> and with aunt on the first of the three weeks. That's right. And that's right. We'll let every, we'll see everybody next week. All right, sounds good. We'll see you next week on security now. Ah, bye everybody.
Ant Pruitt (01:44:17):
Hey, what's going on everybody? I am Ant Pruitt and I am the host of Hands-On Photography here on twit.tv. I know you got yourself a fancy smartphone, you got yourself a fancy camera, but your pictures are still lacking. Can't quite figure out what the heck shutter speed means. Watch my show. I got you covered. Wanna know more about just the ISO and exposure triangle in general. Yeah, I got you covered. Or if you got all of that down, you want to get into lighting, you know, making things look better by changing the lights around. I got you covered on that too. So check us out each and every Thursday here on the network. Go to twit.tv/hop and subscribe today.